In the hidden corners of the internet, your company’s sensitive data could already be for sale. Compromised employee credentials, customer information, and proprietary secrets are frequently traded on dark web marketplaces, creating significant risks for businesses of all sizes. A single exposed password can lead to a full-blown data breach, resulting in financial loss, reputational damage, and regulatory penalties. Proactive monitoring isn't just a good idea; it's a critical defense mechanism.
This guide is designed to help you select from the best dark web monitoring services available. We cut through the noise to provide a direct comparison of the leading platforms, focusing on the features that matter most to small and midsize businesses, regulated organizations, and growing teams. From comprehensive threat intelligence to simple identity theft alerts, the right solution can provide the early warnings needed to neutralize threats before they escalate. A complete security posture also includes physical asset management; a critical component of proactive protection involves strategies for electronics recycling for data breaches prevention, ensuring sensitive information doesn't become exposed through discarded devices.
Below, you will find an in-depth analysis of each service, complete with screenshots, direct links, and actionable insights. We'll explore:
- Key features and monitoring capabilities.
- Ideal use cases for different business needs.
- Strengths and weaknesses of each platform.
This roundup will equip you with the information necessary to choose a service that effectively safeguards your digital assets and strengthens your overall security framework.
1. Managed IT Services from Defend IT Services — with 24/7 Threat Monitoring & Response
Defend IT Services distinguishes itself by framing dark web monitoring not as a standalone product, but as a critical, integrated component of a comprehensive managed cybersecurity service. This approach is specifically engineered for small to midsize businesses (SMEs) that require enterprise-grade security without the overhead of an in-house security team. Instead of simply providing alerts about compromised data, Defend IT Services delivers a full-cycle, hands-on response, making it a standout choice for organizations seeking a complete security partner.

The core strength of their offering lies in its fusion of proactive detection and immediate, expert-led remediation. This holistic model ensures that when a threat is identified, a dedicated team is already poised to act, minimizing business disruption and containing the damage. This makes their solution one of the best dark web monitoring services for businesses that cannot afford security gaps or delayed responses.
Key Differentiators and Comprehensive Features
Defend IT Services goes far beyond basic credential scanning. Their service is built on a multi-layered security framework managed by a 24/7 Security Operations Center (SOC). This ensures continuous vigilance over your entire digital footprint.
- Integrated Threat Intelligence: The service continuously scans dark web forums, criminal marketplaces, and data leak sites for any mention of your company's domains, employee credentials, or sensitive intellectual property. This intelligence is fed directly into their broader security strategy.
- 24/7 SOC and Incident Response: This is the service's cornerstone. A dedicated SOC provides around-the-clock monitoring. When a threat is validated, their incident response team takes immediate action to contain the threat, isolate affected systems, and begin remediation, drastically reducing the adversary's dwell time.
- Comprehensive Cybersecurity Suite: Dark web monitoring is just one piece of the puzzle. The service also includes endpoint detection and response (EDR), managed firewalls, cloud security management, and regular vulnerability assessments to harden your defenses proactively.
- Customized Security Roadmaps: Understanding that security is not one-size-fits-all, Defend IT Services develops tailored strategic roadmaps. These plans align security controls and investments directly with your specific business objectives and critical compliance requirements, such as HIPAA or CMMC. This strategic approach is particularly beneficial for businesses in regulated industries that need to demonstrate due diligence.
Key Insight: The true value of Defend IT Services is its shift from a reactive "alert-only" model to a proactive "detect-and-respond" partnership. Businesses gain not just a tool, but a fully managed security team dedicated to ensuring their operational resilience.
Ideal Use Cases and Practical Implementation
This managed service is an ideal fit for SMEs in regulated sectors like healthcare and finance, as well as any growing business that lacks dedicated IT security staff but handles sensitive data. The implementation process is hands-on, beginning with a thorough assessment of your current environment to identify vulnerabilities and business risks. From there, the team deploys the necessary tools and integrates them into their 24/7 monitoring system, providing a seamless transition to a more secure posture.
As a local, veteran-owned provider based in San Antonio, they emphasize trust and accountability. This focus is a significant advantage for organizations that value responsive, hands-on support. Businesses interested in this comprehensive protection model can explore the benefits detailed in this article about managed IT and cybersecurity services for San Antonio businesses.
Pros & Cons
| Strengths | Considerations |
|---|---|
| Active 24/7 Response: Threat monitoring is coupled with immediate incident remediation by a dedicated SOC. | Geographically Focused: On-site support is centered around San Antonio, Texas. |
| All-in-One Security: Combines dark web scanning with EDR, firewalls, and cloud security in one managed package. | Custom Pricing: Service tiers and costs are not public; a direct consultation is required for a quote. |
| Strategic and Compliant: Customized roadmaps align security measures with business goals and regulatory needs. | |
| Hands-On Partnership: Local, responsive support model is ideal for building a trusted security relationship. |
Learn more by visiting Defend IT Services.
2. ZeroFox
ZeroFox carves out a significant space in the market by offering an enterprise-grade external cybersecurity platform that extends beyond simple alerts. It provides a comprehensive, 24/7 managed service that monitors a vast landscape, including the deep and dark web (TOR, I2P), paste sites, criminal marketplaces, and even ephemeral chat platforms like Telegram and Discord. This solution is particularly well-suited for mid-market and enterprise organizations that require a robust defense against credential theft, PII exposure, and sophisticated brand abuse.
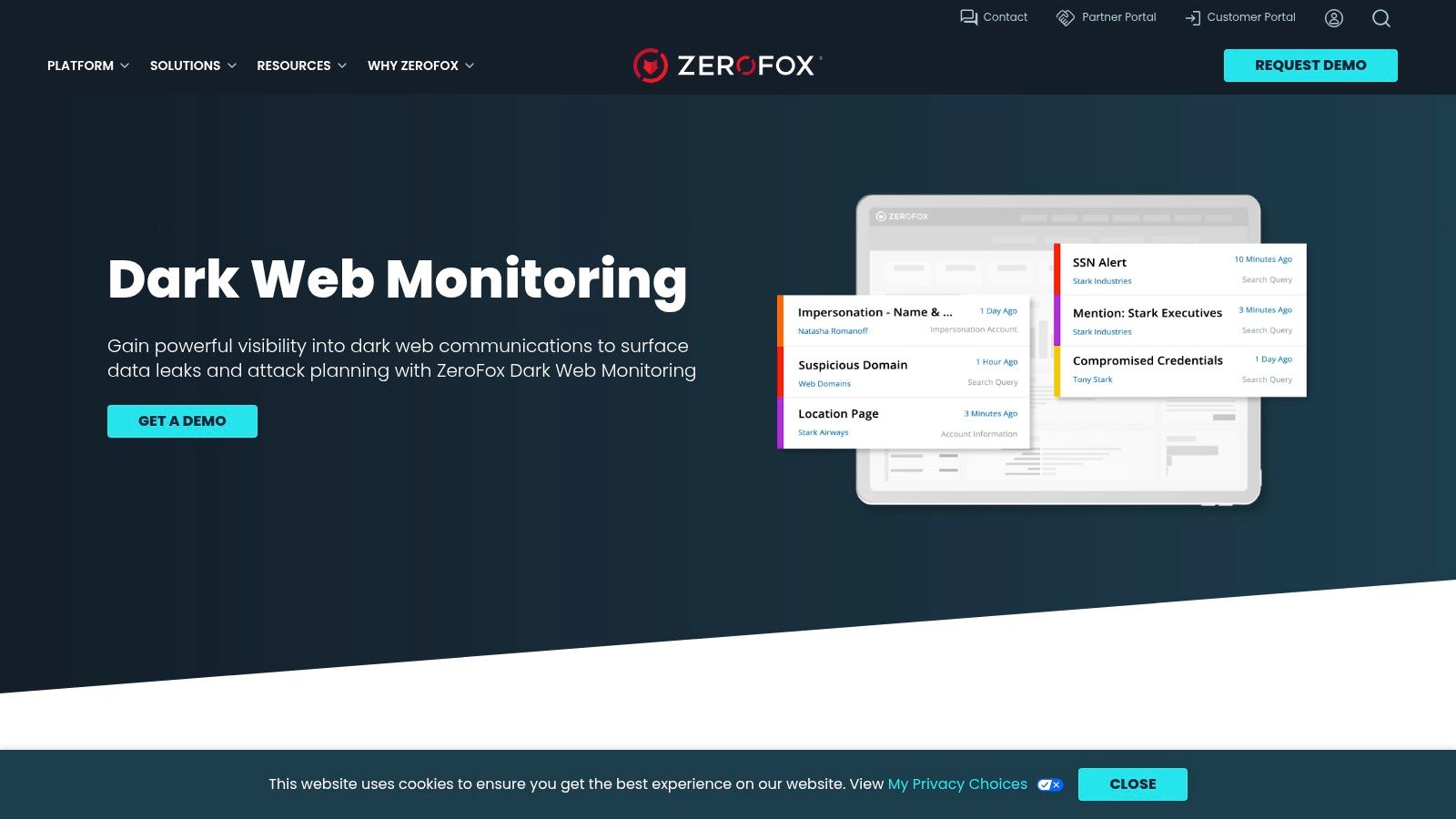
The platform's key differentiator is its powerful combination of automated data collection and human-operated analysis. While technology casts a wide net, ZeroFox's team of dedicated analysts vets and enriches the findings. This human-in-the-loop approach ensures that the alerts sent to your security team are high-fidelity, contextualized, and include actionable next steps, significantly reducing alert fatigue and false positives.
Key Features and Strengths
ZeroFox is recognized as one of the best dark web monitoring services due to its end-to-end capabilities, which include not just monitoring but also remediation.
- Human-Vetted Intelligence: Instead of raw data dumps, you receive SOC-vetted alerts complete with the original thread and context. This allows your team to understand the immediate threat and its potential impact.
- Integrated Takedown Services: When stolen data or fraudulent brand impersonations are discovered, ZeroFox doesn't just notify you. Their team actively works to take down the malicious content, providing a crucial service that many competitors lack.
- Holistic Coverage: The platform monitors for a wide range of threats:
- Credential Exposure: Stolen usernames and passwords.
- Payment Data: Compromised credit card numbers and financial information.
- Executive Targeting: Threats and PII related to key personnel.
- Brand Abuse: Phishing sites, domain spoofing, and logo misuse.
- Security Tooling Integration: ZeroFox seamlessly integrates with your existing security ecosystem (SIEM, SOAR, etc.), allowing for automated workflows and a more unified security posture.
Pricing and Ideal Use Case
ZeroFox operates on an enterprise sales model, meaning pricing is quote-based and requires a consultation or demo. There are no public price lists, which reflects its focus on customized solutions for larger organizations rather than individual consumers or very small businesses.
Expert Insight: The true value of ZeroFox lies in its blend of brand protection, threat intelligence, and dark web monitoring. For a mid-sized company in a regulated industry like finance or healthcare, this unified approach simplifies vendor management and provides a more cohesive view of external threats.
Pros & Cons
| Pros | Cons |
|---|---|
| Comprehensive platform combining multiple security functions. | Pricing is opaque and quote-based only. |
| Human-analyst vetting reduces false positives. | Not suitable for individual consumers or micro-businesses. |
| Includes active takedown services for remediation. | The sales process is more involved than self-service options. |
| Strong industry reputation and G2 leader badges. |
For businesses needing more than just a data feed, ZeroFox provides a managed intelligence and response service that actively mitigates threats discovered on the dark web.
Website: https://www.zerofox.com/products/dark-web-monitoring/
3. Recorded Future
Recorded Future positions itself as a premium intelligence company, offering a comprehensive suite of tools that go far beyond basic dark web scanning. Its Intelligence Cloud is designed for enterprises that need deep, contextualized insights into external threats. The platform monitors an extensive range of sources, including dark web forums, criminal marketplaces, ransomware leak sites, and malware-associated data logs, to provide a holistic view of an organization's exposed attack surface. This service is ideal for mature security teams looking to proactively hunt for threats rather than just react to alerts.

The platform’s core strength lies in its ability to connect disparate pieces of information and assign a risk score, helping teams prioritize their response efforts effectively. Instead of just flagging a compromised credential, Recorded Future provides context on the threat actor, the malware used, and potential links to other ongoing campaigns. This level of detail transforms raw data into actionable intelligence, a critical component for growing businesses that understand the importance of cybersecurity.
Key Features and Strengths
Recorded Future is considered one of the best dark web monitoring services for organizations that require a full-fledged threat intelligence program, not just a monitoring tool.
- Enterprise-Grade Context: The platform doesn't just find stolen data; it enriches it with intelligence about the source, associated malware, and threat actor TTPs (Tactics, Techniques, and Procedures).
- Comprehensive Intelligence Modules: Its solution is broken down into specific use cases, allowing businesses to focus on what matters most:
- Identity Intelligence: Detects and remediates compromised employee and customer credentials.
- Brand Intelligence: Monitors for brand impersonation, phishing domains, and reputational threats.
- Third-Party Intelligence: Assesses the dark web risk exposure of vendors and supply chain partners.
- Automated Workflows: Recorded Future integrates directly with security tools like SIEM, SOAR, and IAM platforms. This allows for automated remediation actions, such as forcing password resets for exposed credentials.
- Proactive Threat Hunting: The platform provides the tools and data necessary for security teams to actively hunt for threats and understand the landscape of risks specific to their industry and geography.
Pricing and Ideal Use Case
Similar to other enterprise-focused solutions, Recorded Future uses a quote-based pricing model. Access to its platform requires engaging with their sales team for a demo and a tailored proposal. This approach is best suited for mid-market and large enterprises with dedicated security operations or threat intelligence teams that can leverage the platform's full capabilities.
Expert Insight: Recorded Future truly shines in its ability to provide high-fidelity, contextual intelligence. For a financial institution or a large tech company, knowing how a credential was stolen (e.g., via Redline Stealer malware) is just as important as knowing it was stolen. This context drives more effective security strategy.
Pros & Cons
| Pros | Cons |
|---|---|
| Exceptional threat intelligence context and depth. | Pricing is quote-based and tailored to enterprises. |
| Broad scope covering brand, identity, and third-party risk. | The extensive feature set may have a steep learning curve. |
| Strong integration capabilities for automated remediation. | Overkill for small businesses needing basic credential alerts. |
| Highly regarded with strong Gartner Peer Insights ratings. |
For organizations ready to move from a reactive to a proactive security posture, Recorded Future provides the deep intelligence needed to anticipate and neutralize threats before they escalate.
Website: https://www.recordedfuture.com/products/identity-intelligence
4. SpyCloud
SpyCloud distinguishes itself by focusing on recaptured data from sophisticated criminal sources that often go undetected by conventional scanners. Its core strength lies in its massive, proprietary dataset of stolen credentials, cookies, and PII sourced directly from malware-stealer logs and breach data circulating in closed criminal communities. This approach provides enterprises with early warnings about compromised employee and customer accounts before that data can be weaponized for fraud or network intrusions.

The platform is designed to power proactive security measures rather than just reactive alerts. By identifying malware-infected devices that have exfiltrated sensitive data, SpyCloud enables security teams to not only reset compromised credentials but also address the root cause of the infection. This focus on post-infection forensics makes it an invaluable tool for preventing session hijacking, ransomware attacks, and online fraud.
Key Features and Strengths
SpyCloud is recognized as one of the best dark web monitoring services for its actionable intelligence and deep integration capabilities. Its solutions are structured to address different organizational needs, from internal workforce protection to external customer account security.
- Proprietary Recaptured Data: Gains access to data from malware logs and exclusive criminal forums, often identifying exposures months before they appear on public breach sites.
- Actionable Forensics: Beyond credentials, it recaptures data from malware stealers that includes system information, IP addresses, and session cookies, helping teams identify and remediate infected devices.
- Tiered Solutions: Offers targeted products for different use cases:
- Enterprise Protection: Monitors employee credentials to prevent network breaches.
- Consumer Risk Protection: Helps businesses protect their customer accounts from takeover.
- Investigations: Provides security and law enforcement with enriched data for threat analysis.
- Powerful Integrations: Seamlessly integrates with security stacks via robust APIs, SIEM/SOAR connectors, Maltego transforms, and dedicated notebooks for investigation and automation. Learn more about the importance of integrating top-tier services like SpyCloud.
Pricing and Ideal Use Case
SpyCloud’s pricing is quote-based and tailored to enterprise needs. The cost is structured based on the specific solution, such as the number of employee or customer accounts monitored, investigator seats, or API query volume. This model is ideal for mid-market to large enterprises, particularly those in finance, e-commerce, and technology, that need to prevent account takeover and protect against malware-driven threats.
Expert Insight: The real power of SpyCloud is its ability to tie a compromised credential back to the malware-infected device that stole it. This is a game-changer for incident response, as it allows teams to neutralize the entry point instead of just playing whack-a-mole with password resets.
Pros & Cons
| Pros | Cons |
|---|---|
| Unique access to malware-stealer data. | Pricing is enterprise-level and not for individuals. |
| Provides actionable context beyond just credentials. | Some users report a need to manually triage older breach data. |
| Flexible APIs for easy integration into existing workflows. | The sales and onboarding process is more involved than self-service tools. |
| Positive G2 reviews for timely alerts and usability. |
For organizations seeking to move beyond standard breach monitoring and proactively combat threats originating from malware, SpyCloud provides uniquely deep and actionable intelligence.
Website: https://spycloud.com/pricing/
5. Aura
Aura distinguishes itself in the crowded cybersecurity market by bundling dark web monitoring into an all-in-one digital safety suite designed for individuals and families. Instead of focusing solely on enterprise-level threat intelligence, Aura provides an accessible, consumer-friendly service that combines identity theft protection, financial fraud monitoring, and device security into a single subscription. This makes it an excellent choice for individuals, couples, or households seeking comprehensive protection against a wide range of personal digital threats.
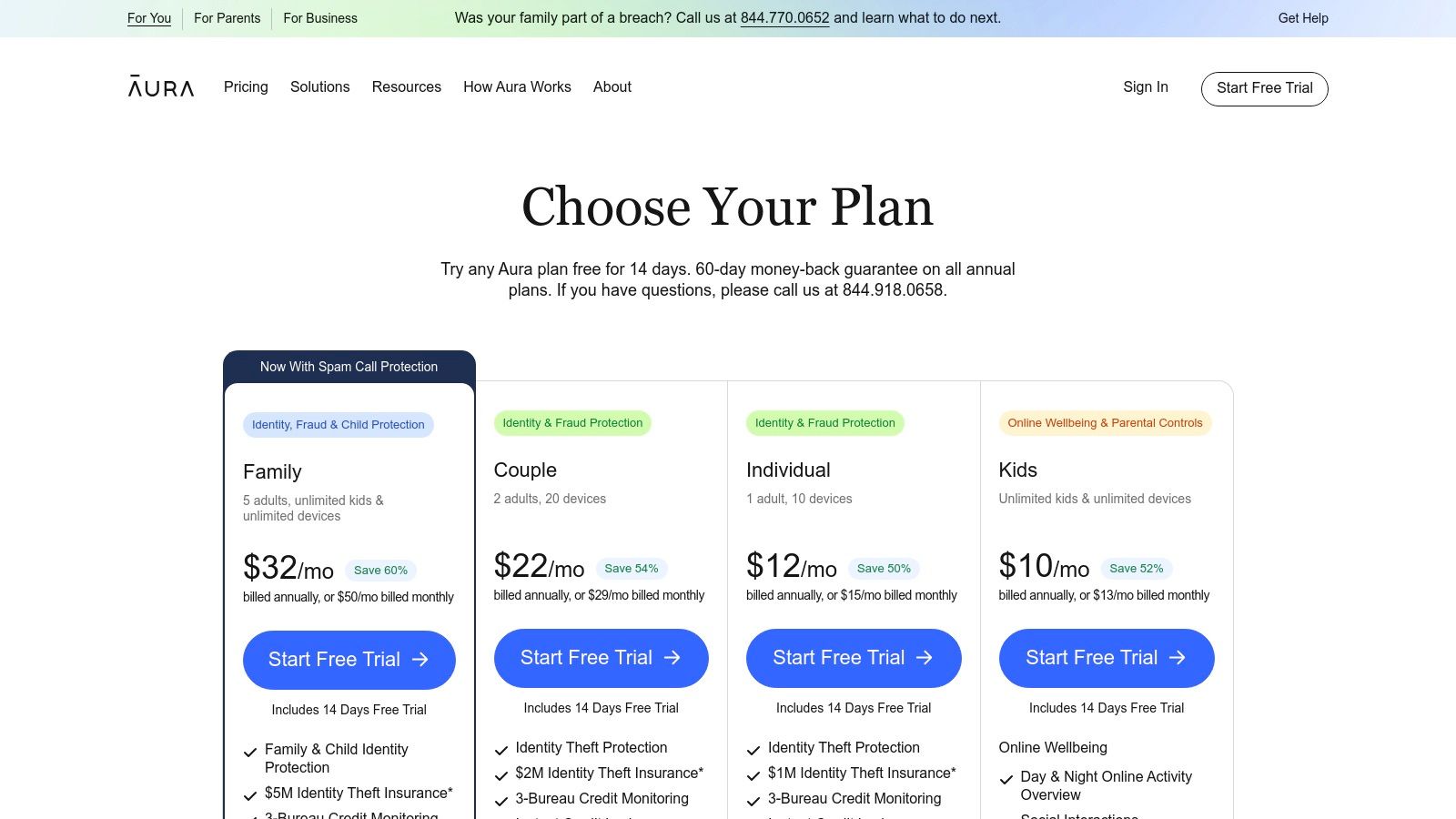
The platform's core value proposition is its simplicity and breadth. Aura continuously scans the dark web for your personal identifiable information (PII), including Social Security numbers, email addresses, and passwords. What sets it apart is how this monitoring is integrated with other critical security features. For example, if your credentials are found, you are not just notified; you can immediately use the included password manager to update your accounts and leverage the 3-bureau credit monitoring to watch for fraudulent activity.
Key Features and Strengths
Aura has earned its place among the best dark web monitoring services by making sophisticated protection straightforward and affordable for the average consumer.
- Holistic Identity Protection: Aura bundles several services that are often sold separately:
- Dark Web Monitoring: Real-time alerts for your PII, financial information, and credentials.
- 3-Bureau Credit Monitoring: Keeps tabs on your Equifax, Experian, and TransUnion reports with monthly score updates and an instant Experian credit lock.
- Data Broker Removal: Automates the process of requesting your information be removed from people-search sites, reducing your public footprint.
- Comprehensive Device Security: Each plan includes a full suite of tools to protect your hardware and online activity, including a VPN, antivirus software, and a password manager.
- Family-Focused Plans: Aura offers plans that cover individuals, couples, and families (up to five adults and unlimited kids), making it a cost-effective solution for protecting an entire household.
- Financial and Transaction Monitoring: The service links to your financial accounts to alert you to unusual spending, helping you catch fraud quickly.
Pricing and Ideal Use Case
Aura offers transparent, tiered pricing for individuals, couples, and families, with significant discounts for annual billing. Plans are clearly listed on their website, and they frequently offer a 14-day free trial and a 60-day money-back guarantee on annual plans. This makes it a low-risk option for those wanting to test the service.
Expert Insight: Aura's strength lies in its "set it and forget it" value proposition for families. For the price of what some companies charge just for dark web monitoring, Aura provides that plus credit monitoring, a VPN, antivirus, and data broker removals. It's an ideal choice for a user who wants one subscription to handle all major aspects of their digital safety without becoming a security expert.
Pros & Cons
| Pros | Cons |
|---|---|
| All-in-one bundle provides excellent value. | Not designed for business or enterprise use cases. |
| Transparent, published pricing with a free trial. | Credit reports are limited to monthly scores and annual full reports. |
| Family plans offer comprehensive household coverage. | Primarily focused on the U.S. market. |
| Includes valuable extras like a VPN and antivirus. |
For individuals and families who need an easy-to-manage, comprehensive digital protection service, Aura provides a powerful and user-friendly solution that goes well beyond basic dark web alerts.
Website: https://www.aura.com/pricing
6. Norton 360 with LifeLock
Norton 360 with LifeLock takes a consumer-first approach, bundling its reputable device security suite with the powerful identity theft protection services of LifeLock. This all-in-one solution is designed for individuals and families who want a single subscription to cover device security (antivirus, VPN), privacy monitoring, and dark web surveillance. Instead of focusing solely on enterprise-level threats, it protects personal information like Social Security numbers, bank accounts, and gamer tags, making it a household name in personal digital safety.
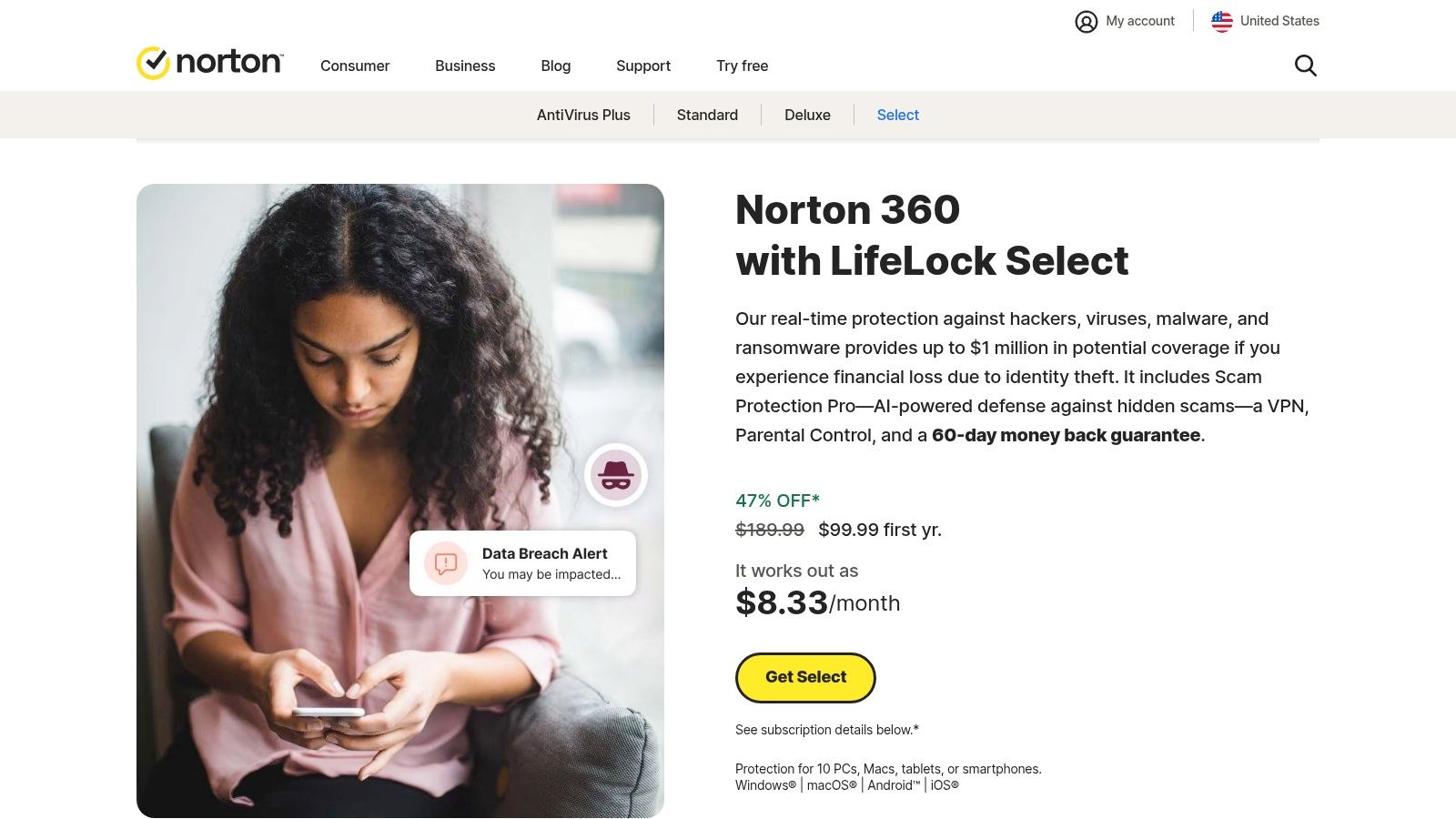
The platform's primary differentiator is its integration of comprehensive identity theft remediation and insurance. While many services alert you to a problem, LifeLock provides U.S.-based Identity Restoration Specialists to help resolve issues. This hands-on support, combined with substantial financial coverage for stolen funds and expenses, provides a full-circle safety net that goes far beyond simple data monitoring.
Key Features and Strengths
Norton 360 with LifeLock is considered one of the best dark web monitoring services for consumers due to its holistic approach to personal and family digital security.
- Comprehensive Identity Alerts: The service monitors for your personal information across the dark web and sends alerts via its mobile app and web dashboard for a wide range of data types, including credit cards, driver's licenses, and SSNs.
- Integrated Device Security: Each plan includes Norton's award-winning antivirus protection, a secure VPN for online privacy, a password manager, and parental controls, simplifying vendor management for families.
- Credit Monitoring and Financial Alerts: Higher-tier plans include one-bureau or three-bureau credit monitoring, alerts on 401(k) and investment account activity, and home title monitoring to guard against fraud.
- Identity Theft Insurance & Restoration: Plans come with a Million Dollar Protection™ Package, which includes coverage for stolen funds and personal expenses, with limits reaching up to $3 million on the top-tier plan.
Pricing and Ideal Use Case
Norton 360 with LifeLock offers several tiered plans, with pricing often starting with significant introductory discounts for the first year. The Select plan is a solid entry point, while the Ultimate Plus plan provides the most comprehensive coverage, including three-bureau credit monitoring. This model is ideal for individuals, couples, and families seeking a unified solution to manage device security and identity protection under one roof. It is less suited for businesses needing employee-wide or corporate asset monitoring.
Expert Insight: The true value of Norton 360 with LifeLock is its convenience and the peace of mind offered by its restoration services. For a family, being able to protect multiple phones, laptops, and identities through a single, well-known provider is a major advantage over piecing together separate services.
Pros & Cons
| Pros | Cons |
|---|---|
| One vendor for device security and identity protection. | Plan structure and renewal pricing can be complex. |
| Well-known brand with widely reviewed features. | Renewal prices are often significantly higher than intro rates. |
| Frequent introductory discounts are available for new U.S. customers. | Key features like 3-bureau credit monitoring are locked in higher tiers. |
| Includes identity theft insurance and restoration specialists. | Primarily focused on the U.S. market. |
For individuals and families wanting a simple, trusted, and comprehensive package, Norton 360 with LifeLock offers a powerful combination of proactive monitoring and reactive support.
Website: https://us.norton.com/products/norton-360-lifelock-select
7. IdentityForce (a TransUnion company)
Backed by the power of credit bureau TransUnion, IdentityForce delivers a consumer-focused identity theft protection suite that includes robust dark web monitoring. This service is designed for individuals and families who want an always-on solution that not only scans the dark web but also integrates deeply with credit and financial account monitoring. By combining these elements, IdentityForce provides a holistic view of a user's digital and financial footprint, making it a strong contender for those seeking comprehensive personal protection.
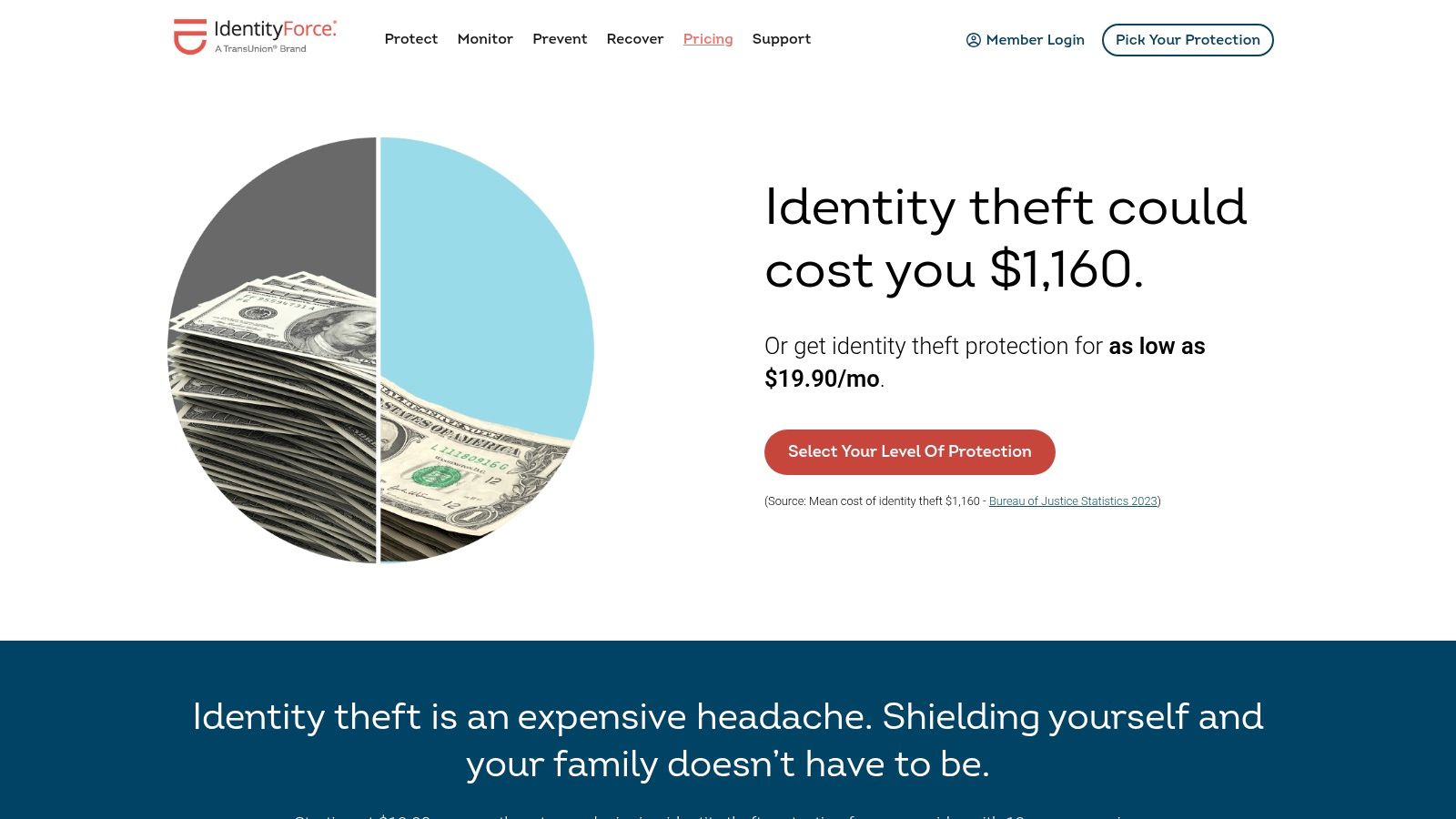
What sets IdentityForce apart in the consumer space is its dedication to actionable intelligence and hands-on support. When a piece of your information is found on the dark web, the platform doesn't just send a generic alert. It provides a granular risk score for each hit, helping you prioritize the most urgent threats. Furthermore, every plan includes access to U.S.-based, certified restoration specialists who will manage the entire recovery process on your behalf, a critical service that provides peace of mind in a stressful situation.
Key Features and Strengths
IdentityForce has solidified its reputation as one of the best dark web monitoring services for consumers by bundling powerful scanning technology with top-tier support and credit-focused features.
- Granular Dark Web Alerts: The platform continuously scans for your Social Security number, email addresses, phone numbers, and more. Each discovery is assigned a risk score to clarify its potential impact.
- Dedicated Restoration Specialists: If your identity is compromised, you get a dedicated U.S.-based specialist to handle the entire restoration process, saving you hundreds of hours of work.
- Comprehensive Credit Monitoring: The higher-tier UltraSecure+Credit plan includes daily monitoring and scores from TransUnion, plus quarterly reports and scores from all three major bureaus (Equifax, Experian, and TransUnion).
- Generous Insurance Coverage: Plans come with identity theft insurance, with the top-tier plan offering up to $2 million in coverage (coverage and availability vary by state) to reimburse stolen funds and related expenses.
- Mobile App and Alerts: Receive timely alerts directly on your mobile device, allowing you to react quickly to potential threats.
Pricing and Ideal Use Case
IdentityForce offers transparent, direct-to-consumer pricing with several tiers. The UltraSecure plan focuses on identity monitoring, while the UltraSecure+Credit plan adds the full suite of three-bureau credit monitoring services. Pricing is typically subscription-based, with monthly and annual options available. A 30-day trial is often offered for new users.
Expert Insight: The true value of IdentityForce for an individual or family is its combination of proactive monitoring and full-service restoration. While many services alert you to a problem, IdentityForce provides an expert to fix it, which is an invaluable benefit for those who lack the time or knowledge to navigate the complexities of identity recovery.
Pros & Cons
| Pros | Cons |
|---|---|
| Clear, published pricing and online signup. | The entry-level plan lacks 3-bureau credit monitoring. |
| Includes dedicated restoration specialists on all plans. | The comprehensive credit bundle plan is priced higher than some direct competitors. |
| 30-day trial is available on certain plans. | Primarily focused on U.S. consumers. |
| Strong credit monitoring options from a trusted name (TransUnion). |
For individuals and families wanting a one-stop-shop for dark web surveillance, credit monitoring, and expert-led identity restoration, IdentityForce offers a reliable and comprehensive solution.
Website: https://www.identityforce.com/identity-protection-pricing
Top 7 Dark Web Monitoring Services Comparison
| Solution | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊⭐ | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Managed IT Services — DefendIT Services | Moderate — hands‑on deployment and customized roadmaps | Managed subscription plus local on‑site support; integrates with existing IT | 24/7 threat monitoring, rapid incident response, compliance support | Growing SMBs wanting a single local partner for IT + security | ⭐ Unified managed IT + layered cybersecurity; rapid IR; local, veteran‑owned support |
| ZeroFox | Low–Moderate — SaaS with analyst workflows and integrations | Enterprise license, SOC/tooling integrations, analyst review capacity | Dark web visibility, analyst‑vetted alerts, takedown actions | Mid‑market & enterprise brand protection and credential exposure monitoring | ⭐ Human‑operated analysis + automated collection; SOC‑vetted alerts and takedowns |
| Recorded Future | Moderate–High — multi‑module platform, integration with SOAR/IAM | Enterprise platform licenses, integration effort, analyst training | Real‑time alerts, risk scoring, automated remediation workflows | Organizations needing broad threat intelligence and third‑party risk monitoring | ⭐ Rich context & risk scoring; automated workflows into security stacks |
| SpyCloud | Low–Moderate — API/UI rollout; integrations for automation | Subscription with API access; integration into IAM/forensics tools | Fast detection of compromised credentials and enriched identity data | Enterprises focused on workforce/customer account protection and investigations | ⭐ Large proprietary breach dataset; flexible APIs for automation |
| Aura | Low — consumer SaaS self‑setup | Consumer subscription for individuals/families; minimal IT overhead | Dark web alerts + credit monitoring + device security bundle | Consumers and families seeking an all‑in‑one identity/security package | ⭐ Published pricing, device bundle (VPN/AV/password manager), trial available |
| Norton 360 with LifeLock | Low — consumer setup, device installations required | Consumer subscription; devices across household; higher tiers add credit services | Device protection plus identity alerts and credit/financial monitoring (tiers vary) | Families wanting combined antivirus and identity theft protection | ⭐ Single vendor for AV + identity; broad retail presence and frequent promotions |
| IdentityForce (TransUnion) | Low–Moderate — consumer onboarding with optional credit add‑ons | Subscription with optional 3‑bureau credit; mobile app and restoration team | 24/7 dark web monitoring with risk scores and dedicated restoration support | Consumers who prioritize restoration services and frequent credit reporting | ⭐ Published pricing, dedicated restoration specialists, granular risk scoring |
Choosing Your Shield: How to Select the Right Dark Web Monitoring Service
Navigating the landscape of dark web monitoring can feel like venturing into the very digital underworld you're trying to defend against. We've explored a range of powerful tools, from comprehensive managed services like DefendIT to specialized threat intelligence platforms like Recorded Future and consumer-focused identity protectors like Aura and Norton 360. The key takeaway is clear: proactive monitoring is no longer a luxury but a fundamental component of a modern cybersecurity strategy for any business.
The threat isn't abstract; it's the potential exposure of your customer database, the leaking of executive credentials, or the sale of your proprietary intellectual property on a hidden marketplace. Each service we've detailed offers a unique shield. ZeroFox excels at external attack surface management, while SpyCloud focuses on recapturing compromised assets post-breach. IdentityForce, backed by TransUnion, provides robust identity theft and credit monitoring, making it a strong choice for businesses prioritizing employee benefits and protection. The challenge isn't finding a solution, but selecting the one that aligns precisely with your organization's specific vulnerabilities, operational capacity, and regulatory obligations.
A Practical Framework for Your Decision
Making the right choice from the array of best dark web monitoring services requires a strategic internal assessment. Before committing to a platform, your team should work through a structured evaluation process. This ensures your investment directly addresses your most significant risks and delivers tangible value.
Consider these critical factors to guide your selection:
- Scope of Monitoring: Do you need to monitor for corporate credentials, customer PII, intellectual property, or all of the above? A financial institution's needs will differ vastly from a local healthcare provider or a multi-location retail business.
- Actionability of Alerts: Receiving an alert is only half the battle. Evaluate how each service helps you respond. Do they offer clear remediation steps? Do they provide managed response services to contain threats on your behalf? An alert without a clear action plan is just noise.
- Integration and Scalability: How well will the service integrate with your existing security stack, such as your SIEM or EDR solutions? For growing San Antonio businesses, it’s crucial to choose a solution that can scale with you, whether you're migrating to the cloud or adding new endpoints.
- Resource Allocation: Be realistic about your internal IT capacity. If you have a dedicated security team, a platform like Recorded Future might be a perfect fit. If you operate with a leaner team, a fully managed service that includes 24/7 monitoring and response is a more practical and effective choice.
Beyond technical features, the proactive defense of your digital footprint often overlaps with how your brand is perceived online. While dark web monitoring focuses on direct threats and data leakage, a holistic security posture also involves managing public-facing information. When evaluating options for protecting your digital presence, you might also consider comparing the best online reputation management software to ensure all angles of your online identity are secure.
Ultimately, choosing a dark web monitoring service is an investment in resilience. It's about transforming your security posture from reactive to proactive, gaining visibility into threats before they escalate into costly breaches. By carefully matching your unique business needs-whether it's HIPAA compliance, protecting a remote workforce, or securing financial data-to the strengths of these services, you can forge a powerful defense against the hidden threats of the digital age.
Don't leave your organization's most sensitive data exposed to the hidden corners of the web. For comprehensive, 24/7 dark web monitoring combined with end-to-end managed IT and security services, partner with Defend IT Services. We provide the expert oversight and rapid response your business needs to stay ahead of threats. Learn more at Defend IT Services.

