In an era where a single ransomware attack can cripple a small or midsize business, selecting the right defense is no longer optional, it's essential for survival. Attackers are constantly deploying sophisticated techniques that bypass traditional antivirus software, leaving organizations vulnerable to data encryption, operational shutdown, and catastrophic financial loss. With so many solutions promising impenetrable protection, how do you choose the right one for your specific needs?
We've done the heavy lifting for you. This guide dives deep into the 12 best ransomware protection software options available, moving beyond marketing hype to provide a practical analysis of each tool's real-world performance. We examine implementation hurdles and specific use cases relevant to businesses in San Antonio and beyond, from regulated healthcare providers to multi-location companies.
This listicle is designed to be a definitive resource. Inside, you will find detailed reviews, screenshots, and direct links for each platform. Whether you need a fully managed security service, a cloud-native Endpoint Detection and Response (EDR) platform, or a solution that integrates seamlessly with your existing tech stack, you'll find clear, actionable insights here. For a broader perspective on safeguarding your organization in the coming year, consider these Top Cybersecurity Solutions for Small Business. Our goal is to equip you with the information needed to make an informed decision and fortify your business against today's most persistent cyber threats.
1. Why Every San Antonio Business Needs Managed IT and Cybersecurity Services
For businesses seeking a comprehensive, hands-off solution, Defend IT Services offers more than just a software tool; it provides a fully managed cybersecurity and IT framework. This approach is a standout because it combines industry-leading technologies with expert human oversight, creating a multi-layered defense specifically tailored for small and midsize organizations. Instead of purchasing and managing separate software, clients get an integrated security stack designed for robust ransomware protection.
This managed service is built on a powerful combination of Bitdefender for advanced endpoint detection and ThreatLocker for zero-trust application control. This dual-pronged strategy effectively blocks both known malware and unauthorized executables, which are common ransomware attack vectors. The service excels by not just preventing threats but also providing 24/7 monitoring and rapid incident response, which is critical for minimizing operational downtime.
Key Features and Strategic Advantages
- Layered Security Stack: Utilizes a best-in-class combination of Bitdefender for endpoint protection and ThreatLocker for application whitelisting and ringfencing. This prevents unauthorized software from ever running, stopping ransomware before it can execute.
- Proactive Threat Hunting: The service includes continuous, 24/7 monitoring by a dedicated security team. This human element actively searches for and mitigates threats, a capability often out of reach for SMBs managing their own security.
- Tailored Cybersecurity Roadmaps: Defend IT Services conducts in-depth vulnerability assessments and creates customized security plans, ensuring the protection strategy aligns with specific business needs and compliance requirements (e.g., HIPAA).
- Integrated IT Management: Beyond security, the service encompasses managed IT, cloud security, and even managed print services. This holistic approach ensures security is consistently applied across all aspects of the business infrastructure.
Even with advanced ransomware protection, a robust cybersecurity strategy should also include understanding what cyber insurance covers to ensure financial protection in a worst-case scenario.
Practical Use Cases and Implementation
A key benefit is the streamlined implementation process. The Defend IT Services team handles the entire deployment, from initial system audit to configuring policies in Bitdefender and ThreatLocker. For a midsize healthcare clinic, this would mean not only deploying endpoint agents but also creating specific application rules to ensure HIPAA compliance and protect patient data from unauthorized access. The ongoing management and personalized support from this veteran-owned firm are significant advantages, especially for businesses without dedicated IT security staff.
| Feature Analysis | Defend IT Services (Managed) | Standalone Software |
|---|---|---|
| Protection Method | Multi-layered: Prevention, Detection, Response | Primarily Prevention & Detection |
| Management | Fully managed by experts | In-house IT team required |
| Incident Response | Included 24/7 service | Typically a separate service or cost |
| Customization | High (tailored to business needs) | Limited to software settings |
Pros:
- Leverages top-tier security software without the internal management burden.
- Proactive 24/7 monitoring and expert incident response.
- Customized security strategies and compliance support.
Cons:
- Primarily serves businesses in the San Antonio, Texas area.
- Requires an initial onboarding period to integrate with existing systems.
Learn more about their comprehensive managed security approach at defenditservices.com
2. CrowdStrike – Falcon Go/Pro/Enterprise
CrowdStrike is a dominant force in endpoint security, offering enterprise-grade protection scaled for businesses of all sizes through its Falcon platform. Their cloud-native approach means deployment is remarkably fast; you can protect your devices in minutes using a single, lightweight agent that won’t slow down employee workstations. For businesses seeking the best ransomware protection software, CrowdStrike provides a powerful, AI-driven engine that moves beyond simple signature matching to analyze and block threats based on their behavior.
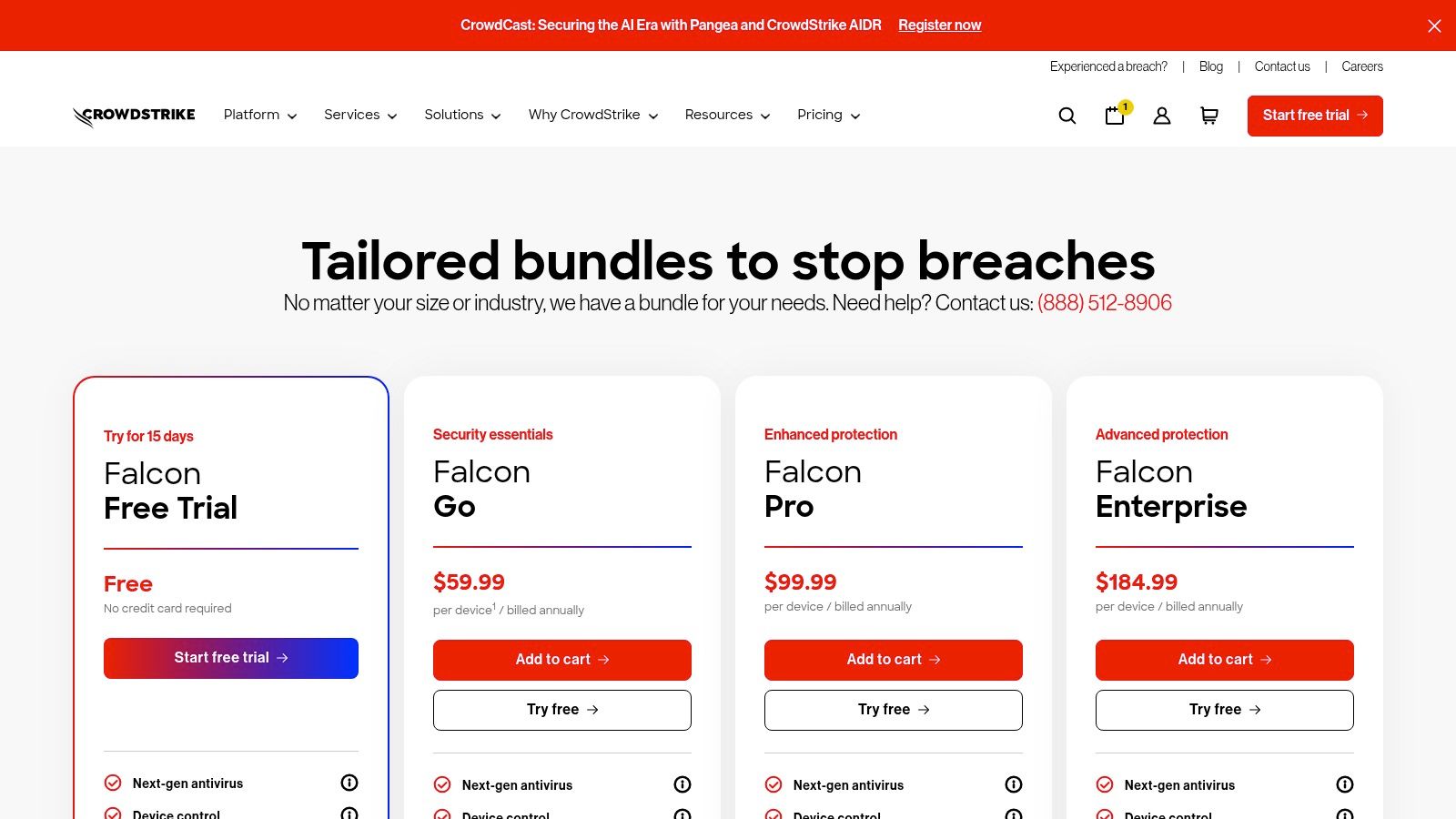
The platform is tiered to meet specific needs, from the SMB-focused Falcon Go to the more advanced Pro and Enterprise bundles. What makes CrowdStrike unique is its transparency; pricing is clearly listed per device on their website, a rarity in the enterprise security space. This allows regulated organizations in finance or healthcare to accurately budget for robust compliance and risk management tools. While billing is annual, their FalconFlex licensing offers some adaptability.
Key Features and Considerations
- Deployment: Cloud-native with a single agent for rapid, low-impact deployment.
- Protection Engine: Utilizes AI-powered Next-Generation Antivirus (NGAV) combined with Endpoint Detection and Response (EDR) to identify and stop sophisticated ransomware attacks.
- Scalability: Tiers like Falcon Go (capped at 100 devices) are ideal for small businesses, while Pro and Enterprise add features like device control and advanced threat hunting for growing teams.
- Pricing: A 15-day free trial is available, with clear annual, per-device pricing listed online. Higher-tier plans include a Breach Prevention Warranty for added assurance.
Website: https://www.crowdstrike.com/en-us/pricing/
3. SentinelOne – Singularity Platform
SentinelOne is renowned in the cybersecurity space for its autonomous, AI-powered Singularity platform, which combines Endpoint Protection (EPP), Detection and Response (EDR), and Extended Detection and Response (XDR) into a single solution. Its standout feature for organizations fighting ransomware is its one-click remediation and rollback capability. This allows businesses hit by an attack to almost instantly reverse unauthorized changes on Windows devices, restoring encrypted files and system settings to their pre-attack state, which is a critical advantage when choosing the best ransomware protection software.
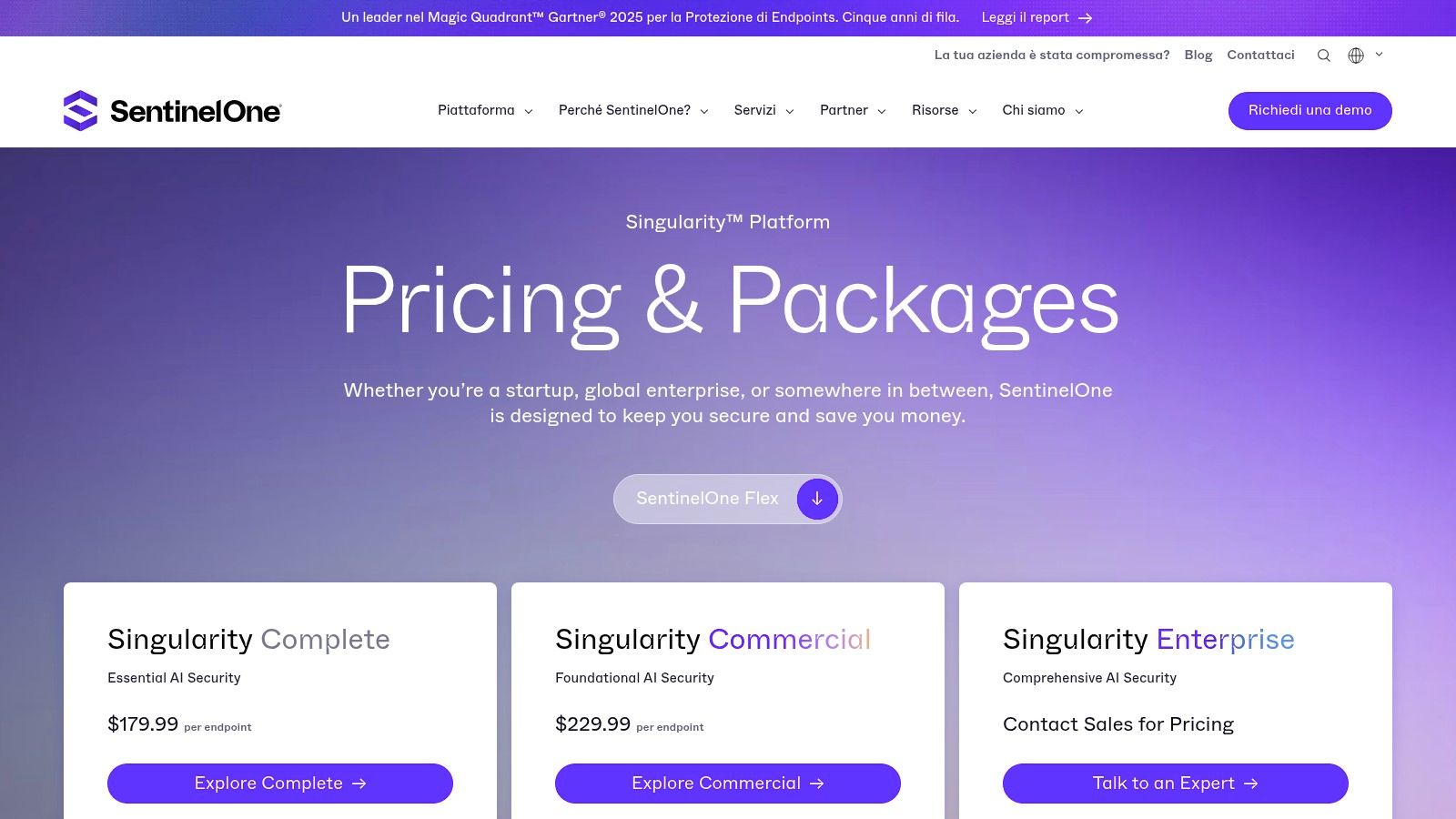
The platform is built on behavior-based detection, allowing it to autonomously identify and neutralize novel threats without human intervention. SentinelOne also expresses strong confidence in its product through a long-standing ransomware warranty program, historically offering up to $1 million in coverage, which provides significant peace of mind for regulated industries like healthcare and finance. While some advanced tiers require a sales consultation, their website offers transparent list pricing for core packages, helping businesses budget effectively.
Key Features and Considerations
- Deployment: A single autonomous agent provides protection across Windows, macOS, and Linux endpoints, as well as cloud workloads.
- Protection Engine: Utilizes patented Storyline technology to track all OS activities, using behavioral AI to detect and stop malicious processes in real-time.
- Ransomware Recovery: The Windows rollback feature can reverse file encryption and system modifications from a ransomware attack with a single click, drastically reducing downtime.
- Pricing: Transparent pricing is available for select packages on their website. A Flex procurement program helps align licensing with business needs, though data retention limits vary by tier.
Website: https://it.sentinelone.com/platform-packages/
4. Microsoft – Defender for Business (SMB) via Microsoft Security
For small and medium-sized businesses already invested in the Microsoft 365 ecosystem, Defender for Business offers an almost unbeatable value proposition. It effectively democratizes enterprise-grade endpoint security, making powerful EDR and NGAV capabilities accessible without the typical complexity or high cost. This solution provides one of the best ransomware protection software options for SMBs by seamlessly integrating with tools they already use, like Microsoft 365 Business Premium and Intune, for centralized management.
The primary advantage of Defender for Business is its automated investigation and remediation engine, which significantly reduces the manual workload on IT teams. When a threat is detected, the system automatically analyzes its scope and applies corrective actions, a feature typically reserved for more expensive, enterprise-focused platforms. Its cross-platform support extends protection beyond Windows to macOS, iOS, and Android devices, ensuring comprehensive coverage for modern, diverse work environments. While it can be purchased standalone, its true power is unlocked when bundled with Microsoft 365, creating a unified security and productivity suite.
Key Features and Considerations
- Deployment: Cloud-managed through the Microsoft Security portal, with deep integration into Microsoft Intune for streamlined policy enforcement and device onboarding.
- Protection Engine: Combines Next-Generation Antivirus (NGAV) with advanced Endpoint Detection and Response (EDR), featuring automated investigation to contain and remediate ransomware threats quickly.
- Scalability: Specifically designed for SMBs (up to 300 users), it can be acquired standalone or as part of the Microsoft 365 Business Premium bundle, offering a clear growth path.
- Pricing: A 30-day free trial is available. Pricing is highly competitive, offered as a low-cost, per-user monthly subscription, making it extremely accessible for small businesses.
Website: https://www.microsoft.com/en-us/security/small-medium-business/pricing
5. Sophos – Intercept X Endpoint and MDR
Sophos is a household name in cybersecurity, and its Intercept X Endpoint platform stands out as some of the best ransomware protection software available, particularly for its specialized anti-ransomware technology. The core of its defense is CryptoGuard, which actively monitors for malicious encryption processes from both local and remote sources. If ransomware activity is detected, CryptoGuard not only halts the attack but can automatically roll back any affected files to their pre-encrypted state, significantly reducing downtime and data loss.
Managed through the cloud-based Sophos Central console, Intercept X provides a unified view of endpoint security across an entire organization. For businesses that need an extra layer of defense without hiring a dedicated security team, Sophos offers a Managed Detection and Response (MDR) service. This provides 24/7 expert monitoring and rapid incident response, a crucial service for organizations in highly regulated fields. While most pricing is quote-based, this allows for customized solutions that fit specific business needs, a strategy often employed by trusted IT partners like those who provide managed cybersecurity in San Antonio.
Key Features and Considerations
- Deployment: Cloud-managed via the Sophos Central console, simplifying administration for multi-location businesses.
- Protection Engine: Utilizes deep learning AI combined with CryptoGuard anti-ransomware technology and an automatic file rollback feature to neutralize threats.
- Scalability: The platform scales from basic endpoint protection to full Extended Detection and Response (XDR) and a 24/7 Managed Detection and Response (MDR) service.
- Pricing: A 30-day free trial is available. Full pricing is generally provided by quote through Sophos partners, ensuring a tailored security package.
Website: https://www.sophos.com/en-us/content/ransomware-attacks
6. Bitdefender – GravityZone (Small Business to Enterprise)
Bitdefender is consistently recognized by independent testing labs for its exceptional malware and ransomware detection rates, making its GravityZone platform a top contender. It offers a prevention-first security approach, combining Endpoint Protection (EPP), Detection and Response (EDR), and Extended Detection and Response (XDR) into a unified console. For businesses looking for the best ransomware protection software with proven efficacy, Bitdefender’s layered defense and ransomware mitigation capabilities are a powerful choice.
One of Bitdefender's strengths is its accessibility for small to midsize businesses. The GravityZone Small Business Security plan can be purchased directly online, offering clear pricing and a streamlined setup process. The platform is highly modular, allowing organizations to add critical security layers like patch management, full disk encryption, and email security as needed. While enterprise-level licensing typically requires engaging with a partner, interactive demos and free trials are available across the board, giving teams a chance to evaluate the platform’s robust capabilities firsthand.
Key Features and Considerations
- Deployment: Cloud or on-premise deployment options with a single agent for endpoint management.
- Protection Engine: Employs advanced machine learning, behavioral analysis, and anti-exploit technology to block fileless attacks and sophisticated ransomware. Features ransomware mitigation with automatic file rollback.
- Scalability: Clear product tiers for small businesses available online, with more comprehensive EDR/XDR packages for growing enterprises and Managed Service Providers (MSPs).
- Pricing: Free trials and interactive demos are available. Small business plans are sold online with transparent per-device pricing, while enterprise pricing requires a quote.
Website: https://www.bitdefender.com/en-us/business/products/gravityzone-small-business-security
7. Trend Micro – Trend Vision One Endpoint Security / Apex One
Trend Micro offers a mature, enterprise-grade endpoint suite that delivers comprehensive threat defense for businesses needing deep, granular control. Its platform, centered around Trend Vision One with Apex One for endpoints, provides some of the best ransomware protection software by integrating predictive machine learning with real-time behavior monitoring. This multi-layered approach is designed to detect and block fileless malware and encryption routines before they can execute and cause damage.
What sets Trend Micro apart is its powerful policy-driven engine and broad XDR (Extended Detection and Response) capabilities. Administrators can define precise mitigation rules that automatically quarantine suspicious files and terminate malicious processes. Furthermore, its XDR platform connects security data from endpoints, email, servers, and cloud workloads, providing a unified view of an attack chain. This comprehensive visibility is crucial for understanding the importance of cybersecurity for growing businesses and stopping sophisticated threats that traverse multiple environments. While pricing isn't public, requiring interaction with sales or a partner, the depth of its feature set makes it a strong contender for organizations with complex security needs.
Key Features and Considerations
- Deployment: Flexible deployment options including SaaS, on-premises, or as a managed service to fit different IT infrastructures.
- Protection Engine: Utilizes predictive machine learning, behavior analysis, and virtual patching to block ransomware and other advanced threats before they impact endpoints.
- Scalability: The Trend Vision One platform offers extensive XDR and cross-layered detection, making it highly scalable for businesses integrating endpoint, cloud, and network security.
- Pricing: A free trial is available upon request, but detailed pricing requires contacting the sales team or a channel partner.
Website: https://www.trendmicro.com/en_us/business/products/endpoint-security.html
8. ESET – ESET PROTECT Complete (Business)
ESET is a long-standing name in cybersecurity, known for its lightweight yet powerful endpoint protection solutions. The ESET PROTECT Complete tier is specifically packaged for businesses needing multilayered defenses against sophisticated threats, including ransomware. It combines traditional endpoint security with advanced tools like full-disk encryption, patch management, and cloud application security, making it one of the best ransomware protection software options for organizations looking for a comprehensive, all-in-one suite.
What makes ESET particularly attractive for SMBs is its balance of performance and features. The agent has a minimal system footprint, ensuring employee productivity isn't impacted. Their licensing model is also highly flexible, allowing businesses to mix and match protection tiers for different user groups, which is a significant advantage for budget-conscious companies. While pricing is customized based on device count, their U.S. website offers a straightforward cart and checkout process once you input your needs, often featuring promotions for new customers.
Key Features and Considerations
- Deployment: Cloud-based or on-premises management console with a lightweight agent for endpoints, mobile devices, and file servers.
- Protection Engine: Employs advanced threat defense, machine learning, and a cloud-based reputation system to detect and block fileless malware and zero-day ransomware attacks.
- Scalability: The platform is built to scale from small offices to large enterprises, with add-ons for Managed Detection and Response (MDR) and Extended Detection and Response (XDR) available for growing security needs.
- Pricing: Custom pricing is provided after entering the number of devices, but a 30-day free trial is available. The U.S. store simplifies the purchasing process for businesses ready to buy directly.
Website: https://www.eset.com/us/business/complete-protection/
9. Malwarebytes – Premium (Home) and Business
Malwarebytes has built a strong reputation as a go-to tool for malware cleanup, and its platform offers robust, real-time protection against emerging threats. It stands out by providing straightforward solutions for both individual users and businesses, making it an accessible choice for those seeking the best ransomware protection software without enterprise-level complexity. The platform's core strength lies in its simplicity; from the online checkout process to installation, users can get protected in just a few minutes with minimal technical expertise.
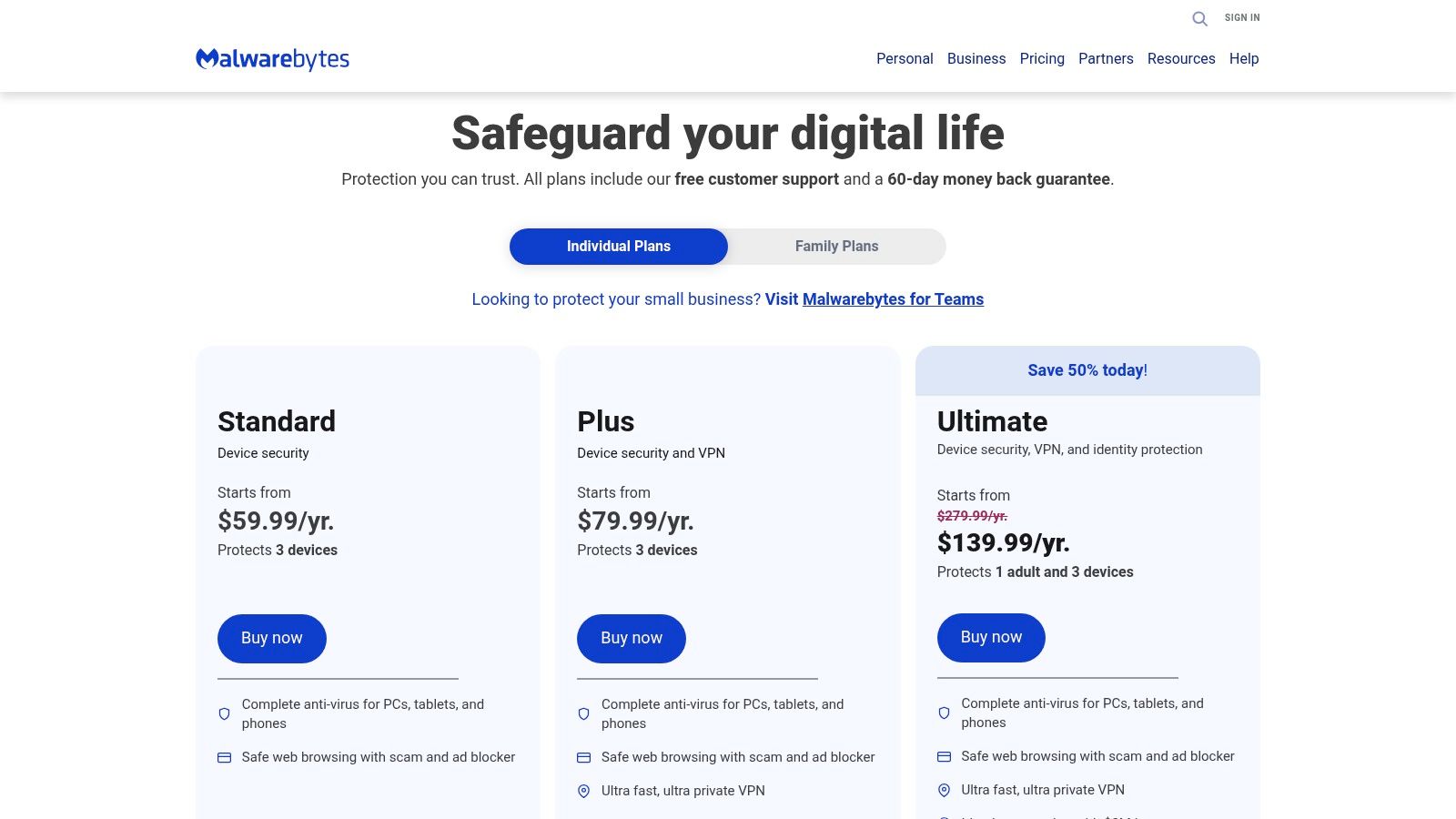
The company offers distinct product lines for home users and businesses, ensuring the features are tailored to the right audience. For small teams or businesses just starting with cybersecurity, the Business plans provide essential endpoint protection, detection, and remediation capabilities. A significant advantage is the transparent pricing and the generous 60-day money-back guarantee, which offers peace of mind and a risk-free trial period. While it may not have the extensive threat-hunting tools of an enterprise XDR solution, its effectiveness in stopping and removing malware is well-documented.
Key Features and Considerations
- Deployment: Simple download and installation process designed for non-technical users and small IT teams.
- Protection Engine: Employs multiple layers of security, including web protection, malware protection, and an anti-ransomware engine that specifically targets file-encrypting behavior.
- Scalability: Clear separation between Premium plans for home use and dedicated Business tiers (For Teams, Endpoint Protection) that scale with company size.
- Pricing: A 14-day free trial is available for business plans, with clear monthly or annual pricing listed online. The 60-day money-back guarantee is a key differentiator.
Website: https://www.malwarebytes.com/pricing
10. Acronis – Cyber Protect Home Office / True Image Cyber Security
Acronis approaches ransomware defense from a unique and highly practical angle by integrating active protection with comprehensive backup and recovery. Their Cyber Protect Home Office (formerly True Image) solution is built on the premise that the fastest way to recover from an attack is to restore your system from a clean backup. This makes it one of the best ransomware protection software options for small offices and home-based businesses that prioritize rapid business continuity over complex threat-hunting tools.
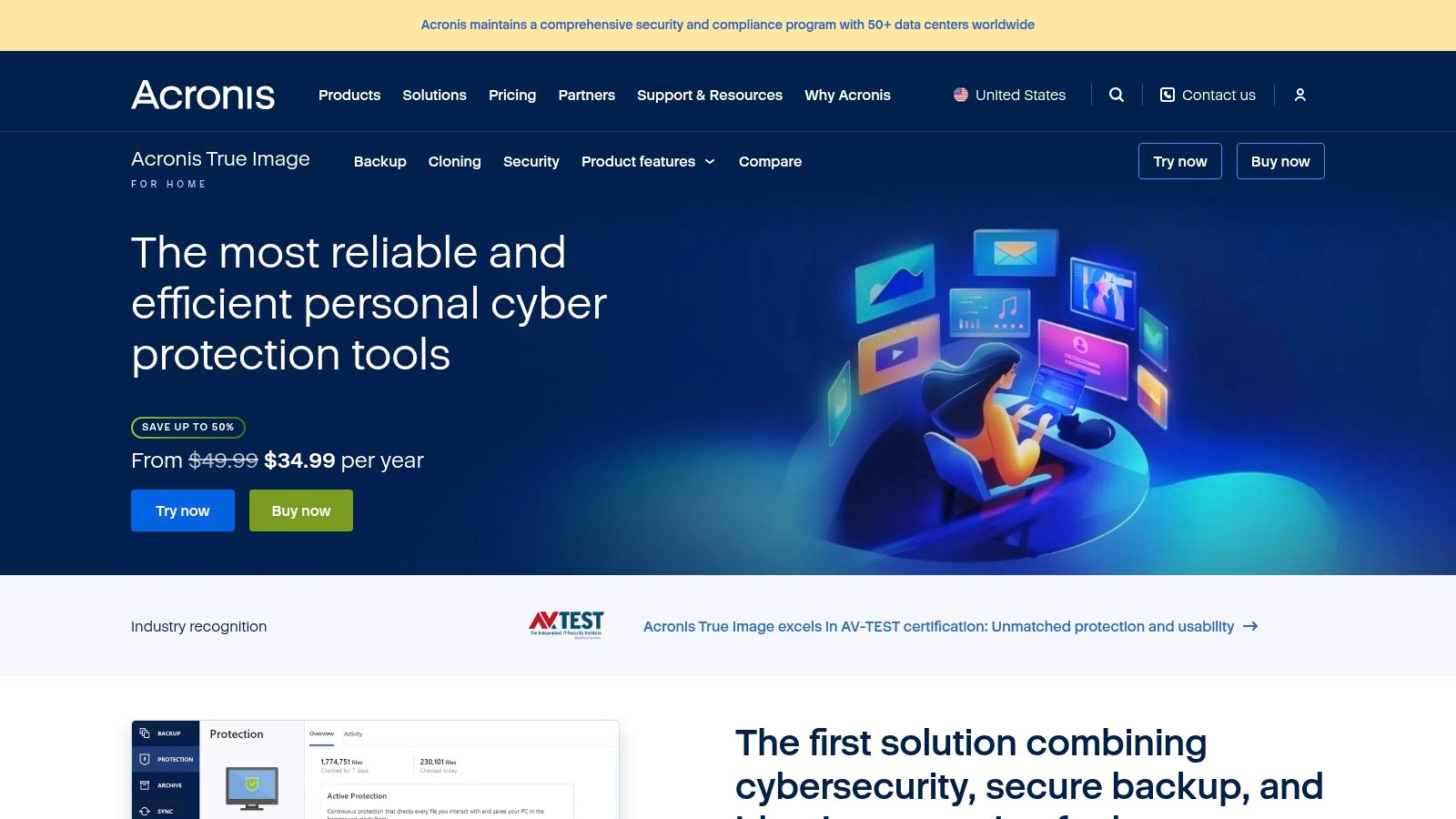
The platform's strength lies in its dual functionality. While its Active Protection technology monitors processes in real-time to detect and stop ransomware encryption, its core feature is creating full-image backups of your entire system. These backups can be stored locally, on a network drive, or in the Acronis Cloud. If an attack succeeds, you can restore your entire machine, including the OS, applications, and files, to its pre-infection state, drastically minimizing downtime and data loss. This combined approach is ideal for small businesses without dedicated IT staff.
Key Features and Considerations
- Deployment: Simple installer for Windows, macOS, Android, and iOS devices.
- Protection Engine: Combines real-time anti-malware and anti-ransomware protection with robust system imaging and file backup capabilities.
- Scalability: Primarily designed for individuals and very small offices; pricing tiers are based on the number of machines and the amount of cloud storage required.
- Pricing: Subscription-based, with annual plans that vary based on features and cloud storage (e.g., 50 GB to 5 TB). Promotional discounts are frequently available, especially for US customers.
Website: https://www.acronis.com/en/products/true-image/cyber-security/
11. CDW – Enterprise IT Reseller (Multiple Brands)
For businesses that prefer to procure IT solutions through a trusted channel partner, CDW offers a streamlined way to purchase the best ransomware protection software from multiple leading vendors. Instead of being a software developer, CDW is a massive value-added reseller that simplifies the complex world of enterprise licensing. This is ideal for organizations that need to manage quotes, invoices, and corporate purchasing workflows for products like SentinelOne, CrowdStrike, and Sophos all in one place.
CDW’s platform is built for business-to-business transactions, providing digital fulfillment that ensures rapid license delivery after purchase. Their value lies in being a one-stop shop where IT managers can compare and buy solutions, often with negotiated pricing or promotional discounts not available directly from the vendor. This is particularly useful for regulated industries that need to document their procurement process for compliance and risk management. For instance, you can acquire licenses that include SentinelOne's ransomware warranty directly through their portal.
Key Features and Considerations
- Deployment: Varies by product; CDW provides the licensing and access, but deployment follows the specific vendor’s process (e.g., cloud-native agent, on-premise).
- Protection Engine: Access to a wide catalog of top-tier Endpoint Protection (EPP) and Endpoint Detection and Response (EDR) solutions from various security vendors.
- Scalability: Designed for corporate and large-scale procurement, making it easy to purchase licenses for hundreds or thousands of devices at once.
- Pricing: Pricing is often quote-based, but some products are listed directly. Watch for occasional promotional pricing and bundles. Be aware that some offers may be restricted to new customers only.
Website: https://www.cdw.com/
12. Newegg – Downloadable Security Software Marketplace
While not a software developer itself, Newegg serves as a valuable marketplace for businesses seeking competitive pricing on top-tier security software. This major US retailer offers a vast selection of downloadable codes from leading brands like Norton, McAfee, Malwarebytes, and ESET. For businesses that have already identified a specific solution, Newegg often provides significant discounts compared to purchasing directly from the vendor, making it an excellent stop for budget-conscious procurement.
The platform’s key advantage is instant digital fulfillment. Upon purchase, product keys are delivered via email, allowing for immediate activation and deployment. This is especially useful for small businesses needing to quickly secure new devices or replace an expiring license without delay. Newegg clearly outlines details like device limits and auto-renewal terms on product pages, helping teams make informed decisions and find some of the best ransomware protection software at a reduced cost. However, it's crucial to verify the seller is Newegg itself to ensure authenticity and support.
Key Features and Considerations
- Deployment: Instant digital delivery of product keys via email for immediate download and installation from the vendor’s official site.
- Protection Engine: Varies by the brand purchased; Newegg is a marketplace offering a wide range of solutions from basic antivirus to comprehensive endpoint security suites.
- Scalability: Offers licenses for single devices up to multi-device packages suitable for small teams, with options from numerous industry-leading vendors.
- Pricing: Highly competitive with frequent sales and promotional discounts. Many digital products are non-returnable, so be certain of your choice before purchasing.
Website: https://www.newegg.com/Antivirus-Internet-Security-Download/SubCategory/ID-439
Top 12 Ransomware Protection Software Comparison
| Solution | Core Features / Security ★✨ | User Experience & Quality ★🏆 | Value Proposition 💰 | Target Audience 👥 | Unique Selling Points ✨ | Price Points 💰 |
|---|---|---|---|---|---|---|
| Defend IT Services | Managed IT, Cybersecurity, Print Services | Proactive 24/7 monitoring & rapid response | Customized roadmaps, veteran-owned local support | San Antonio businesses 👥 | Integrated print+security, local partnership ✨ | Custom pricing 💰 |
| CrowdStrike – Falcon Go/Pro/Enterprise | AI NGAV, EDR/XDR, firewall, device control | Lightweight agent, quick deployment | Transparent per-device pricing, 15-day trial | SMB & enterprise 👥 | Breach Prevention Warranty, online pricing ✨ | Annual billing only 💰 |
| SentinelOne – Singularity Platform | Behavior detection, ransomware rollback | Strong rollback, automated mitigation | Warranty up to $1M, flexible license | SMB & enterprise 👥 | Ransomware rollback, warranty program ✨ | Contact sales for some tiers 💰 |
| Microsoft Defender for Business (SMB) | NGAV/EDR, cross-platform, M365 integrated | Seamless Microsoft ecosystem integration | Competitive SMB pricing | SMB Microsoft users 👥 | Native Microsoft integration | Subscription 💰 |
| Sophos – Intercept X Endpoint & MDR | CryptoGuard anti-ransomware, auto rollback | Rapid incident response, cloud managed | Consistent strong test scores | SMB to enterprise 👥 | MDR 24/7 rapid response | Quote-based 💰 |
| Bitdefender – GravityZone | Ransomware rollback, fileless protection | Unified console, strong test scores | Online SMB purchase and demos | SMB to enterprise 👥 | Layered add-ons, clear SMB flow ✨ | Trial & quote 💰 |
| Trend Micro – Vision One / Apex One | ML, behavior monitoring, XDR | Deep policy granularity | Enterprise-grade broad protection | Enterprise 👥 | Broad XDR integration | Quote-based 💰 |
| ESET PROTECT Complete | Endpoint/mobile with patch/email security | Lightweight agents, flexible licensing | Frequent US promotions, mix & match | SMB/SME 👥 | Flexible seat management | Seat-based subscription 💰 |
| Malwarebytes Premium | Real-time ransomware protection | Simple install, consumer & SMB tiers | Easy purchase, strong malware cleanup | Home & SMB users 👥 | 60-day money-back guarantee | Affordable plans 💰 |
| Acronis Cyber Protect Home Office | Anti-ransomware + backup/restore | Combined backup & security | Good for small office/home | Home & small office 👥 | Integrated backup with security | Varies by storage 💰 |
| CDW – Enterprise IT Reseller | Multi-vendor catalog, corporate workflows | Fast license delivery, promo pricing | One-stop multi-brand reseller | Corporate buyers 👥 | Negotiated pricing & corporate support | Varies; quotes common 💰 |
| Newegg – Security Software Marketplace | Broad brands, instant digital delivery | Easy comparison & fast license access | Frequent deals & discounts | General consumers & SMB 👥 | Competitive pricing, instant fulfillment | Competitive pricing 💰 |
Making Your Choice: Partnering for a Secure Future
Navigating the crowded market of cybersecurity tools can be a daunting task. As we've detailed, the landscape of the best ransomware protection software is diverse, with solutions ranging from the sophisticated, AI-driven EDR of CrowdStrike and SentinelOne to the robust, user-friendly suites offered by Sophos and Bitdefender. We've also seen how Microsoft Defender for Business provides a powerful, integrated option for those within the Microsoft 365 ecosystem, and how specialists like Acronis blend top-tier protection with essential backup and recovery functions.
The key takeaway is that there is no single "best" solution for everyone. The right choice is deeply intertwined with your organization's specific operational context, particularly for small and midsize businesses. A standalone software license might seem cost-effective initially, but it places the immense responsibility of configuration, threat monitoring, and incident response directly on your shoulders. Without a dedicated IT security team, this approach can create dangerous gaps in your defenses.
Key Factors to Guide Your Decision
Before making a final commitment, revisit your core requirements. Your selection process should be a strategic exercise, not just a feature comparison.
-
Internal Expertise: Do you have a dedicated IT specialist with cybersecurity experience? If not, a self-managed platform like SentinelOne or CrowdStrike might be overwhelming. A Managed Detection and Response (MDR) service, like those offered by Sophos or a managed service provider, becomes a much more practical and secure choice.
-
Compliance and Regulation: For businesses in regulated industries like healthcare or finance, compliance is non-negotiable. Tools with strong reporting, auditing, and data governance features are critical. Ensure any potential solution can help you meet specific mandates like HIPAA or FINRA.
-
Integration and Infrastructure: How will the new software fit into your existing technology stack? Consider its compatibility with your cloud services, on-premise servers, and other business applications. A disjointed security posture is an exploitable one; seamless integration is key to comprehensive protection.
-
Beyond Prevention: The Role of Recovery: Ransomware protection isn't just about blocking attacks. It's about resilience. Even the best defenses can be breached, making a robust backup and disaster recovery plan essential. Solutions like Acronis Cyber Protect, which integrate both aspects, provide a critical safety net that ensures business continuity.
The Strategic Advantage of a Managed Security Partner
For many San Antonio SMBs, the most effective, secure, and cost-efficient path forward is not choosing a single tool, but rather a dedicated security partner. The complexity of modern threats requires more than just software; it demands constant vigilance, expert analysis, and rapid response capabilities that are often beyond the reach of a small internal team.
Partnering with a Managed Security Service Provider (MSSP) shifts the burden from your team to a group of dedicated experts. An MSSP doesn't just sell you a license. They implement, configure, and fine-tune a curated stack of best-in-class tools to match your specific risk profile. They provide the 24/7 monitoring necessary to detect threats in real-time and the skilled personnel to neutralize them before they can cause catastrophic damage. This approach transforms your security from a reactive, resource-draining chore into a proactive, strategic asset, allowing you to focus on your core business with genuine peace of mind.
Ultimately, selecting the best ransomware protection software is the first step on a longer journey. The goal is not just to install a program, but to build a resilient security posture that can adapt to an ever-evolving threat landscape. Whether you manage it in-house or entrust it to a proven partner, the decisive action you take today will be the foundation of your organization's secure future.
Feeling overwhelmed by the options? Let the experts at Defend IT Services build a security strategy tailored for your San Antonio business. We leverage industry-leading tools and provide 24/7 expert management to deliver enterprise-grade protection without the enterprise-level price tag. Contact Defend IT Services today to secure your business and regain your peace of mind.



