Thinking about a risk assessment can feel overwhelming, but it really boils down to five core stages: scoping what you need to protect, identifying the dangers, analyzing the potential damage, creating a remediation plan to fix it, and then keeping a watchful eye through continuous monitoring. This structured approach takes a huge, intimidating task and turns it into a clear, manageable roadmap for protecting your business.
Your Starting Point for an Effective Risk Assessment
Let's be honest, the phrase "risk assessment" sounds like a dry, formal process you just have to get through. But if you see it as just a compliance checkbox, you're missing the entire point. A good assessment is less about ticking boxes and more about building a smart, strategic defense for your company.
It's how you uncover your real weaknesses before they get exploited. This allows you to put your time, money, and effort where they'll have the biggest impact, rather than just scrambling to put out fires after the damage is done.
This guide is designed to strip away the confusing jargon and give you practical, actionable steps that any business, regardless of size, can follow.
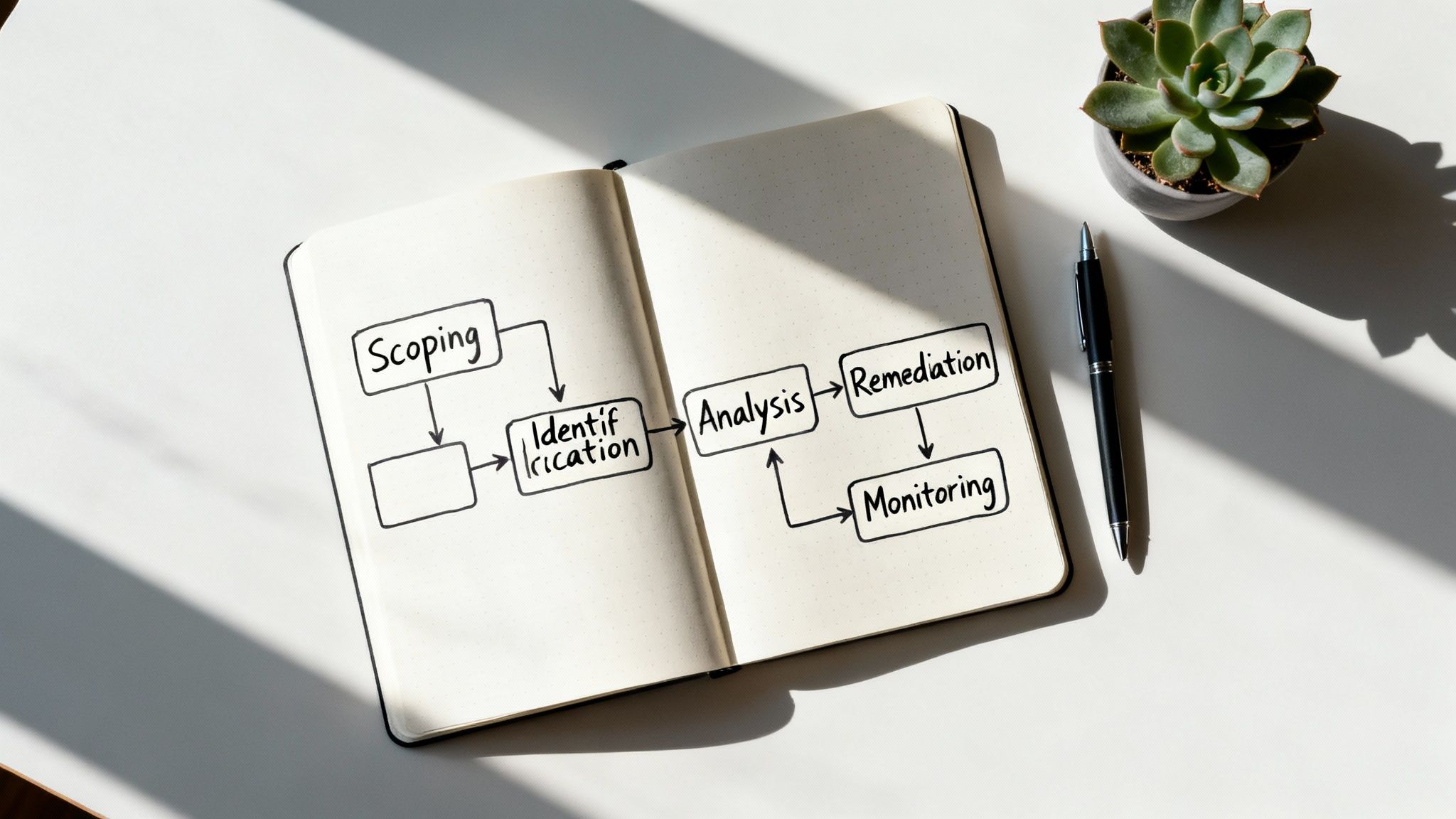
To really get a handle on the process, it helps to see it as a continuous cycle. Each stage feeds into the next, creating a repeatable framework for managing uncertainty and protecting what matters most. We'll break down the entire journey, but here's a quick look at the five core stages we'll cover.
The 5 Core Stages of a Risk Assessment
This table gives you a bird's-eye view of the entire process, from setting boundaries to staying vigilant over the long term.
| Stage | Primary Goal | Key Activities |
|---|---|---|
| Scoping | Define the boundaries and focus of the assessment. | Identify critical assets (data, systems, people), business processes, and compliance requirements to include. |
| Identification | Discover potential threats and vulnerabilities. | Brainstorm threat scenarios (e.g., ransomware), find system weaknesses (e.g., outdated software), and review past incidents. |
| Analysis | Prioritize risks based on potential business impact. | Score the likelihood and impact of each identified risk, often using a risk matrix to visualize priorities. |
| Remediation | Develop a plan to address high-priority risks. | Decide on risk treatment: mitigate (fix it), transfer (insure it), accept (live with it), or avoid (stop the activity). |
| Monitoring | Ensure controls remain effective over time. | Continuously track security metrics, conduct regular vulnerability scans, and schedule periodic reassessments. |
Mastering these stages provides a solid foundation for any risk management program.
This is especially critical for organizations in regulated fields. For healthcare providers, for instance, the entire process hinges on conducting a risk analysis under the HIPAA Security Rule to protect patient data. Ultimately, this proactive mindset is a core reason we always stress the importance of cybersecurity for growing businesses.
Defining Your Battlefield with Scoping and Preparation
Before you can even think about tackling a single risk, you have to draw a map of your battlefield. This initial scoping and preparation phase is where so many risk assessments go wrong. They either end up too narrow, creating dangerous blind spots, or they're so broad that they become unmanageable and lose steam almost immediately. Getting this right from the start is critical.
A poorly defined scope means wasted time and energy. Think of it like trying to secure a building without knowing where the valuables are. You'd end up putting the same heavy-duty lock on the janitor's closet as the server room—a terrible use of resources that leaves your most important assets vulnerable.
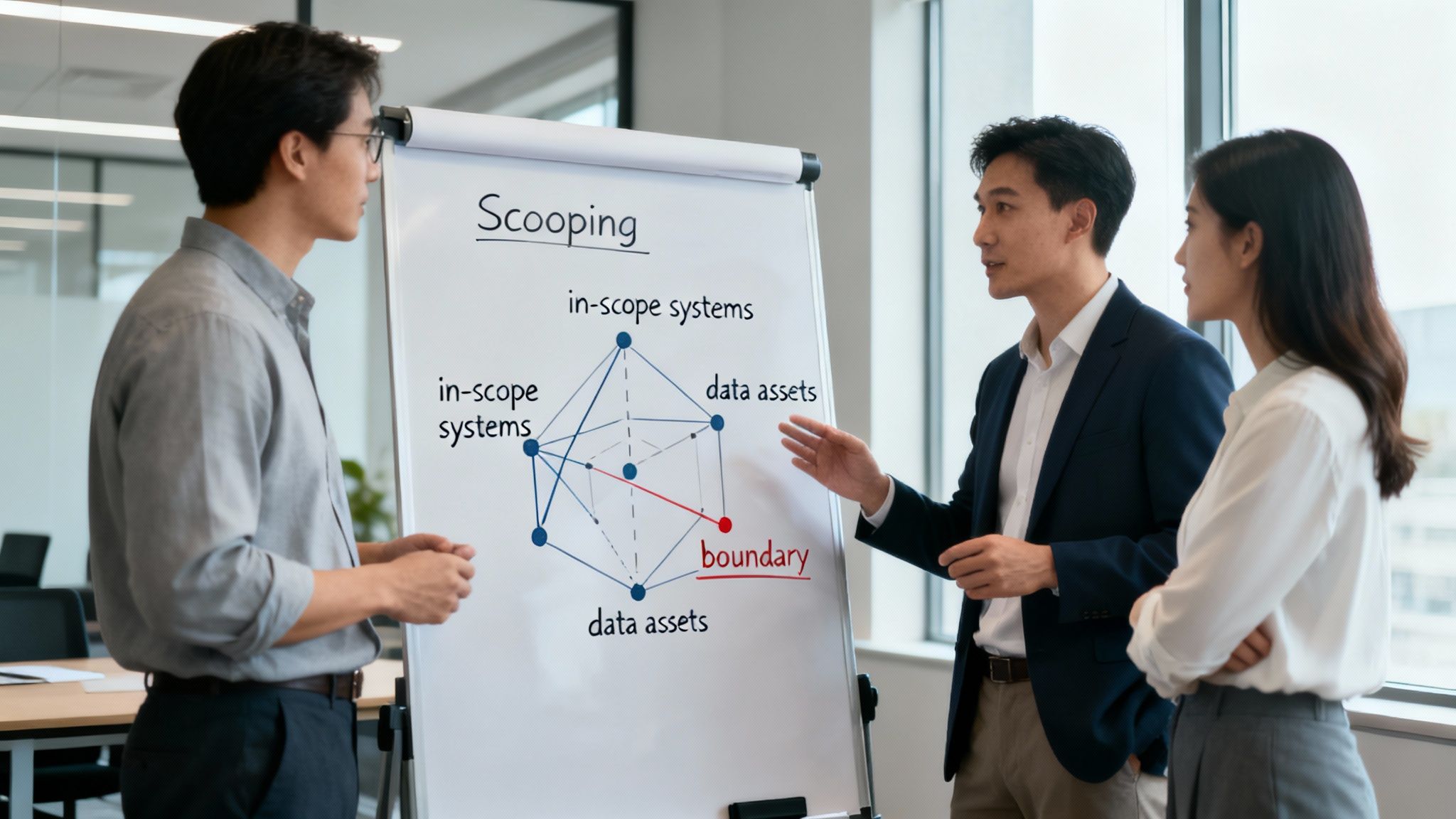
The whole point of scoping is to clearly define what’s "in" and what’s "out." This isn't just about servers and software; it's about business units, physical locations, critical data, and even specific people. A tight scope focuses your efforts where they'll have the biggest impact.
Assembling Your Team and Getting Buy-In
Running a risk assessment with just the IT team is a recipe for an incomplete picture. Real business risk doesn't live in a silo—it cuts across every department, and your team needs to reflect that. You'll want a cross-functional group that brings different perspectives to the table.
Your core team should have people from:
- IT and Security: These are your technical experts. They know the infrastructure, the software, and the security controls you already have in place.
- Operations: These folks understand the day-to-day workflows and how the business actually runs, not just how it looks on a flowchart.
- Leadership/Management: You need a champion who can provide strategic direction and make sure the project gets the resources it needs.
- Legal and Compliance: If you're dealing with regulations like HIPAA or financial rules, you absolutely need their expertise.
Once the team is in place, the real work begins: getting genuine buy-in from leadership. This is more than just a signature on a project charter. It's about communicating the "why" and showing them this isn't just another IT task, but a strategic move to protect the entire organization.
A risk assessment without executive support is destined to become a report that gathers dust. When leaders understand the potential business impact of identified risks, they are far more likely to approve the resources needed for remediation.
For a smaller business, your "team" might just be a couple of key people, but the principle is the same. Pull in people who see different parts of the operation. You might find that partnering with an outside firm for managed IT and cybersecurity services can fill critical gaps, especially for lean teams in complex industries. You can learn more about why San Antonio businesses need managed IT and cybersecurity services to see how that kind of partnership works.
Building a Comprehensive Asset Inventory
You can't protect what you don't know you have. That’s why an asset inventory is the bedrock of any credible risk assessment. Unfortunately, a lot of companies stop at a simple list of laptops and servers. A real inventory has to go much, much deeper.
It needs to document everything that holds value for your business. Think beyond the hardware and start listing anything that, if it were compromised, would hurt your operations, your finances, or your reputation.
A solid asset inventory should track:
- Hardware: Servers, laptops, workstations, mobile devices, and all the networking gear that connects them.
- Software: Operating systems, business applications (both on your own servers and in the cloud), and databases.
- Data: This is often your most critical asset. You need to classify it by sensitivity—think customer PII, patient health records (ePHI), financial data, and intellectual property.
- People: Who are the key personnel with access to your most sensitive systems?
- Facilities: Don't forget physical locations like your office, data centers, or storage sites.
- Third-Party Vendors: Any partner with access to your network or data is an extension of your attack surface and belongs on this list.
A Real-World Scoping Example
Let's look at a midsize healthcare provider. They need to run a risk assessment to stay compliant with HIPAA. A rookie mistake would be to just focus on their Electronic Health Record (EHR) system.
A properly scoped assessment, however, looks at the whole picture:
- Systems in Scope: The EHR, yes, but also the patient scheduling software, the billing platform, the internal email server, and the cloud service used for backups.
- Data in Scope: All electronic Protected Health Information (ePHI), patient financial records, and internal employee data.
- People in Scope: Every clinician, the administrative staff with system access, and the third-party IT provider that manages their network.
- Locations in Scope: The main clinic, any satellite offices, and the offsite data center where their servers live.
By drawing these lines clearly at the beginning, the healthcare provider can run a focused, effective assessment. They know exactly which systems to test, whose access rights to audit, and which data flows to map out. This clarity prevents the whole process from derailing before it even starts. That map is the first—and most important—step toward becoming a secure and compliant organization.
Uncovering Your Real Threats and Vulnerabilities
Now that you have a map of your assets and a team ready to go, the real detective work begins. This is where we pinpoint the specific dangers that could disrupt your business. To get this right, it’s crucial to understand two concepts that people often mix up: threats and vulnerabilities.
Let's use a simple analogy. Think about securing your home.
A threat is the burglar casing the neighborhood. It’s an external (or even internal) force that could cause harm. A vulnerability, on the other hand, is the unlocked back window. It’s the specific weakness that lets the threat in.
You can’t control the existence of burglars, but you can absolutely control whether your windows are locked. It’s the same in business. You can’t eliminate every cyber threat, but you can find and fix the vulnerabilities they prey on. The goal here is to get a complete picture of both.
Practical Methods for Finding Threats
Identifying threats means looking both outside and inside your company walls. You need to get a handle on the dangers trying to get in and the risks that are already part of your operations. This process is part science, part creative thinking.
Here are a few proven ways to start digging:
- Structured Brainstorming: Get your team in a room and ask a simple question: “What could go wrong?” Let everyone run with it. Think through scenarios from a targeted ransomware attack to what would happen if a key employee quit without notice.
- Analyze Past Incidents: Your own history is a goldmine. Dig through old helpdesk tickets, security incident reports, and even notes from past outages. What was the root cause? Could it happen again?
- Use Threat Intelligence: You don’t have to guess what attackers are up to. Subscribing to threat intelligence feeds from sources like CISA or private security firms gives you real-time data on active campaigns targeting your industry.
Identifying Your Hidden Vulnerabilities
With a list of potential threats in hand, you can start hunting for the vulnerabilities they might exploit. And remember, vulnerabilities aren't just technical glitches. They can be weak points in your processes, your physical security, or even your company culture. A thorough search covers all these bases.
A common mistake is focusing only on technical flaws like unpatched software. The truth is, your biggest vulnerability is often a business process that relies on a single person or a major gap in employee security training.
To uncover these weak spots, try these approaches:
- Technical Scanning: Tools like vulnerability scanners can automatically check your networks and systems for known software flaws, misconfigurations, and missing patches.
- Process Walkthroughs: Sit down with department heads and literally map out their critical workflows on a whiteboard. Where are the single points of failure? What happens if a key system goes offline for an hour?
- Employee Interviews: Talk to the people on the front lines. They know the real-world shortcuts and security gaps better than anyone, even if those issues aren't written down in any official manual.
As part of identifying these potential weaknesses, it's also smart to get an outsider's perspective on what attackers can see. This is where conducting an online digital footprint check comes in. It helps reveal how much sensitive information about your company and staff is already publicly available for anyone to find and exploit.
Thinking in Real-World Scenarios
Let's put this all together with a practical example. Imagine a small financial advisory firm.
- Threat: A sophisticated phishing email impersonating a senior partner, demanding an urgent wire transfer.
- Vulnerability 1 (Human): Employees haven't had any practical security awareness training in over a year and don't know how to spot and report modern phishing attempts.
- Vulnerability 2 (Process): The firm's policy for wire transfers doesn't require out-of-band, multi-person verbal verification for large sums.
- Vulnerability 3 (Technical): Their email filtering system is a basic, off-the-shelf tool that consistently fails to flag emails with spoofed sender addresses.
See how that works? In one simple scenario, we've found significant weaknesses across people, processes, and technology. This is the level of detail you need to truly understand your risk.
This proactive approach is becoming the new standard. Organizations are moving beyond simple compliance checklists and embracing a more strategic mindset. The BDO Global Risk Landscape Report 2025 found that 78% of companies now conduct risk assessments at least quarterly—a big jump from just 65% in 2020. What’s more, 82% of organizations now use frameworks that pull in both internal and external data, like market trends and regulatory changes, to shape their strategy. This data-driven, holistic view is exactly what you need to uncover the most impactful risks before they turn into real incidents.
Analyzing and Scoring Risks for True Prioritization
So you’ve gone through the process of identifying threats and vulnerabilities, and now you’re staring at a massive, and frankly, intimidating list. It’s a common roadblock. Seeing every possible thing that could go wrong written down in one place can be paralyzing. But this raw list isn’t the end goal; it’s the starting point.
The next step is to bring some context to this chaos. We need to figure out which of these potential disasters actually warrants your immediate attention and budget. This is where risk analysis comes in, and it's simpler than you might think. We're going to transform that list into an organized, prioritized action plan by asking two fundamental questions for every single risk you've identified:
- How likely is this to actually happen?
- What’s the real-world business impact if it does?
Answering these two questions allows you to score and rank everything, turning an overwhelming spreadsheet into a powerful tool for making smart, defensible decisions.
The Power of Likelihood and Impact Scoring
The idea here is to assign a number to both likelihood and impact, usually on a simple 1-to-5 scale. We're not aiming for mathematical perfection; the goal is to create a consistent framework for comparing completely different types of risks against one another.
- Likelihood: This is your educated guess on probability. Is an event almost certain to happen this year (a 5), or is it so rare it’s barely a consideration (a 1)? You’ll base this on past incidents, what’s happening in your industry, and how effective your current security controls are.
- Impact: This measures the damage. Would it be a minor hiccup with almost no financial loss (a 1), or would it be a catastrophic, company-ending event (a 5)?
This isn't just some internal exercise; it's a structured standard used at the highest levels. The World Economic Forum’s 2025 Global Risks Report gathered insights from over 900 experts who ranked global threats using this exact methodology. Cyber risk came out on top, with over 70% of respondents identifying it as a critical danger. This just goes to show how relevant this simple scoring system is.
This chart shows a few of the common ways we gather the initial data for this kind of analysis.
As you can see, a healthy mix of brainstorming with your team, digging into system logs, and keeping an eye on external threat intelligence gives you a solid foundation.
Once you have your scores, you can calculate an overall risk rating, typically just by multiplying the two numbers. For example, a risk with a likelihood of 4 and an impact of 5 gets a score of 20. This immediately stands out as a much higher priority than a risk with a likelihood of 2 and an impact of 3 (which scores a 6).
Visualizing Priorities with a Risk Matrix
Multiplying numbers is a good start, but the real "aha!" moment comes when you visualize the data on a risk matrix, sometimes called a heat map. It’s a simple grid that plots likelihood on one axis and impact on the other, instantly showing you where the danger zones are.
Here is a typical example of what a 5×5 risk matrix looks like.
Sample Risk Matrix Example
| Likelihood ↓ / Impact → | 1 (Insignificant) | 2 (Minor) | 3 (Moderate) | 4 (Major) | 5 (Catastrophic) |
|---|---|---|---|---|---|
| 5 (Almost Certain) | Medium | Medium | High | Critical | Critical |
| 4 (Likely) | Low | Medium | High | High | Critical |
| 3 (Possible) | Low | Medium | Medium | High | High |
| 2 (Unlikely) | Low | Low | Medium | Medium | High |
| 1 (Rare) | Low | Low | Low | Medium | Medium |
The result is a color-coded chart that makes your priorities impossible to ignore.
- Red (High/Critical Risk): These are the threats in the top-right corner—high likelihood, high impact. They demand immediate action plans.
- Yellow (Medium Risk): These are risks that need to be managed and monitored closely. You'll need a mitigation plan, but it might not be a five-alarm fire like the red items.
- Green (Low Risk): With low likelihood and/or impact, these are risks you might formally decide to "accept" for now, while still keeping an eye on them.
A risk matrix does more than just display data; it tells a story. It lets executives and technical teams speak the same language. You can point to a box and instantly agree on severity without getting bogged down in jargon.
Scenario: A Financial Services Firm in Action
Let's make this real. Picture a midsize financial services firm working through their assessment. They’ve identified two key risks:
- Risk A: A Ransomware Attack. They score the likelihood as a 4 (very likely, given the constant attacks on their industry) and the impact as a 5 (catastrophic, as it would lock up client data and halt operations). The total risk score is 20.
- Risk B: Office Theft of a Laptop. They score likelihood as a 2 (unlikely, thanks to good physical security) and impact as a 3 (moderate, because the laptop is encrypted, but a data breach is still possible). The total risk score is 6.
When they plot this on their matrix, the ransomware attack lands squarely in the red "Critical" quadrant. The stolen laptop probably falls somewhere in the yellow or green area. This instantly shows the firm's leadership where to focus their cybersecurity budget and resources first. It’s not that a stolen laptop isn't a problem, but the ransomware threat is an existential one that needs to be dealt with now.
Building Your Actionable Remediation Plan
An analysis that just sits on a shelf is useless. Now that you’ve got a risk matrix staring you in the face, clearly pointing out your priorities, it's time to turn those findings into a documented, concrete plan. This is where you pivot from simply understanding your risks to actively wrestling them into submission. A solid plan ensures everyone knows what they're supposed to do, deadlines are clear, and your decisions will hold up under scrutiny from auditors, execs, or regulators.
For every risk you’ve uncovered—especially the ones glowing red in the "High" and "Critical" boxes—you really only have four ways to handle it. Choosing the right one is a business decision, not just a technical one.
Choosing Your Risk Treatment Strategy
The path you take depends on the risk's potential damage, how much the fix will cost, and your company's overall appetite for risk. Let's walk through the options.
-
Mitigate: This is your go-to strategy most of the time. You roll out new controls or tighten up existing ones to knock down the risk’s likelihood or its potential impact. A perfect example is deploying multi-factor authentication (MFA) to shut down the risk of a simple password breach.
-
Transfer: With this one, you’re essentially offloading the financial fallout of a risk onto someone else. The classic move here is buying a cybersecurity insurance policy to cover the hefty costs of a potential data breach.
-
Accept: For those nagging, low-level risks where the cost of fixing them is more than the damage they could ever do, you might consciously decide to just live with it. The key here is that this has to be a formal, documented decision—not just you ignoring the problem and hoping for the best.
-
Avoid: Sometimes, the only sensible move is to get out of the game entirely. If a creaky old legacy application is riddled with unpatchable holes, you might just have to pull the plug, decommission it, and move to a more secure alternative.
Documenting your risk treatment decisions is absolutely non-negotiable. It doesn't matter if you mitigate, transfer, accept, or avoid a risk; you need a clear paper trail explaining why you made that call, who signed off on it, and when. This audit trail is gold during compliance checks and strategic reviews.
A Framework for Prioritizing Action
Your risk matrix is your roadmap. The rule is simple: start at the top right corner (Critical) and work your way down and to the left. For each of those high-priority risks, your remediation plan needs to nail down a few key details.
Key Components of a Remediation Task
- Risk Owner: Pin this on a specific person, not a department. You need one individual who is ultimately accountable for seeing the fix through to the end.
- Specific Action: Get granular. "Improve server security" is useless. "Deploy endpoint detection and response (EDR) software on all production servers" is an actionable task.
- Timeline: Set a realistic but firm deadline. This injects a sense of urgency and gives you something to measure progress against.
- Resources Needed: What will it take to get this done? Spell out the budget, tools, or people required.
This structured approach is what turns a list of problems into a genuine project plan. Taking these proactive steps is what resilience is all about. In fact, the United Nations Office for Disaster Risk Reduction has found that investments in risk reduction can yield a benefit-cost ratio of up to 4:1 in certain regions. In other words, every dollar you spend today could save you up to four dollars in future losses. You can read more about the findings of the UNDRR Global Assessment Report.
Putting It All Together: A Practical Example
Let's go back to that law firm that discovered a critical vulnerability in its client portal. The risk is a data breach exposing sensitive case files—a catastrophic impact (5) with a possible likelihood (3). That puts it squarely in the "High" risk zone on their matrix.
Here’s how they could build out their remediation plan:
- Risk: Unauthorized access to client portal data via a software vulnerability.
- Treatment Strategy: Mitigate.
- Risk Owner: Jane Doe, Head of IT.
- Action Items:
- Immediately apply the vendor's security patch to the portal software.
- Hire a third-party firm to conduct a penetration test to confirm the fix worked and hunt for other weaknesses.
- Implement a web application firewall (WAF) to add another layer of defense.
- Timeline: Patch to be applied within 24 hours. Penetration test scheduled within 2 weeks. WAF implementation project to be completed within 60 days.
This is the kind of detail that makes a plan real and actionable. For organizations that don't have this kind of expertise in-house, bringing in a partner for managed cybersecurity services can be a smart and effective way to execute complex fixes like these.
Answering Your Top Questions About Risk Assessments
When you're first getting started with this process, a few practical questions always pop up. It's completely normal. Getting clear, straightforward answers is the best way to keep things moving and get everyone on the same page. Let's dig into some of the most common ones I hear.
How Often Should We Be Doing This?
Lots of people aim for an annual risk assessment, which is a great start. But thinking of it as a once-a-year checkbox item is a huge mistake. The best way to approach this is to treat your assessment as a living, breathing document that changes right along with your business.
A full, top-to-bottom reassessment should happen any time there's a major shift. Maybe you're rolling out a new ERP system, going through a merger, or making a big pivot in your business model. These are all perfect triggers. Meanwhile, you should be continuously monitoring your most important controls—that's a daily habit, not a year-end fire drill. And if you're in a regulated field like healthcare or finance, rules like HIPAA might set a minimum frequency for you anyway.
The real key is to let the rhythm of your business drive the process, not just the calendar. Honestly, an outdated risk assessment can be more dangerous than having none at all because it gives you a false sense of security.
What's the Difference Between a Risk Assessment and a Vulnerability Scan?
This is easily one of the most common points of confusion I run into, but the difference is critical.
Think of it like this: a vulnerability scan is a technical tool that hunts for potential security weaknesses. It’s like an automated gadget that rattles every door and jiggles every window in your building to see if any are unlocked. It spits out a technical list of potential flaws.
For example, a scan might tell you about:
- Outdated software that has known security holes.
- Cloud storage buckets that were accidentally set to be publicly accessible.
- Weak or default passwords still active on your network gear.
A risk assessment, on the other hand, is the strategic thinking that puts those technical findings into a business context. It takes that list of unlocked windows from the scan and asks the important questions: Which unlocked window leads to the server room with all our customer data? How likely is it that a burglar is even in our neighborhood? What's the real financial and reputational cost if they get inside and steal something?
In short, a scan finds the holes. An assessment tells you which ones to fix first based on how badly they could hurt your business.
Should We Do This Ourselves or Hire an Expert?
Deciding whether to run your risk assessment internally or bring in an outside expert really comes down to your team's skills, time, and budget. There are real pros and cons to each path.
Doing it in-house can definitely save money and is a fantastic way to build up your team's security knowledge and sense of ownership. This approach can work really well if you have people on staff who genuinely understand IT, security, and compliance. The main risk, though, is that you can be blind to your own faults. That "we've always done it this way" mindset can easily gloss over hidden risks.
Hiring a third-party expert gives you a fresh, unbiased perspective. These folks live and breathe risk management every single day, so they’re on top of the latest threats and tricky compliance rules. For companies in heavily regulated industries, those staring down a specific audit, or simply those without a dedicated security team, an external assessment is often the smartest, most thorough choice. It delivers an objective view that executives and auditors tend to put a lot of faith in. The right partner won't just run an audit; they'll give you a strategic roadmap for getting better.
A thorough risk assessment is the bedrock of any resilient security strategy. At Defend IT Services, we help businesses in San Antonio conduct comprehensive assessments that uncover real-world risks and build actionable remediation plans. Move from uncertainty to confidence by visiting us at https://defenditservices.com to learn how our managed IT and cybersecurity services can protect your organization.



