CMMC certification is the Department of Defense's (DoD) way of making sure its partners can be trusted with sensitive information. Think of it as a mandatory security clearance, but for a company's entire digital infrastructure. It moves the entire Defense Industrial Base (DIB) away from a "trust us, we're secure" honor system to a "show us" model that requires proof.
What Is CMMC Certification and Why Does It Matter?
Imagine the DoD's sensitive data is priceless cargo. In the past, they'd hire a trucking company (a contractor) and basically take their word that the truck was armored and secure. CMMC changes all that. Now, every single truck in that supply chain has to pass a rigorous, standardized inspection before it can carry anything valuable.
This whole framework came about because cyberattacks on the DIB were becoming a massive problem. A breach at a small, seemingly insignificant subcontractor could easily expose critical data, creating a weak link that puts national security at risk. CMMC is designed to make sure every single link in that chain is strong and meets a specific, verifiable cybersecurity standard.
The Shift From Trust to Verification
The biggest change CMMC brings to the table is the move from self-attesting to third-party verification. For years, contractors could just fill out a form and say they were compliant with standards like NIST SP 800-171. That's no longer good enough.
Now, for most contracts, an independent Certified Third-Party Assessment Organization (C3PAO) has to come in and validate that a contractor’s security practices actually meet the required level. This shift has some major consequences:
- Real Accountability: It forces companies to truly implement and maintain cybersecurity controls, not just check a box on a form.
- A Level Playing Field: It creates a consistent security benchmark for everyone in the defense supply chain, from the giant prime contractors down to the smallest mom-and-pop machine shops.
- Serious Risk Reduction: By requiring a formal assessment, CMMC ensures that vulnerabilities are actually found and fixed, dramatically lowering the risk of a data breach.
CMMC Is More Than Just a Compliance Headache
It's easy to look at CMMC as just another regulatory hurdle to jump, but that's a mistake. Getting certified is a powerful business move. It proves to the DoD and prime contractors that you take protecting their information seriously, which builds immense trust.
Beyond that, the importance of cybersecurity for growing businesses can't be overstated. The work you do for CMMC strengthens your company's defenses against all kinds of cyberattacks, making you a much more resilient and secure organization overall.
The clock is ticking. The Cybersecurity Maturity Model Certification officially becomes a mandatory requirement for DoD contractors on November 10, 2025. The DoD estimates that around 8,350 companies will need to achieve CMMC Level 2, which requires a formal third-party assessment to win contracts. It's time to start preparing.
Understanding the Three CMMC 2.0 Levels
The Cybersecurity Maturity Model Certification (CMMC) isn't a one-size-fits-all mandate. It’s structured into three distinct levels, each demanding a higher degree of security. The whole point is to make sure the cybersecurity protections a contractor has in place are a perfect match for the sensitivity of the government information they handle.
Think of it like building a secure facility. You wouldn't use the same blueprint for a simple storage shed that you would for a bank vault. Each CMMC level builds on the one before it, creating a clear, progressive path toward a stronger cybersecurity posture. This tiered approach allows the Department of Defense (DoD) to set appropriate standards for everyone in its massive supply chain, from small-town machine shops to major defense contractors.
Ultimately, the specific CMMC certification level your company needs will be spelled out in your DoD contracts, based entirely on the type of data you'll be working with.
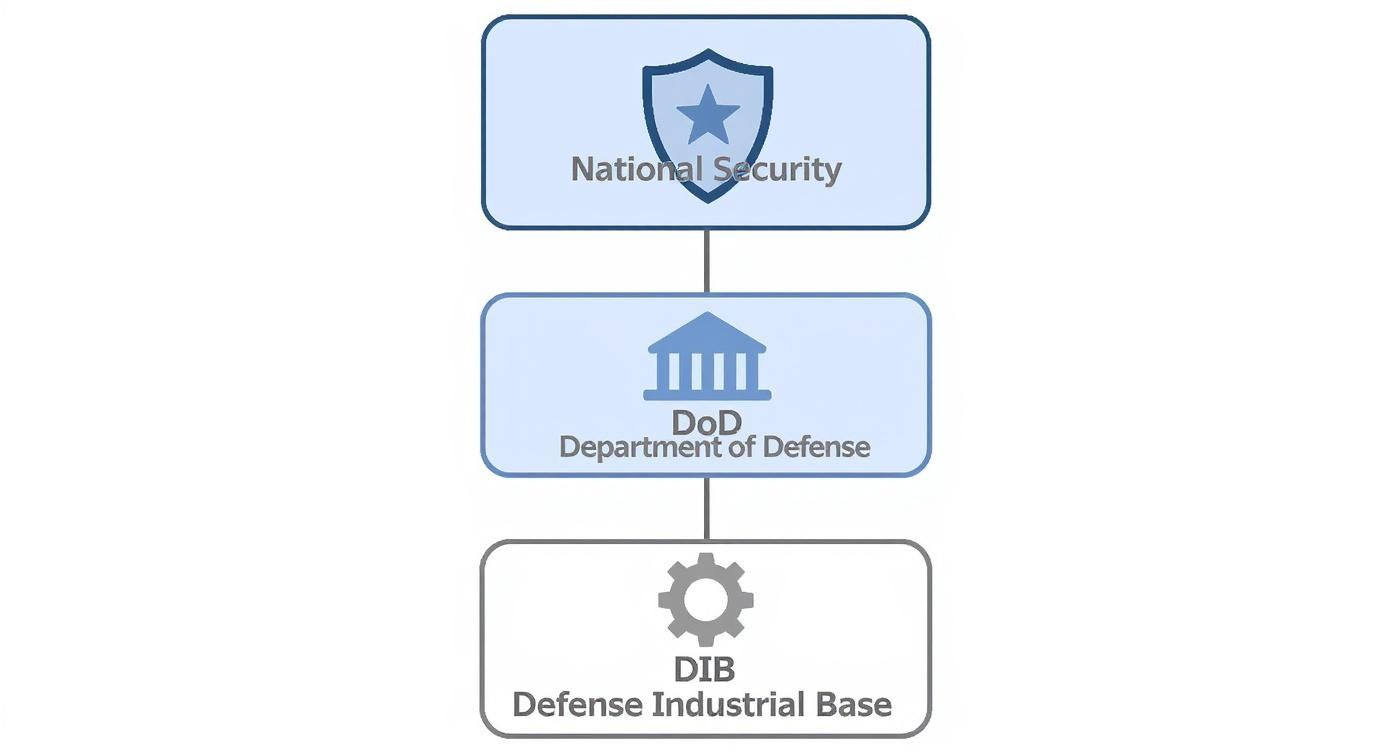
This structure is all about protecting our national security by securing the Defense Industrial Base (DIB) from the ground up.
Level 1: Foundational
Level 1 is the starting line for CMMC. Think of it as putting good locks on the doors, setting up an alarm system, and installing security cameras. These are the basic, common-sense cybersecurity practices every business should already be doing.
This level is all about protecting Federal Contract Information (FCI). FCI is essentially any information the government provides or that you generate for a contract that isn't meant for public eyes. The requirements are pretty straightforward, lining up with the 17 basic safeguarding practices found in FAR 52.204-21.
Key Takeaway: Level 1 requires an annual self-assessment. The company’s leadership simply has to affirm that they are meeting the requirements. There’s no third-party audit involved, which makes this the most accessible certification level for contractors who only ever touch FCI.
Level 2: Advanced
Stepping up to Level 2 is like upgrading your facility to a full-blown security operations center. We're talking controlled access points, professional guards, and mandatory ID checks for anyone coming or going. This is a major jump in security maturity and is where the vast majority of contractors in the DIB will land.
Level 2 is designed to protect Controlled Unclassified Information (CUI). The requirements here are much more rigorous, aligning directly with the 110 security controls detailed in NIST SP 800-171. CUI is sensitive government data that needs strong protection but isn't formally classified.
Unlike Level 1, getting a Level 2 CMMC certification usually means a formal, hands-on assessment every three years. This audit must be conducted by an authorized Certified Third-Party Assessment Organization (C3PAO). While the DoD has hinted that some specific programs might only require a self-assessment, most companies handling CUI should prepare for the third-party validation.
Level 3: Expert
Level 3 is the high-security vault. It's the digital equivalent of a Sensitive Compartmented Information Facility (SCIF), complete with biometric scanners, reinforced walls, and 24/7 surveillance by elite security teams. This level is reserved for companies handling the most critical CUI connected to our nation's top defense priorities.
The requirements for Level 3 pull from NIST SP 800-172, which adds a powerful layer of enhanced controls on top of the 110 from Level 2. These extra practices are specifically designed to fend off Advanced Persistent Threats (APTs)—the sophisticated, state-sponsored hacking groups that pose the greatest risk.
Assessments for Level 3 aren't handled by C3PAOs. They are performed directly by government assessors from the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). This direct government oversight just goes to show how critical the programs requiring this level of certification are.
CMMC 2.0 Maturity Levels Comparison
To make it easier to see the differences at a glance, here’s a breakdown of the three levels and what they entail.
| Maturity Level | Required Practices/Controls | Assessment Type | Applies To Contractors Handling |
|---|---|---|---|
| Level 1 Foundational | 17 Practices from FAR 52.204-21 | Annual Self-Assessment | Federal Contract Information (FCI) only |
| Level 2 Advanced | 110 Controls from NIST SP 800-171 | Triennial C3PAO Assessment | Controlled Unclassified Information (CUI) |
| Level 3 Expert | 110+ Controls from NIST SP 800-172 | Triennial Government-Led Assessment | CUI for high-priority DoD programs |
Getting a firm grasp on these levels is the first real step in your compliance journey. Once you know what kind of information your company handles for the DoD, you can zero in on your target CMMC level and start building a clear roadmap to get there.
Your Step-by-Step CMMC Certification Roadmap
Getting CMMC certified isn't a one-and-done task; it's a methodical journey. The best way to think about it is like preparing for a major professional audit. Success comes from careful planning, an honest look in the mirror, and a lot of hard work long before the assessors show up at your door. This roadmap breaks the whole process down into four clear phases to get you from square one to the finish line.
This isn't just about passing a test. It's about building a sustainable security culture that keeps your defenses strong long after you have the certificate in hand. Let's walk through what you need to do.
Phase 1: Define Your Assessment Scope
Before you touch a single control, you have to draw a line in the sand. This first step—defining your scope—is easily the most important one. It sets the boundaries for everything else and directly impacts the cost, complexity, and timeline of your entire certification effort. The goal here is to pinpoint every single place on your network where Controlled Unclassified Information (CUI) is stored, processed, or transmitted.
Think of your network as a large building. Instead of trying to secure every single room, you first identify only the rooms that contain valuable assets. That designated area—your "CUI environment"—becomes your entire focus. Getting this right from the start prevents "scope creep," which is when the assessment starts ballooning out of control, taking your budget and deadlines with it.
A well-defined scope should clearly identify things like:
- The specific servers or cloud instances where CUI lives.
- The laptops and workstations used by employees who handle CUI.
- The software and applications that touch that sensitive data.
Phase 2: Conduct a Gap Analysis
Okay, you know what you need to protect. Now you need to figure out how your current security measures stack up against the CMMC level you're aiming for. This is your gap analysis. It’s essentially a pre-audit inspection where you get brutally honest about your strengths and, more importantly, your weaknesses.
In this phase, you'll go control by control, comparing what you have in place—your policies, procedures, and tech—against the specific requirements of your target CMMC level. For Level 2, that means lining up your practices against the 110 controls in NIST SP 800-171. This process will create a crystal-clear picture of where you’re falling short.
For example, you might have rock-solid password policies (a control) but realize you've never actually documented an incident response plan (a gap). The output of this phase is a detailed report that becomes the blueprint for your remediation work.
Phase 3: Remediate and Implement Controls
Armed with your gap analysis, it's time to get to work and close those security holes. This remediation phase is where the heavy lifting happens, involving a mix of technical implementations and procedural groundwork. You'll be implementing missing security controls, writing new policies, and training your team on the new rules of the road.
This is a hands-on stage that could involve a variety of tasks:
- Technical Implementation: Rolling out new security tools like multi-factor authentication (MFA) or deploying endpoint detection and response (EDR) software.
- Policy Development: Writing and formalizing essential documents, such as an access control policy, a System Security Plan (SSP), or an incident response plan.
- Process Improvement: Training your staff on how to properly handle CUI and how to spot a phishing email a mile away.
As you map out your CMMC journey, it can be useful to see how it fits into the bigger picture. Looking at a general cybersecurity certification roadmap can help you align your company's compliance goals with broader professional development for your team.
Phase 4: Prepare for the Formal Assessment
Once the remediation work is done, you're in the home stretch. It’s time to engage a Certified Third-Party Assessment Organization (C3PAO) to conduct your formal audit. Preparation here is everything. You'll need to gather and organize all your documentation—policies, procedures, and tangible proof that your security controls are working as intended. Your job is to make the assessor's job easy.
It's a lot like preparing your financial records for a tax audit. The better organized and more complete your evidence is, the smoother and faster the whole thing will go. The C3PAO will perform a deep dive to validate that every single practice meets the requirements for your target CMMC certification level. For a real-world perspective on partnering with an expert, see how San Antonio businesses trust DefendIT Services to navigate these complex waters.
The CMMC Readiness Checklist and Common Pitfalls
Knowing the path to CMMC certification is one thing; actually walking it is another. It’s easy to get lost in the weeds. To succeed, you need a sharp focus on what to do—and just as importantly, what not to do.
Think of this as your pre-flight check. A pilot doesn't just hope the plane will fly; they methodically verify every critical system before takeoff. You need to do the same for your security posture before an assessor ever walks through your door. This isn't about a last-minute sprint; it’s about building a security-first culture that can stand up to scrutiny.

Key Domains for Your Readiness Checklist
While a full CMMC assessment is incredibly detailed, you can make huge strides by focusing on a few foundational areas. Assessors need to see more than just technology; they need proof in the form of solid documentation.
Here's where to start:
Access Control: Who gets the keys to the kingdom? You must prove you’re enforcing the principle of least privilege, which means people can only access the bare minimum of information they need to do their jobs. This is where strong password policies and multi-factor authentication (MFA) become non-negotiable.
System and Information Integrity: How do you keep your systems clean and secure from malicious code or unauthorized tweaks? This domain is all about having antivirus software, running regular vulnerability scans, and—crucially—having a process to apply security patches quickly.
Incident Response: When something goes wrong (and it will), what's the plan? You need a documented incident response plan that lays out exactly how to detect, contain, and recover from a cyberattack. This isn't just a technical playbook; it defines roles, responsibilities, and who calls whom.
Audit and Accountability: Can you trace what happened on your network, who did it, and when? Assessors will dig into your audit logs. These records are your best friend for investigating an incident and proving you’ve been compliant all along.
Choosing the right enterprise security software solutions is a major step forward, as these tools are the backbone for implementing many of the required controls.
Common CMMC Certification Pitfalls to Avoid
Knowing the rules is half the battle. Knowing where everyone else messes up is the other half. The road to CMMC certification is littered with predictable—and avoidable—mistakes.
The gap between knowing about CMMC and being ready for it is huge. Fresh data from CMMC CON 2025 is pretty eye-opening: only about 1% of defense contractors felt completely ready for their formal assessment. That number is actually going down.
While 69% of contractors say they're DFARS compliant, only 30% have had assessments rigorous enough to prove it. And even though the average SPRS score crept up to 60 in 2025, a startling 17% of contractors still have negative scores, which points to massive security gaps.
Crucial Warning: The single biggest mistake we see is companies treating CMMC as an "IT project." It's not. CMMC certification is a business-level commitment that requires leadership buy-in, participation from every department, and a real shift in company culture.
Steering clear of these common blunders will save you an incredible amount of time, money, and frustration.
Top Mistakes That Delay Certification
Improper Scoping: Getting the boundary of your CUI environment wrong is a fatal flaw. We mentioned it in the roadmap, and it’s worth repeating. Scope it too broadly, and your assessment becomes a nightmare of complexity and cost. Scope it too narrowly, and it’s an automatic fail.
Poor or Missing Documentation: You can have the best security tools on the market, but if you can't produce a System Security Plan (SSP), policies, and standard operating procedures for an assessor, you will not pass. Their mantra is simple: "If it's not documented, it didn't happen."
Underestimating Resources: CMMC compliance takes time and money—often more than you think. Many businesses fail to budget properly for new software, hardware upgrades, expert consulting, and the sheer number of employee hours needed for implementation and training.
By using this checklist to get prepared and actively avoiding these common pitfalls, you can turn CMMC from a source of anxiety into a manageable and strategic business goal.
Estimating Your CMMC Certification Costs
Trying to budget for your CMMC certification can feel like trying to hit a moving target. Let's be honest: there's no single price tag. Your total investment will depend on your company’s size, the CMMC level you're aiming for, and—most importantly—where your cybersecurity stands today.
Think of it like a home renovation. The cost to gut and rebuild a kitchen is worlds apart from just adding a fresh coat of paint. It's the same here. A company that already has a solid security program will spend far less than one building its defenses from the ground up. The journey to a successful CMMC certification is more than just the final assessment fee; it’s a full-on investment in your security infrastructure.
Breaking Down the Hard and Soft Costs
Your CMMC budget really boils down to two categories: hard costs and soft costs. Getting a handle on both is crucial for building a realistic financial plan and getting the buy-in you need from leadership.
Hard Costs are the straightforward, out-of-pocket expenses you'll pay to outside vendors. These are the easiest to track and budget for.
- Technology and Software: This covers any new security tools you might need, like multi-factor authentication (MFA) solutions, endpoint detection and response (EDR) software, or secure file-sharing platforms.
- Consulting and Advisory Services: Many businesses bring in CMMC experts for gap analysis, remediation help, and assessment prep. These services typically run between $150 and $400 per hour.
- C3PAO Assessment Fee: This is what you'll pay for the official audit by a Certified Third-Party Assessment Organization. For a Level 2 assessment, expect this fee to be anywhere from $20,000 to $60,000, sometimes more, depending on how complex your CUI environment is.
Soft Costs are the internal resources you’ll pour into the effort. You aren't writing a check for these, but they have a very real impact on your bottom line.
- Internal Staff Time: This is the big one. Your team will likely spend hundreds of hours on scoping the project, fixing gaps, writing documentation, and getting trained. It's easily the most underestimated "cost" in the whole process.
- Productivity Impact: Let's face it, rolling out new security controls and processes can slow things down for a bit while everyone gets used to the new way of doing things.
What's a Realistic Budget for a Small Business?
Every company is different, of course, but we can ballpark it for a small business (under 100 employees) going for Level 2 certification. If your security posture is moderately mature, you should probably plan for a total investment between $50,000 and $150,000. This range accounts for consulting, necessary tech upgrades, and the final C3PAO assessment.
A huge factor in controlling these costs is your timeline. The Department of Defense suggests organizations start preparing at least six months before they need certification. In our experience, a realistic timeline from the first gap analysis to a successful assessment is closer to 12-18 months.
This isn't just about spreading out the financial hit. It's about giving your team the runway to properly implement controls, train employees, and build the security-first culture you need to not just get compliant, but stay compliant. Rushing the process almost always leads to expensive mistakes and a failed assessment, which means you’re back at square one.
The best approach? Treat CMMC as a strategic, long-term investment. That’s the most reliable path to success.
The Business Benefits of CMMC Certification
It’s easy to look at CMMC certification as just another box to check for the government. But seeing it that way is a huge missed opportunity. Yes, it’s a must-have for winning Department of Defense (DoD) contracts, but the real payoff goes far beyond that. Getting certified is a smart, strategic move that strengthens your business for the long haul.
Think of it like this: a solid security fence doesn’t just meet a building code. It actively protects your property and gives your customers confidence. In the same way, the CMMC framework forces you to build a stronger, more secure, and more efficient company—making you a better partner for everyone, not just the DoD.
Gaining a Powerful Competitive Edge
In a world where data breaches are front-page news, having a verified cybersecurity posture makes you stand out. A CMMC certification is a clear signal to the entire market that you take security seriously. This builds immediate trust with commercial clients and partners who are growing more and more nervous about their own supply chain risks.
This commitment to security can unlock doors to entirely new markets and attract customers who won't work with anyone less secure. Suddenly, your compliance becomes a powerful selling point that proves you can be trusted with their most sensitive information.
Investing in a strong security posture is no longer just about defense; it's about offense. It allows you to confidently pursue opportunities that your less-secure competitors cannot, turning compliance into a true competitive advantage.
Improving Operational Health and Resilience
The journey to CMMC readiness forces you to get your house in order. You have to map out where your data lives, how it moves, and who can access it. This process almost always uncovers hidden inefficiencies and clunky workflows that have nothing to do with security. The end result is a leaner, better-organized, and more effective operation.
On top of that, a robust security posture dramatically lowers your risk of suffering a catastrophic data breach. By implementing essential controls like incident response plans and access management, you're far better equipped to stop attacks before they start and to recover quickly if one gets through. This minimizes downtime and financial damage. Good security isn't just a compliance task; it's a fundamental part of business continuity. For more on this, you can explore why every San Antonio business needs managed IT and cybersecurity services.
The data backs this up. A recent survey of companies that aligned with CMMC controls found real, measurable benefits. A noteworthy 54% reported better efficiency, 48% saw a reduction in security-related losses, and 23% gained a clear competitive edge. You can find more details in these CMMC compliance findings.
At the end of the day, CMMC certification is an investment in your company's future. It lays a foundation of security and operational excellence that protects your business, builds unwavering customer trust, and creates new paths for growth.
CMMC Questions Answered
When you're trying to wrap your head around CMMC, a lot of practical questions come up. Let's tackle some of the most common ones we hear from contractors just like you.
Does Every Single DoD Contractor Need CMMC?
Pretty much, yes. If you’re a contractor or a subcontractor in the Department of Defense (DoD) supply chain, you’ll need to meet specific CMMC requirements to bid on and win new work. The level you need to hit depends on the kind of information you handle—either Federal Contract Information (FCI) or the more sensitive Controlled Unclassified Information (CUI).
There's one main exception to this rule: contracts that are only for Commercial Off-the-Shelf (COTS) items. Even then, most experts agree that it's smart for COTS suppliers to implement the basic Level 1 controls. Better safe than sorry.
How Long is a CMMC Certification Good For?
Once you earn your CMMC certification, it's valid for three years. After that, you'll need to go through a reassessment to keep your certification active.
This isn't just a "one and done" checklist. The DoD wants to see that you're committed to cybersecurity for the long haul, not just scrambling to pass an audit every few years.
Keep in mind, you also have to submit an annual affirmation to the Supplier Performance Risk System (SPRS). This is your official yearly statement confirming that you're still maintaining the required security controls between those big three-year assessments.
Can We Just Certify Ourselves?
That depends entirely on the level you're aiming for. For Level 1, which is all about basic cyber hygiene for protecting FCI, you can do an annual self-assessment. You'll then submit an affirmation to the DoD stating you're in compliance.
But for Level 2 and Level 3, self-certification is off the table. These levels require a formal assessment from either a certified third-party organization or a government team. While you can't sign off on it yourself, you absolutely should—and are expected to—perform a detailed internal self-assessment first. This is your chance to find and fix any gaps before the official auditors walk through the door.
Ready to stop guessing and get a clear picture of your CMMC requirements? Defend IT Services provides expert guidance for everything from readiness assessments to full-scale remediation. We'll make sure you're ready for a successful certification. Secure your spot in the DoD supply chain by visiting us at https://defenditservices.com to get started.

