Picture this: you get an email from your boss. It’s marked "URGENT," asking you to wire funds for a top-secret acquisition. It looks legitimate, the tone is right, but it’s a phantom. It’s a con artist, and you’re their target.
That, in a nutshell, is Business Email Compromise (BEC). It's not about viruses or complex hacking; it's a sophisticated scam that plays on human trust to trick you into sending money to criminals.
What Is Business Email Compromise?
Think of a BEC attack as the digital version of a master forger. Instead of faking a signature on a physical check, the scammer perfectly mimics a trusted identity over email. Their goal isn't to blast through your firewalls with malware. It's to simply walk through the front door by pretending to be someone you'd never question, like your CEO or a supplier you've worked with for years.
This method is so effective because it cleverly sidesteps most traditional security tools. Your email filter is looking for malicious links and infected attachments, but a BEC email often has neither. It's just text. The entire attack hinges on psychological manipulation, exploiting the fast-paced nature of business and the trust we place in our colleagues and partners. An attacker might even lurk in the background for weeks, studying your company's communication style and key players before making their move.
The Human Element of Deception
At its core, BEC is a social engineering masterclass. Attackers are experts at exploiting our natural tendency to be helpful, especially when a request comes from someone in charge. They manufacture a sense of urgency or secrecy, pressuring you to act before you have a chance to think it through.
Common tactics look like this:
- Impersonating Authority: An attacker poses as a C-level executive, pressuring a junior employee in finance to make a wire transfer that bypasses normal procedures.
- Exploiting Trust: They pretend to be a trusted vendor, sending a polite email notifying you of their "new" bank details for all future payments.
- Creating Urgency: The email might mention a critical payment that's overdue or a confidential deal that needs funding now, all to rush you into making a costly mistake.
To give you a clearer picture, let's break down what makes a BEC attack unique.
Key Characteristics of a BEC Attack
This table summarizes the fundamental elements that define a Business Email Compromise scam, providing a quick reference for readers.
| Characteristic | Description |
|---|---|
| No Malware | The emails are typically free of malicious links or attachments, making them hard for filters to detect. |
| High Deception | Attackers use social engineering, impersonation, and pretexting to manipulate victims. |
| Targeted | These are not spam campaigns; attackers research their targets to make the request highly believable. |
| Financial Goal | The ultimate objective is almost always to trick the victim into making a fraudulent wire transfer. |
Because these attacks prey on people, not just technology, even the most secure organizations can be vulnerable. This highlights a crucial point: strengthening your defense is about more than just software. It’s about building a security-aware culture, which is central to the importance of cybersecurity for growing businesses.
The financial toll is jaw-dropping. BEC isn't just a nuisance; it's one of the most lucrative cybercrimes on the planet. Between 2013 and 2022, these scams resulted in staggering global losses of over $50.8 billion.
Closer to home, the FBI’s Internet Crime Complaint Center (IC3) reported that BEC attacks cost U.S. businesses nearly $2.9 billion in a single year. These numbers prove just how serious the threat is for companies of every size.
How a BEC Attack Unfolds Step by Step
A Business Email Compromise attack isn't a random smash-and-grab job. It’s a carefully staged operation, a lot like a digital heist. The attackers are patient, methodical, and follow a clear playbook to trick your team and drain your bank account. Understanding how they operate is the first real step toward shutting them down.
The whole thing starts long before that fake email hits someone's inbox. It begins with the attacker doing their homework, acting like a private investigator digging for intel on your company.
Phase 1: The Stakeout (Reconnaissance and Target Selection)
In this first stage, the attacker’s goal is simple: learn everything they can about you. They’ll pore over your company’s structure, pinpoint who holds the keys to the kingdom, and figure out your internal workflows. This isn’t a blind guess; it’s a data-driven process to find the weakest link.
Attackers use public information from LinkedIn, company org charts, and even job descriptions to build a profile of their ideal targets. They're looking for executives, HR managers, and anyone in finance or compliance. This research allows them to personalize their scam, making the fake emails feel shockingly real. It’s no wonder that BEC accounted for 36.8% of cyber incidents in recent studies. You can dive deeper into these trends and what they mean for businesses in this detailed analysis of BEC tactics.
By mapping out relationships—who reports to whom, which vendors get paid regularly—the attacker creates a blueprint for a believable con. They’re simply looking for the path of least resistance to your money.
Phase 2: The Disguise (Impersonation and Account Control)
With a target in their sights, the attacker now needs a convincing disguise. This is the impersonation phase, where they figure out how to pose as someone your employee would trust, like the CEO or a key vendor. They typically use one of two methods:
- Email Spoofing: This is the low-tech but often effective approach. The attacker creates an email address that looks almost identical to a real one. Think subtle changes, like swapping an "l" for a "1" or a slight tweak to the domain (
ceo@acme-corp.cominstead ofceo@acmecorp.com). It's just enough to fool a busy employee at a quick glance. - Account Takeover (ATO): This is far more dangerous. Here, the attacker actually gets inside a legitimate employee's email account, usually by tricking them with a separate phishing attack to steal their password. Now, the attacker can send fraudulent emails from a trusted source, read existing conversations, and wait for the perfect moment to strike.
This simple flowchart shows just how straightforward the process is from the attacker's point of view.
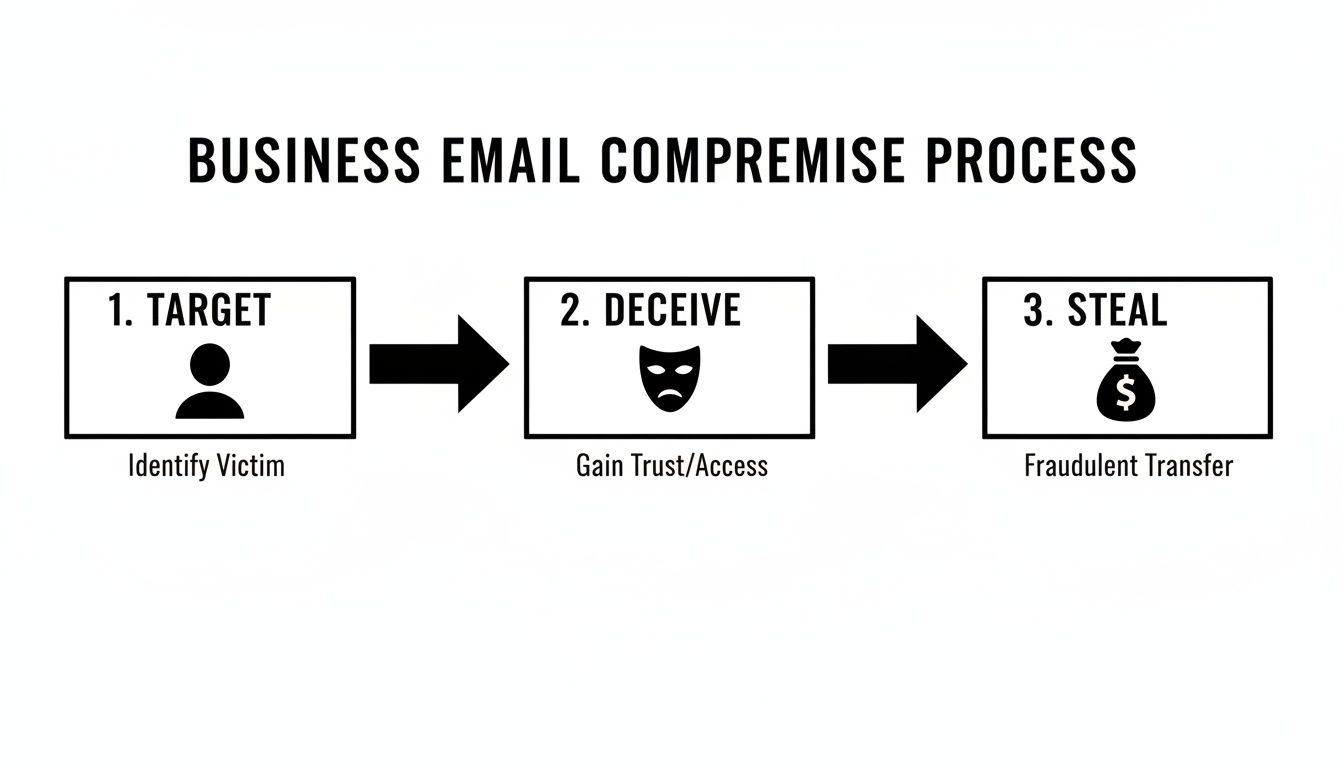
It really boils down to three key actions: find the right person, deceive them with a convincing story, and then make off with the money.
Phase 3: The Sting (Execution and Social Engineering)
This is the moment the attacker has been working toward. All that research and preparation comes down to a single email designed to manipulate your employee. The message is built on powerful psychological triggers.
The heart of a BEC email is pretexting—the art of creating a plausible, but completely false, scenario. The attacker invents a story that pressures the target to ignore normal procedures. They almost always lean on urgency, authority, or strict confidentiality to stop the person from thinking twice and verifying the request.
For instance, an email might look like it's from the CEO asking the finance department for an urgent wire transfer to close a "top-secret acquisition." By telling them not to discuss it with anyone, the attacker isolates the victim, using the weight of authority and secrecy to push them into complying without question.
Phase 4: The Getaway (The Payout and Money Mule Network)
If the scam works, the employee authorizes the payment. The money is wired out, but not to a legitimate partner. It goes directly into a bank account the criminal controls. From there, the final, crucial step begins.
To make the stolen funds disappear, attackers rely on a network of money mules. These are people—sometimes unwitting participants, sometimes complicit—who receive the stolen cash into their own accounts. They then quickly transfer it to other accounts, often overseas, slicing it up into smaller amounts along the way. This network is designed to launder the money so fast that by the time you realize what’s happened, it’s virtually impossible to trace or recover.
The 5 Most Common Types of BEC Scams
Business Email Compromise isn't just one type of attack; it's a whole playbook of cons. Each play is carefully designed to exploit a different corner of human trust and business process. Think of the attackers as masters of disguise, slipping into different personas to make their requests seem completely legitimate.
To really get a handle on this threat, you have to know the masks they wear. These scams are so effective because they’re not random—they are laser-focused on specific departments, from the finance team cutting checks to the HR department holding sensitive data.
Let's break down the five most common variations you're likely to run into.
1. CEO Fraud and Executive Impersonation
This is the quintessential BEC attack, the one you’ve probably heard about. An attacker crafts an email that looks like it’s coming from a high-level executive—usually the CEO or CFO. The email lands in the inbox of someone in finance or accounting with an urgent, time-sensitive demand. It’s almost always about a confidential matter, like a secret acquisition or a late payment to a critical partner that needs to be settled now.
The psychological trick here is authority bias. When an employee gets a direct order from the "boss," their first instinct is to comply quickly, not to question it. The attacker reinforces this by adding instructions like, "I'm about to step into a meeting and can't be reached by phone, please handle this via email," which cleverly cuts off the easiest path to verification.
Real-World Scenario: An accounting clerk receives an email that appears to be from her CEO. The message demands an immediate wire transfer of $45,000 to a new vendor to finalize a "confidential merger." The attacker repeatedly stresses the need for secrecy, preventing the clerk from running it by anyone else and ultimately causing a major financial loss.
2. Fake Invoice Schemes and Supplier Swindles
In this version, the scammer puts on the mask of a trusted supplier. They might hack into a real vendor's email account or just spoof their domain to send a fraudulent invoice to your accounts payable team. The email often looks identical to the real thing, simply informing your team of "updated" banking details for all future payments.
This is a particularly nasty tactic because it piggybacks on routine, everyday business. Paying invoices is a standard-issue task, so an email from a familiar vendor is far less likely to set off alarm bells. A recent and incredibly effective twist on this is conversation hijacking, where attackers compromise an email account and slip into an existing email thread about a real invoice. Right before payment is due, they chime in with a message like, "Hi, just a heads up, we've switched banks. Please use this new account for this payment." This specific tactic has seen a shocking 70% jump in use. You can learn more about the staggering evolution of BEC attacks and their financial impact.
3. Employee Account Compromise
This attack goes a step beyond simple impersonation. Instead of just faking an employee's email, the attacker gains full control of it, usually by tricking the employee with a phishing email to steal their password. Once they're in, they hold a powerful position. They can sit back and observe ongoing projects, learn the employee's communication style, and get their hands on contact lists for clients, partners, and vendors.
From inside this compromised account, the attacker can:
- Send fraudulent payment requests to your company's partners, using the employee's trusted email address.
- Authorize fake invoices internally, abusing the employee’s legitimate access.
- Intercept legitimate incoming payments and quietly redirect them to their own bank accounts.
Because these malicious emails are sent from a real, trusted account, they sail right past most technical filters and human suspicion. This makes it one of the most destructive and hardest-to-detect forms of BEC.
4. Attorney Impersonation and Legal Pretexts
Here, the scammer adds another layer of authority and urgency by pretending to be a lawyer or a representative from a law firm. The attacker usually contacts an executive or senior employee, claiming to be handling a highly confidential and time-sensitive legal matter.
The request almost always involves a wire transfer to settle a lawsuit, pay a retainer fee, or close a sensitive deal. The "attorney" will insist on absolute secrecy to avoid "jeopardizing the case," which is just another psychological ploy to pressure the target into bypassing the usual checks and balances. The legal jargon and the serious tone of the email make the request seem official and non-negotiable.
5. Data Theft Targeting HR and Finance
While most BEC attacks are a direct grab for cash, some are playing a longer game: stealing valuable information. In this scenario, attackers often impersonate an executive and send a request to the HR or finance department.
The email might ask for a complete list of employee W-2 forms, Social Security numbers, or other Personally Identifiable Information (PII). This data is pure gold on the dark web. It can be sold and used for widespread identity theft, tax fraud, or as ammunition for even more convincing spear-phishing attacks against your employees. It's a critical reminder that when we ask what is business email compromise, the answer isn't always money—sometimes, the prize is your data.
How to Spot the Red Flags of a BEC Email
While technology provides a crucial shield, your employees are your most active line of defense against Business Email Compromise. BEC attacks are designed to slip past filters by looking completely normal, which means a well-trained, skeptical human eye is often the last and best chance to stop a fraudulent payment before it's too late.
Empowering your team to recognize the subtle warning signs transforms them from potential targets into a powerful human firewall. The key is to cultivate a culture where it is not only safe but encouraged to pause, question, and verify any unusual request—no matter how urgent it seems or who it appears to come from.
Listen to Your Gut: The Psychology of the Request
The first red flag often isn't in the text itself but in the feeling it creates. Attackers are masters of psychological manipulation, and they build their entire scam around a few powerful triggers designed to make you act before you think.
An Overwhelming Sense of Urgency: The email insists that a payment or action must be taken immediately. Phrases like "handle this ASAP," "urgent action required," or "I'm in a meeting and can't talk" are used to rush you into making a mistake.
A Demand for Secrecy: The attacker will often instruct you not to speak to anyone else about the request. They'll claim it’s "confidential" or part of a "secret acquisition." This is a classic tactic to isolate you and prevent you from following normal verification procedures.
An Unusual or Uncharacteristic Request: If the CEO suddenly emails an accounts payable clerk directly to request a wire transfer, that’s a major break from the normal chain of command. Any request that seems out of the ordinary or bypasses established processes should be treated with extreme caution.
These emotional pressures are designed to short-circuit critical thinking. Recognizing them is the first step toward dismantling the attacker's strategy.
Look Closer: Scrutinizing the Email Details
Once that initial "gut check" raises a concern, it's time to put on your detective hat and examine the email's details. Attackers often hide in plain sight, hoping you won't look too closely.
A generic greeting like "Dear valued employee" is a huge giveaway. If the email is truly from a colleague or executive, they would almost certainly use your name. Likewise, keep an eye out for poor grammar or awkward phrasing, which can indicate the message was written by a non-native speaker or a sloppy AI tool.
Always Check the Sender's Details: An attacker might spoof the display name to look like "John Doe," but the actual email address might be
john.doe@acme-corp.cominstead of the legitimatejohn.doe@acmecorp.com. Hovering your cursor over the sender's name will reveal the true source address.
Also, be sure to check the "Reply-To" field. Scammers often configure it so that your reply goes to an email address they control, not the one that appeared in the "From" field. It's a subtle but very common trick.
Follow the Money: Changes to Payment Information
One of the most direct and dangerous red flags is a sudden, unexpected change to financial information. This is the classic endgame in supplier swindles and fake invoice scams.
Be on high alert for any email that includes:
- New Bank Account Details: A vendor you've paid for years suddenly sends an email announcing they have a new bank.
- Different Payment Methods: A request to switch from a check or ACH to an urgent wire transfer should be immediately verified.
- Last-Minute Invoice Changes: An email that intercepts an existing payment conversation to provide "updated" payment instructions for a pending invoice.
Any change involving money, no matter how small or plausibly explained, must be verified through an out-of-band channel. This simply means picking up the phone and calling a known, trusted number for the person or vendor making the request—never use the contact information provided in the suspicious email itself. This one simple step can stop a BEC attack dead in its tracks.
To help your team stay vigilant, here is a quick-reference checklist they can use to vet suspicious emails.
BEC Red Flag Checklist
| Red Flag Category | Specific Signs to Look For |
|---|---|
| Urgency & Secrecy | – Is there immense pressure to act now? – Does the sender ask you to keep it quiet or confidential? |
| Suspicious Sender | – Does the display name match the actual email address? – Is the domain slightly misspelled (e.g., acme-corp.com vs. acmecorp.com)? |
| Unusual Request | – Does this request bypass standard procedures? – Is it strange for this person to be contacting you about this topic? |
| Language & Tone | – Does the greeting seem generic ("Dear employee")? – Are there unusual grammar mistakes or awkward phrases? |
| Financial Changes | – Is there a last-minute change to bank account numbers? – Is there a request to change the payment method (e.g., to a wire transfer)? |
| Links & Attachments | – Are you being asked to click a link to a login page or open an unexpected invoice? |
Encourage your staff to keep these signs in mind. When an email checks multiple boxes on this list, it’s a strong signal to stop, verify, and report.
Proven Strategies to Prevent BEC Attacks

Moving from simply spotting threats to actively stopping them calls for a tough, multi-layered defense. A real strategy to prevent Business Email Compromise isn't about buying a single piece of software and calling it a day. It’s about building a resilient security posture on three pillars: strong technology, clear processes, and vigilant people.
When you weave these three elements together, you create a system where one layer can catch what another might miss. This approach transforms your defense from a simple wall into a deep, flexible security net capable of catching even the most convincing BEC scams.
Bolstering Your Technical Defenses
Your first line of defense is the technology that filters, authenticates, and secures your digital communications. These tools work behind the scenes, automatically blocking threats and making it much, much harder for attackers to impersonate trusted people or bust into your systems.
To fight back against the sophisticated impersonation tricks common in BEC, it's critical to implement strong email authentication protocols like SPF, DKIM, and DMARC. Think of these as a digital verification system, confirming that an email actually came from the domain it claims to.
Beyond authentication, Multi-Factor Authentication (MFA) is simply non-negotiable.
- How it Works: MFA demands a second form of verification—like a code from your phone—on top of a password.
- Why it Matters: Even if a scammer steals an employee’s password, MFA slams the door shut, stopping them from getting into the email account and derailing account takeover attempts.
With a staggering 58% of BEC attacks targeting businesses that don't use MFA, turning it on for all email and critical system accounts is one of the most powerful moves you can make.
Implementing Ironclad Business Processes
Technology alone won't cut it. The next layer is all about creating firm, easy-to-follow internal rules designed specifically to trip up a BEC attacker. These processes add crucial human checkpoints, especially for high-stakes actions like sending money.
The single most effective process is out-of-band verification. This just means confirming any sensitive request through a different channel than email. For instance, if you get an email asking for a wire transfer or a change in vendor payment details, you must:
- Stop: Don't reply to the email. Don't act on the request. Just stop.
- Verify: Pick up the phone and call the person who supposedly sent the email. Use a trusted number from your existing records—never a number from the suspicious email itself.
- Confirm: Verbally confirm that the request and all its details are legitimate before you do anything else.
This simple 'trusted callback' procedure has single-handedly foiled countless BEC attempts. It yanks control of the conversation away from the attacker and adds a verification step that is nearly impossible for them to fake.
Making this process official ensures that employees know that verifying requests isn't a suggestion; it's a mandatory step for protecting the company's money.
Empowering Your People as a Human Firewall
The final and most critical piece of your defense is your team. Since BEC attacks are built to exploit human trust, your employees have to be trained and empowered to be your first and last line of defense. A strong security culture is built on continuous education and awareness, not a one-and-done meeting.
This starts with ongoing security awareness training. Regular sessions should cover the latest BEC tactics, how to spot the red flags we've discussed, and your company's specific verification rules. Training can't be a one-time thing; it needs to be a continuous program that keeps security top of mind.
To make it all stick, combine training with simulated phishing exercises. These are controlled, fake BEC emails that test your team’s ability to spot and report threats in a safe environment. When an employee clicks on a simulated phish, it becomes a priceless—and low-stakes—learning moment.
Putting together a well-rounded prevention strategy is complex, which is why many organizations find that expert guidance makes all the difference. Understanding why every San Antonio business needs managed IT and cybersecurity services can provide a clear roadmap for implementing these essential protections. By combining technology, process, and people, you create a formidable defense against the threat of business email compromise.
Your Incident Response Plan After a BEC Attack
That sinking feeling in your stomach when you realize you've been hit by a Business Email Compromise scam is unforgettable. It’s a high-stress, gut-wrenching moment. But in the chaos that follows, acting with speed and precision is what separates a recoverable mistake from a catastrophic financial loss.
When the worst happens, you don't have time to figure out a plan on the fly. You need a playbook. The following steps give you a clear, actionable checklist to contain the breach, protect your money, and start the recovery process right away.
Step 1: Immediately Contain the Financial Damage
First things first: the money. As soon as you even suspect a fraudulent transfer has been made, your immediate focus has to be on stopping or reversing it.
- Call Your Bank's Fraud Department: Get on the phone with your bank instantly and tell them a wire transfer was fraudulent. Ask them to recall or reverse the funds. Time is absolutely critical here—the sooner you act, the better your odds.
- Request a SWIFT Recall: If the money went overseas, ask for a SWIFT recall notice. This is the official message sent through the international banking system to freeze the funds at the receiving bank.
- Freeze the Account: It's often a smart move to put a temporary freeze on the compromised account to block any more unauthorized transactions while you sort things out.
Every single minute counts. The faster you report the fraud, the higher the chance the funds can be intercepted before the attacker cashes out and disappears.
Step 2: Secure the Compromised Account
At the same time you're dealing with the bank, you have to lock the attacker out of your system. Think of the compromised email account as an active threat.
The goal is to immediately sever the attacker's access. This stops them from sending more fraudulent emails, deleting evidence, or escalating their attack by moving laterally through your network.
Take these actions right away:
- Reset Passwords: Immediately change the password for the compromised email account. Make sure the new one is long, complex, and totally unique.
- Enable Multi-Factor Authentication (MFA): If MFA wasn't already on, turn it on now. This is a non-negotiable security layer that can block the attacker even if they somehow get the new password.
- Review Account Rules: Scammers love to set up sneaky email forwarding rules or grant themselves delegate access to keep spying on conversations. Go through the account settings and delete anything you don't recognize.
Step 3: Preserve Evidence and Notify Leaders
Whatever you do, don't delete the fraudulent emails. These messages are critical evidence. You'll need them for your internal investigation and for law enforcement. Be sure to preserve the original emails with their full headers, as they contain a trail of digital breadcrumbs.
Once you’ve secured the evidence, alert your key internal stakeholders—your executive team, IT department, and legal counsel. Getting everyone on the same page quickly is essential for managing the crisis. It’s in these high-stakes moments that expert guidance becomes invaluable, which is why so many San Antonio businesses trust DefendIT Services for cybersecurity and IT solutions.
Step 4: Report the Crime to Law Enforcement
Finally, you have to report the incident. This isn't just about a slim chance of getting your money back; it's about helping the authorities build cases against these sophisticated criminal groups.
Your primary point of contact should be the FBI's Internet Crime Complaint Center (IC3). Go to their official website and file a detailed report. The IC3's Recovery Asset Team has a direct line to financial institutions and can help freeze funds, but they can only act on information they receive. Give them every detail you have: bank names, account numbers, transaction dates, and the exact amounts.
Frequently Asked Questions About Business Email Compromise
Even when you know the basics, a few common questions always pop up about Business Email Compromise. Let's dig into those to make sure everything is crystal clear.
Is BEC the Same as Phishing?
That’s a great question, and the short answer is no—but they are related. Think of it this way: phishing is like a huge net dragged across the ocean to catch anything that swims by, while BEC is like a skilled spearfisher patiently hunting a specific, high-value target.
Your average phishing attack is a numbers game. Scammers blast out thousands of generic emails with fake password reset links, hoping a small percentage of people will take the bait. It’s all about volume.
BEC is the opposite. It’s a specialized, carefully researched form of spear phishing. The attacker isn't trying to steal your password with a bad link; they’re trying to impersonate someone you trust to manipulate you psychologically. It's less of a technical hack and more of an old-fashioned con designed to trick a specific person into sending money.
Are Small Businesses Really a Target?
Absolutely. There's a dangerous myth that cybercriminals only chase after giant corporations with deep pockets. The reality is, small and midsize businesses (SMBs) are often the perfect target.
Why? It’s simple: attackers know SMBs usually have fewer security resources and their processes for approving payments are often less strict.
Think about it. In a small company, employees wear many hats. The person handling invoices might also be managing operations and answering the main phone line. This creates a busy, high-pressure environment where a well-crafted, urgent-sounding request can easily slip past an overwhelmed employee. While the big-dollar BEC heists grab the headlines, the constant, smaller-scale attacks on SMBs add up to billions in losses every year.
It’s estimated that 70% of organizations have been targeted by at least one BEC attack. This includes businesses of all shapes and sizes. Cybercriminals play a volume game, and SMBs are a massive, often less-protected group of potential victims.
How Does AI Make BEC Attacks More Dangerous?
Generative AI has put BEC attacks on steroids. It's made them incredibly difficult to spot. Not too long ago, you could often sniff out a scam email because of its clunky phrasing or obvious spelling mistakes. Those days are gone.
AI gives attackers a powerful toolkit to:
- Craft Flawless Emails: AI can write perfectly fluent, contextually appropriate emails in any language, making the scam instantly more convincing.
- Scale Personalized Attacks: A criminal can now generate thousands of unique, highly personalized email drafts in the time it used to take a human to write just a few.
What this means for your team is that you're now up against an avalanche of perfectly polished, persuasive scam emails. By mid-2024, an estimated 40% of BEC phishing emails were already being generated by AI. This trend makes having a sharp, well-trained team—a human firewall—more important than it has ever been.
Tackling the complexities of BEC and building a solid defense takes real expertise. Defend IT Services offers the managed cybersecurity and IT solutions San Antonio businesses need to stay protected from these sophisticated threats.

