Threat intelligence isn't just a technical buzzword; it's the practice of gathering and analyzing information to understand who might attack you, why, and how. It’s about converting a flood of raw data into genuinely useful, actionable insights that help you make smarter, faster security decisions.
Ultimately, this lets you move from a reactive, "put out the fire" mindset to a proactive one.
What Is Threat Intelligence Really?

Think of your business as a medieval castle. You wouldn't just build high walls and hope for the best, right? A smart defender sends scouts into the surrounding lands to learn about potential enemies. These scouts find out who the attackers are, what weapons they carry, and how they plan to get past your defenses.
That’s exactly what threat intelligence does for your cybersecurity. It’s not simply a list of bad IP addresses or an alert about a new virus. It’s the fully analyzed story that gives you the context needed to make informed security choices and answer critical questions that raw data can't.
From Raw Data To Actionable Defense
Without context, a single piece of information—like a suspicious IP address hitting your firewall—is just noise. It could be anything. Threat intelligence provides the context that turns that noise into a clear signal, telling you if that IP is part of a known botnet or a targeted attack campaign.
This process involves pulling information from all kinds of places and piecing it together to create a clear picture of the threats you face. It’s what helps you get ahead of attacks instead of just cleaning up after them. For any company on the rise, recognizing the importance of cybersecurity for growing businesses is the crucial first step in building a defense that lasts.
Threat intelligence is what allows you to stop firefighting and start anticipating. It’s about building a security strategy based on solid evidence of what attackers are actually doing, not just what you assume they might do.
This kind of strategic foresight helps you put your resources where they’ll have the most impact. It sharpens your focus on the threats that are most likely to come after you. For a broader look at how digital clues are pieced together, understanding the scope of a cyber investigation can offer valuable perspective.
To put it simply, threat intelligence takes you through a clear, three-step journey from noise to action. Here’s a quick breakdown of how that works.
Threat Intelligence At A Glance
| Component | Description | Example |
|---|---|---|
| Data Collection | Gathering raw information from security logs, public reports, dark web forums, and other sources. | An automated system flags a file hash that just appeared on a known malware exchange site. |
| Analysis & Context | Processing the raw data to find patterns, motivations, and the capabilities of threat actors. | An analyst connects that file hash to a specific ransomware group known for targeting the healthcare industry. |
| Actionable Insight | Delivering a clear recommendation or automated action based on the analyzed intelligence. | The security team proactively blocks that file hash across all systems and warns staff about the specific threat. |
As you can see, each stage builds on the last, transforming a meaningless data point into a defensive move that protects the entire organization.
The Four Levels of Threat Intelligence
To really get a handle on threat intelligence, you have to stop thinking of it as one big stream of data. It’s actually a layered system, where each level gives a different kind of insight to a different person—from the IT pro in the server room all the way up to the CEO. These four distinct levels—Strategic, Tactical, Operational, and Technical—all work in concert to build a complete defensive picture.
Think of it like planning a cross-country road trip. You need the high-level map showing the start and end points (Strategic), the turn-by-turn GPS directions (Tactical), intel on which roads are notorious for traffic jams or construction (Operational), and a list of specific gas stations to refuel at along the way (Technical). You need all four to get to your destination safely and efficiently.
This layered approach isn't just a neat idea; it's become fundamental to modern cybersecurity. The global threat intelligence market was valued at around USD 14.64 billion and is expected to rocket to USD 57.90 billion by 2034, growing at a compound annual growth rate of 14.74%. This explosive growth shows just how critical these different intelligence layers are for businesses trying to stay ahead. You can explore more about the threat intelligence market forecast on Precedence Research.
Strategic Intelligence: The 30,000-Foot View
Strategic intelligence is the big-picture view, crafted for non-technical decision-makers like C-suite executives and board members. It’s all about answering the question, "How do global cyber threats affect our business goals and overall risk?"
This isn't about the nitty-gritty of a specific malware variant or a malicious IP address. Instead, it covers broad trends, geopolitical risks, and industry-wide threat patterns. A strategic report might, for example, warn of a surge in state-sponsored attacks targeting the financial sector or flag new data privacy laws that could lead to crippling fines.
The goal here is to inform long-term planning, justify security investments, and shape business strategy. It helps leadership put money where it matters most by understanding the potential financial and reputational fallout from different cyber threats.
Operational Intelligence: Understanding the Adversary
While strategic intelligence looks at the "what," operational intelligence zooms in on the "who" and "why" behind the attacks. It answers critical questions like, "Who is targeting us, what are their motivations, and how do they typically operate?"
This level is all about profiling the threat actors themselves. It digs into their intentions, their skill levels, and the patterns they follow. For instance, an operational report might identify a specific ransomware gang known for its double-extortion tactics or a hacktivist group gearing up for a campaign against companies in your industry.
By understanding the adversary's motives and methods, security teams can move from a reactive posture to a proactive one. It’s the difference between just blocking attacks and actively anticipating—and disrupting—the attacker's next move.
This context is gold for threat hunters and incident responders, giving them the vital intel they need to know what they're truly up against.
Tactical Intelligence: The Attacker’s Playbook
Tactical intelligence gets more technical, zeroing in on the immediate "how" of an attack. This is essentially the adversary's playbook, detailing their specific Tactics, Techniques, and Procedures (TTPs). It’s built for the hands-on defenders in the trenches, like SOC analysts and network engineers.
This level focuses on answering, "What specific methods are attackers using right now that could hit us?" A tactical intelligence feed would describe things like:
- Specific malware strains being deployed in current campaigns.
- Phishing email templates that are tricking users.
- Vulnerabilities that a particular hacking group is actively exploiting.
This information is immediately actionable. It's used to configure firewalls, write new detection rules for a SIEM, and fine-tune other security controls to counter active threats.
Technical Intelligence: The Ground-Level Indicators
Finally, technical intelligence is the most granular and fast-paced layer. It’s made up of specific Indicators of Compromise (IoCs)—the digital breadcrumbs an attacker leaves behind. This type of intelligence is often machine-readable, designed to be fed directly into automated security tools like firewalls and endpoint detection systems.
Technical intelligence provides concrete, black-and-white data points, such as:
- Malicious IP addresses
- Known phishing domains
- Malware file hashes
- Suspicious URL patterns
This is the frontline of defense, enabling systems to block known threats in real-time without human intervention. While a single IoC might only be relevant for a short time, a constant, fresh stream of technical intelligence is absolutely essential for maintaining a strong day-to-day security perimeter.
To pull it all together, here’s a quick breakdown of how these four types of threat intelligence compare.
Comparing the Four Types of Threat Intelligence
| Intelligence Type | Primary Focus | Audience | Example Question Answered |
|---|---|---|---|
| Strategic | High-level risks, trends, and business impact | Executives, Board Members, C-Suite | "How will a rise in nation-state attacks affect our five-year plan?" |
| Operational | The "who" and "why" behind an attack; adversary motives | Threat Hunters, Incident Responders | "Who is this ransomware group and what are their typical targets?" |
| Tactical | Attacker TTPs (Tactics, Techniques, & Procedures) | SOC Analysts, Security Engineers | "What specific phishing techniques are being used against our industry?" |
| Technical | Indicators of Compromise (IoCs) like IPs and hashes | Automated Security Tools (SIEM, Firewall) | "Is this IP address associated with a known command-and-control server?" |
Each layer provides a unique piece of the puzzle. Without the strategic view, you're flying blind. Without the technical details, your defenses are full of holes. A truly effective security program knows how to collect, analyze, and act on all four.
How Raw Data Becomes Actionable Intelligence
Threat intelligence isn't just a static report you read and file away. It's a dynamic, living process—a continuous cycle that transforms scattered bits of data into a powerful defensive tool. This whole journey is what we call the Threat Intelligence Lifecycle.
Think of it like a professional newsroom. An editor doesn't just shout, "Find me some news!" They assign specific beats, reporters go out to gather facts, and a story is carefully pieced together before it ever hits the press. The intelligence lifecycle follows a very similar six-phase path, making sure the final product is accurate, relevant, and actually useful.
This structured process is what separates genuine intelligence from a simple data dump. It’s a disciplined approach that builds context and meaning, turning something as small as a suspicious email attachment into a clear warning about an impending phishing campaign.
This infographic breaks down how the different levels of threat intelligence—Strategic, Operational, Tactical, and Technical—fit into different parts of an organization.
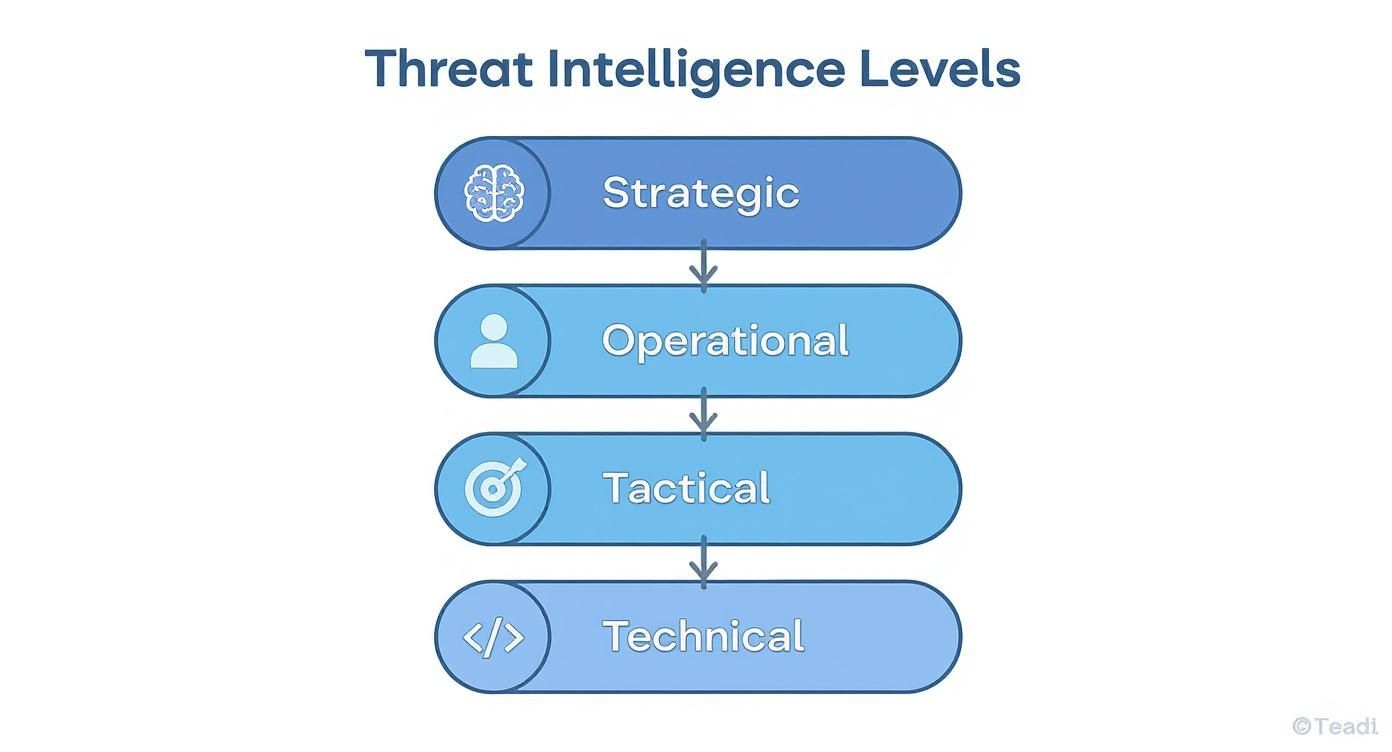
As you can see, intelligence flows from high-level strategic planning all the way down to the granular, machine-level technical details, creating a truly cohesive defense.
The Six Phases of the Intelligence Lifecycle
Each step in this cycle builds on the one before it, refining raw information until it becomes something you can act on. This methodical flow ensures security teams make decisions based on solid evidence, not just gut feelings.
1. Planning and Direction
This is where it all begins. Think of it as the editor setting the assignment. The security team figures out its goals based on what the business actually needs to protect. They ask critical questions like, "What are our most valuable digital assets?" or "Which cybercriminals are most likely to come after our industry?" Getting this phase right ensures the entire effort is focused on answering the most important questions from the very start.
2. Collection
With a clear plan in hand, it's time for the "reporters" to start gathering information. Raw data is pulled in from a massive number of sources, which typically fall into a few key categories:
- Internal Sources: This is your own data—things like network logs, past incident reports, and firewall alerts.
- External Sources: This includes open-source intelligence (OSINT) from public news, security blogs, social media chatter, and even dark web forums.
- Commercial Feeds: These are curated threat data streams you can buy from specialized security vendors.
3. Processing
Raw data is almost always messy and full of noise. This is the "organizing the notes" phase. All the collected information gets sorted, filtered, and formatted so it can be analyzed properly. This might mean translating data from different languages, pulling out key indicators from lengthy reports, or just stripping out all the irrelevant fluff.
The goal of processing is to prep the raw material for the most important step: analysis. Without this stage, analysts would be drowning in a sea of unusable data.
4. Analysis
Here’s where an analyst "connects the dots" to uncover the real story. They dig into the processed data to spot patterns, figure out what the adversary is trying to do, and build the all-important context. This is where the team answers the "so what?" behind the data. The leap from raw data to actionable intelligence happens right here, drawing on techniques also found in competitive intelligence analysis. A simple list of IP addresses, for example, becomes a map of an attacker’s infrastructure.
5. Dissemination
Once the story is written, it needs to get to the right audience. Intelligence is packaged into a digestible format—maybe a formal report, a quick alert, or a direct data feed—and delivered to the people who need to see it. This could be a high-level briefing for the C-suite or an automated update to a firewall's blocklist.
6. Feedback
Finally, the "newsroom" asks how they did. Stakeholders who received the intelligence weigh in on whether it met their needs. Was it timely? Was it relevant? This input feeds directly back into the planning phase, allowing the team to fine-tune its goals and get better with each cycle. It's this continuous loop that helps an intelligence program stay one step ahead of emerging threats.
Why Threat Intelligence Is a Business Imperative
It’s one thing to understand the technical side of threat intelligence, but the question every business leader asks is simple: "Why should we care?" The answer isn't just about IT; it's about protecting your bottom line, your reputation, and your ability to stay in business.
At its heart, threat intelligence helps you switch from a reactive to a proactive security mindset. Instead of waiting for an alarm to go off and scrambling to put out the fire, you start anticipating where the next attack might come from. This isn't just a small adjustment—it completely changes the game, turning your security from a frantic cleanup crew into a strategic advantage.
This shift pays off in real dollars. The market for threat intelligence is exploding, expected to reach USD 22.97 billion by 2030. That growth isn't just hype; it's a signal that businesses are seeing real value in using intelligence to get ahead of sophisticated cyber threats. You can see the numbers for yourself in the threat intelligence market forecast from MarketsandMarkets.
From Fighting Fires to Building Fortresses
Without good intelligence, a security team is always in crisis mode. Every alert could be a disaster, and they waste countless hours chasing down every little red flag. It’s an exhausting and inefficient way to operate.
Threat intelligence brings much-needed context to the chaos. It helps you instantly separate the real, urgent threats from the everyday background noise.
Think about it this way. An alert pops up for suspicious network activity.
- Without Intelligence: Your team drops everything to investigate. It could take them hours, maybe even days, only to find out it was a false alarm. They can't afford to ignore it, but the time is lost forever.
- With Intelligence: The system instantly recognizes the activity. It matches the pattern to a known ransomware group that's been hitting companies just like yours. Now, your response is fast, specific, and effective.
That ability to prioritize isn't just about saving time; it's about preventing burnout in a field where skilled people are hard to find and even harder to keep.
Threat intelligence doesn't just make your security tools better; it makes your security team smarter. It empowers them to make faster, more confident decisions that protect the entire organization.
Optimizing Security Spending and Reducing Risk
One of the best arguments for threat intelligence is how it helps your budget. Instead of throwing money at every new security gadget on the market, you can make smarter investments based on the actual threats you're facing.
If intelligence shows that attackers are targeting a specific software vulnerability in your industry, you can focus your resources on patching that system immediately. It’s about spending money where it will have the biggest impact.
This targeted approach means every dollar you spend on security delivers a real return. More importantly, preventing a breach helps you avoid the massive costs that come after one, which go far beyond just fixing computers. These costs include:
- Regulatory Fines: Hefty penalties for non-compliance with data protection laws.
- Legal Fees: The staggering cost of lawsuits and settlements.
- Customer Notification: The expensive and complex process of informing everyone affected.
- Reputational Damage: The long-term loss of customer trust, which can be the most devastating blow of all.
By knowing what's coming, you can build stronger defenses today to protect both your data and your brand's future. For any local company, combining this foresight with professional oversight is crucial, which is why every San Antonio business needs managed IT and cybersecurity services. In the end, threat intelligence stops being an IT-only issue and becomes a core part of your strategy for survival and growth.
Building Your Own Threat Intelligence Program

Moving from simply understanding threat intelligence to actually using it can feel like a massive leap. But it doesn't have to be. Creating an effective program is far less about buying expensive tools and much more about adopting a smart, methodical approach. You can start small and see major defensive improvements right away just by focusing on your biggest risks first.
The secret is to adopt a "crawl, walk, run" philosophy. Instead of trying to boil the ocean, you begin with manageable steps that provide immediate value. This kind of practical roadmap helps you build a security capability that scales with your business, no matter your current size or maturity.
This structured thinking is becoming more critical by the day. The need for better network protection has lit a fire under the cybersecurity sector, with the threat intelligence market alone projected to hit USD 26.19 billion by 2029, growing at a blistering CAGR of 17.9%. This isn't just hype; it reflects a genuine business need to fight back against sophisticated threats and secure modern infrastructure. You can get a deeper look at this trend in the full threat intelligence market report on Research and Markets.
Define Your Security Goals
Before you even think about collecting data, you need to know what you’re trying to protect and why. This is the single most important step. It anchors your entire program to real business needs, ensuring you don't waste time and money chasing irrelevant threats.
Start by asking some honest, fundamental questions:
- What are our crown jewels? Is it customer PII, our secret sauce intellectual property, or the operational tech that keeps the lights on?
- What are the biggest dangers in our industry? Are we in a sector constantly hammered by ransomware, or is a quiet data breach the more likely scenario?
- What rules do we have to play by? Do compliance frameworks like HIPAA or PCI DSS set specific security priorities for us?
Getting answers to these questions gives you a compass. It helps you zero in on the intelligence that matters to your organization and the threats that pose a genuine risk to your operations.
Identify Reliable Intelligence Sources
With clear goals set, you can start figuring out where to get your information. A solid program pulls from a mix of sources to create a complete picture of the threat landscape. You don’t need to subscribe to a dozen pricey feeds on day one; start with what's already out there for free.
Think about these three main buckets for your sources:
- Open-Source Intelligence (OSINT): This is the massive amount of publicly available information from security blogs, news sites, government alerts (like those from CISA), and industry-specific groups (ISACs). OSINT is an amazing, cost-effective place to start.
- Internal Intelligence: Your own security tools are a goldmine. Logs from your firewall, antivirus software, and incident response reports give you a front-row seat to the threats already knocking on your door.
- Commercial Feeds: As your program grows, you can look into paid threat intelligence feeds from specialized vendors. These providers offer curated, high-quality data that can often be plugged directly into your security tools for automated blocking and detection.
Select the Right Tools for the Job
Once you have data coming in, you need a way to make sense of it all. A Threat Intelligence Platform (TIP) is like the central nervous system for your program. It gathers data from all your different sources, standardizes it, and helps you spot the actionable insights.
A TIP transforms a chaotic flood of raw data into a manageable, prioritized stream of alerts. It connects the dots, reveals trends, and pushes relevant intel out to your other security systems.
For smaller businesses, a dedicated TIP might be overkill at first. You can start by using the threat intelligence features already built into your existing SIEM or firewall. The immediate goal is to centralize information so you can see the whole board, not just one piece.
As your needs mature, a managed services approach can give you the expertise and tooling you need without a huge upfront cost. Exploring professional cybersecurity services is a great way to bridge that gap.
Ultimately, building a threat intelligence program is a journey, not a destination. Start by setting your priorities, gather the right data, and use simple tools to make sense of it. By taking these practical steps, you can forge a powerful defensive shield that protects your business from the threats that truly matter.
Common Questions About Threat Intelligence
When people first start digging into threat intelligence, a few key questions always pop up. It's completely normal. Getting clear, straightforward answers is the first step in moving from just talking about security to actually building a smarter, intelligence-led defense.
Let's walk through three of the most common questions I hear. Clearing these up will give you a much better grasp of what threat intelligence really is and how it can work for you, no matter the size of your business.
What’s the Difference Between Threat Data and Threat Intelligence?
This is probably the most important distinction to get right from the start. People often use threat data and threat intelligence interchangeably, but they are worlds apart. Nailing this difference is crucial.
I like to use a weather forecasting analogy.
Threat Data is a single, raw fact. Think of it as one reading from a thermometer. It might be a malicious IP address, a suspicious domain, or a malware file hash. By itself, that one piece of data doesn't tell you much. A single temperature reading can't tell you if a blizzard is on the way.
Threat Intelligence is the full weather forecast. It’s what happens when an expert takes that temperature reading and analyzes it alongside wind speed, barometric pressure, historical patterns, and satellite images. The result is a forecast that says, "A blizzard is heading your way, it will hit around 8 PM, and you can expect 12 inches of snow."
In cybersecurity, intelligence is the context—the who, what, when, where, and why—that turns raw data into something you can actually use. It transforms a random IP address into a clear warning: "This IP belongs to a command-and-control server for a ransomware group that’s actively hitting financial firms in your region." Now that is something you can act on.
Is Threat Intelligence Just for Big Corporations?
There's a persistent myth that threat intelligence is a luxury only giant corporations with massive security budgets can afford. And while big companies certainly invest heavily, the reality is that the core ideas are just as critical—and achievable—for small and medium-sized businesses (SMBs).
It’s all about scaling the approach to fit your reality. An SMB doesn't need to track every state-sponsored hacking group on the planet. The goal is to focus on what matters to you.
You don't need a global spy network to defend your business. You just need timely, relevant information about the threats most likely to come knocking on your door.
Plenty of fantastic intelligence sources are free. Open-source intelligence (OSINT)—information gathered from public sources like security blogs, government alerts, and industry sharing groups—is incredibly valuable. By tapping into OSINT and a few affordable, specialized tools, SMBs can protect themselves from the same threats targeting the big players, without needing a huge security operations center.
How Does Artificial Intelligence Change Things?
The final big question is how artificial intelligence (AI) and machine learning (ML) play into all of this. These aren’t just buzzwords; they are fundamentally changing the game for threat intelligence. The amount of threat data created every single day is simply too vast for human analysts to handle on their own.
Think of AI and ML as a massive force multiplier for your security team. They can:
- Process enormous datasets at a speed and scale a person could never dream of.
- Spot hidden patterns and connect the dots between seemingly random security alerts.
- Help predict future attacks by learning from an adversary's past moves.
- Automate the tedious, repetitive tasks, which frees up your human experts to focus on the complex, strategic investigations that truly matter.
AI essentially helps your team find the needle in an ever-growing haystack, and find it much, much faster. It gives them the power to respond to threats almost instantly and even start anticipating what an attacker might do next, making proactive security a genuine possibility.
Ready to build a security strategy based on proactive intelligence instead of reactive firefighting? The experts at Defend IT Services can help you develop a threat intelligence program that fits your business, giving you the foresight needed to stay ahead of cyber threats. Learn more about our cybersecurity solutions today.

