Compliance management is simply the formal way your organization makes sure it's following all the relevant laws, regulations, and industry standards that apply to it. Think of it as the collection of policies and procedures that keeps your business running ethically and legally, protecting you from crippling fines and a damaged reputation.
Deconstructing Compliance Management
At its heart, compliance management is the art and science of playing by the rules.
Let's use an analogy. Imagine you're running a professional kitchen. You have to follow mandatory health codes (these are the external laws) to keep your doors open. You also need to stick to specific food handling protocols (industry regulations). And finally, you have your own secret recipes (internal policies) to ensure you deliver a consistent, high-quality meal every time.
Compliance management is the system that makes sure all three of those things happen without a hitch. It's not a one-and-done project or a dusty binder on a shelf; it's an active, ongoing process. It's about figuring out which rules apply to you and weaving them into the fabric of your daily operations. This proactive mindset turns what could be a huge source of anxiety into a genuine business advantage.
More Than Just Following Rules
A solid compliance program is about so much more than just checking boxes. It’s about creating a culture of integrity and accountability that runs through every part of your company. When you get it right, the benefits are clear:
- Reduces Business Risk: It helps you spot and address potential legal, financial, and operational threats before they can do any real harm.
- Builds Customer Trust: Showing a real commitment to compliance, especially around data privacy, proves to your customers that you take their security seriously. That's a huge differentiator in today's market.
- Improves Operational Efficiency: When policies and procedures are clear, you eliminate guesswork, cut down on errors, and create smoother, more consistent business processes.
A strong compliance framework doesn't just prevent penalties; it creates a stable foundation for sustainable growth. It transforms regulatory obligations from a burden into a blueprint for building a more resilient and trustworthy business.
To get a deeper look at how compliance and risk management work together to protect your business, check out this comprehensive guide to compliance risk management. Understanding that link is the first step toward building a program that truly works.
The Three Layers of Compliance
Every business, big or small, has to navigate a unique set of rules that fall into three main categories. A big part of understanding compliance management is seeing how these layers fit together.
- External Laws and Regulations: These are the non-negotiables set by governments. Think GDPR for data privacy in Europe or HIPAA for healthcare in the U.S.
- Industry Standards: These are requirements specific to your sector, like PCI DSS for any business that handles credit card payments. You have to follow them to stay in good standing.
- Internal Policies: These are the rules you create for yourself. They range from your employee handbook and code of conduct to specific security protocols designed to protect your company's information.
An effective compliance management program brings all three layers together in harmony, ensuring your team knows exactly what's expected of them and has the tools to deliver on those expectations every day.
The Building Blocks of a Strong Compliance Program
A solid compliance program isn’t a single document you create and then stuff in a filing cabinet. It’s a living, breathing system made up of several key components, all working together. Think of it like building a secure house—you don’t just put up walls and call it a day. You need a solid foundation, a strong frame, locks on the doors, and an alarm system. They all have to function in unison to offer real protection.
In the same way, effective compliance management is built on a set of core pillars. Each one plays a unique role, but it's their combined strength that turns the abstract idea of "compliance" into a practical, day-to-day reality that truly safeguards your business.
Start With a Risk Assessment
Before you can build your defenses, you have to know what you’re defending against. A risk assessment is your reconnaissance mission—a systematic process of identifying, analyzing, and evaluating the compliance threats your organization faces. It's the diagnostic phase where you pinpoint the weak spots in your operations.
This isn’t about guesswork. It involves a hard look at your business processes, the data you handle, and the specific regulations that apply to you. The central question is, "Where are we vulnerable?" The goal is to come away with a prioritized list of risks based on their potential impact and likelihood, so you can focus your resources where they matter most.
A risk assessment is your strategic map. Without one, you're essentially flying blind, wasting time and money on controls you might not even need while leaving critical vulnerabilities exposed.
Develop Clear Policies and Procedures
Once you understand your risks, the next step is to write the rulebook for your team. Policies are the high-level statements that define your company’s official stance on things like data privacy or acceptable use. They set the direction and spell out the expectations.
Procedures, on the other hand, get into the nitty-gritty. They are the detailed, step-by-step instructions explaining how to follow those policies. For example, a procedure would outline the exact process for handling a customer's request to delete their personal data. Having both eliminates confusion and ensures everyone knows exactly what they're supposed to do.
Implement Technical and Administrative Controls
With your rulebook in hand, it’s time to actually build your defenses. Controls are the specific safeguards you put in place to knock down the risks you identified earlier. They generally fall into two main categories:
- Technical Controls: These are the technology-based solutions you deploy. Think firewalls, data encryption, multi-factor authentication, and access control systems that restrict who can see sensitive information.
- Administrative Controls: These are the people-focused measures. This includes things like employee security awareness training, mandatory background checks, and having a well-documented incident response plan ready to go.
The right mix of technical and administrative controls creates a layered defense that's much tougher to break through. For growing businesses, understanding the importance of cybersecurity is the crucial first step toward implementing the right technical safeguards.
Monitor, Audit, and Report Continuously
A compliance program is never "done." It requires constant attention to stay effective. Continuous monitoring involves the ongoing, day-to-day checks to make sure your controls are working as intended. This might involve automated tools that scan for vulnerabilities or regular reviews of who is accessing sensitive files.
Audits are more formal, periodic assessments—often conducted by your internal team or a third-party expert—that provide an objective "health check" of your compliance posture. Finally, reporting keeps key stakeholders, from department heads to the C-suite, in the loop. They need to know how the program is performing, what issues have been found, and what’s being done to fix them. This entire cycle ensures your program can adapt to new threats and changing regulations.
The rules a business must follow come from multiple places, as this flowchart shows.
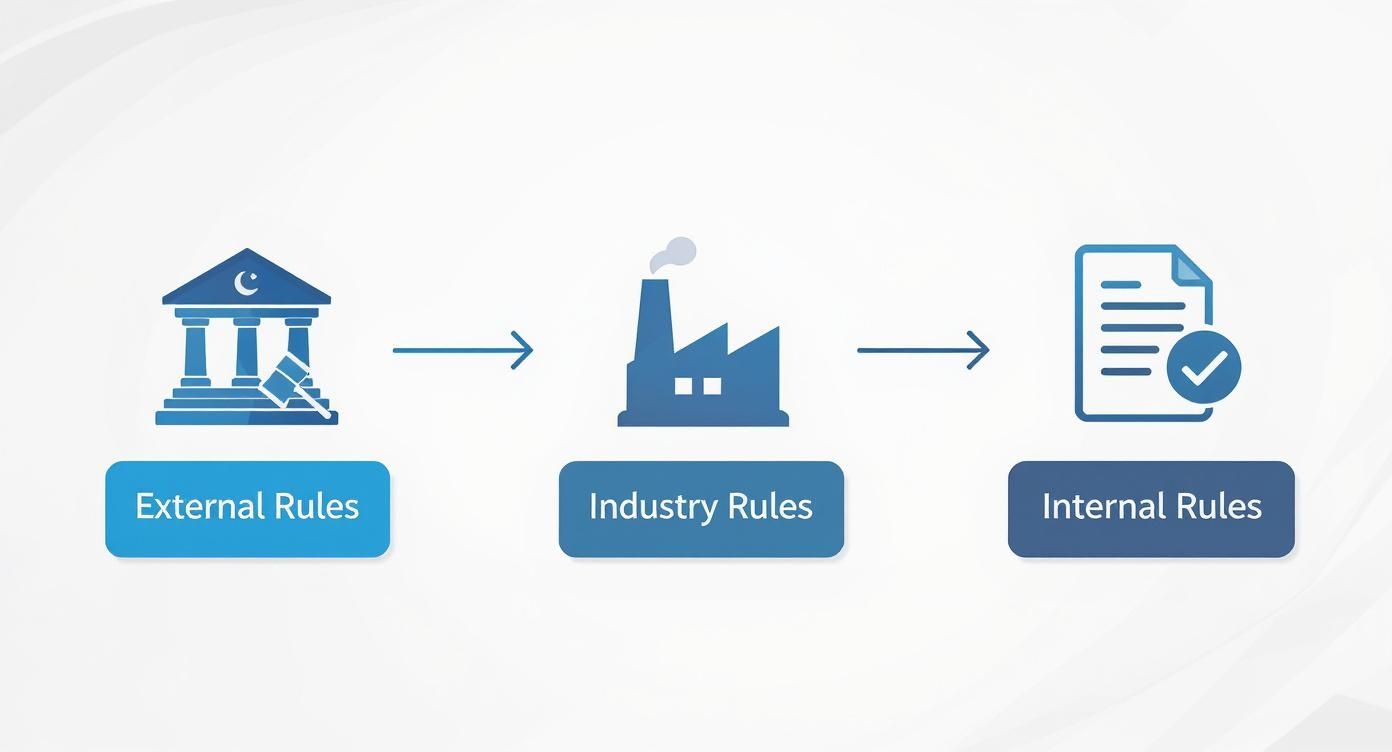
This shows how a company's internal rules are ultimately shaped by broader industry standards and external legal requirements.
Keeping up with these layers is a massive challenge. A recent PwC survey found that a staggering 85% of organizations feel that compliance requirements have gotten more complex over the last three years. This isn’t isolated to one sector; it’s a feeling shared across almost every industry. These five building blocks—risk assessment, policies, controls, monitoring, and reporting—form a powerful, cyclical process. Each one feeds into the next, creating a dynamic system that makes your business stronger and more resilient over time.
4. A Guide to Common Compliance Frameworks
https://www.youtube.com/embed/QiMBPdchl1w
Stepping into the world of compliance can feel like you're trying to decipher a secret code. You're immediately hit with a barrage of acronyms—HIPAA, PCI DSS, SOC 2, NIST. It's enough to make any business owner’s head spin. But these frameworks aren't just bureaucratic hurdles; they're essential roadmaps for protecting your data and earning customer trust.
A great way to think about them is like different types of building codes. A single-family home has one set of rules, a hospital has another, and a massive skyscraper has a completely different, more complex set. Each code is tailored to the building's purpose and the people inside it. Compliance frameworks work the same way, providing specific rules based on the kind of data you handle and your industry.
Knowing which "building code" applies to your business is the first critical step. It ensures you're not just going through the motions but are building a genuinely secure foundation that protects both your company and your clients from very real threats.
HIPAA: The Standard for Health Information
For any organization that touches Protected Health Information (PHI), the Health Insurance Portability and Accountability Act (HIPAA) is non-negotiable. This doesn't just apply to hospitals and doctor's offices, but also to their "business associates"—think of an IT provider, a billing company, or a cloud storage service that has access to patient data.
At its core, HIPAA is all about maintaining the confidentiality, integrity, and availability of sensitive health records. It lays down firm rules for how that data is stored, who can see it, and how it's shared.
- Who Needs It: Healthcare providers, insurance companies, and any third-party vendor that works with them and their patient data.
- Why It Matters: The penalties for non-compliance are severe. Fines can reach up to $1.5 million per violation per year, not to mention the immense reputational damage that can shatter patient trust overnight.
PCI DSS: Securing Every Card Payment
If your business takes credit or debit card payments—whether online, in-person, or over the phone—you must meet the Payment Card Industry Data Security Standard (PCI DSS). This isn't a federal law, but rather a set of security standards mandated by the major card brands like Visa, Mastercard, and American Express.
Think of it as a security contract. To keep the privilege of accepting their cards, you agree to protect cardholder data by following their specific rules.
PCI DSS is all about creating a secure bubble around cardholder data. It requires specific safeguards like network firewalls, strong data encryption, and tight access controls to stop credit card fraud in its tracks.
SOC 2: Building Trust for Service Organizations
The Service Organization Control 2 (SOC 2) framework is for technology companies and cloud service providers that store or process their clients' data. A SOC 2 report is essentially a stamp of approval from an independent auditor, confirming that a company has the right controls in place to keep that data safe.
Unlike the rigid, one-size-fits-all nature of some other frameworks, SOC 2 is flexible. It's built around five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. A business can be audited against just one or all five, depending on the promises it makes to its customers.
- Who Needs It: SaaS companies, cloud hosting providers, data centers, and managed IT service providers.
- Why It Matters: A clean SOC 2 report is often a deal-breaker for enterprise-level clients. It gives them the independent assurance they need to trust you with their valuable information.
Part of navigating these frameworks involves understanding related guidelines, like the NIST SP 800-88 data sanitization standard, which offers specific instructions for securely wiping data from old hardware.
Comparing Key Compliance Frameworks
With so many frameworks out there, it's easy to get confused about which ones apply to you. This table breaks down the most common ones to give you a clearer picture of where your business might fit.
| Framework | Primary Focus | Who Needs It? |
|---|---|---|
| HIPAA | Protecting patient health information (PHI). | Healthcare providers, insurers, and their business associates. |
| PCI DSS | Securing credit cardholder data during transactions. | Any business that accepts, processes, or stores card payments. |
| SOC 2 | Protecting customer data held by service providers. | SaaS companies, cloud providers, and managed service firms. |
| NIST | Providing a flexible framework of cybersecurity best practices. | Federal agencies and contractors; widely adopted by private sector as a gold standard. |
Each framework serves a distinct purpose, but they all share a common goal: to create a structured approach to managing risk and protecting sensitive information. Understanding the right one for your business is the first step toward building a resilient security posture.
Your SMB Roadmap to Implementing Compliance
For a small or midsize business, the very idea of a "compliance program" can sound intimidating and expensive. It conjures up images of endless paperwork, high-priced consultants, and software you don't have the time to learn. But it doesn't have to be that way.
Building a solid compliance foundation is completely achievable, even on a tight budget. The secret is to treat it like any other business project: break it down into practical, manageable steps. This isn't about achieving perfection overnight; it's about making steady, meaningful progress.
Think of it like building a sturdy fence. You wouldn't try to put the whole thing up in one afternoon. Instead, you'd dig one post hole at a time, making sure each one is solid before moving to the next. This roadmap follows that same principle.

Phase 1: Identify Your Obligations
You can't play by the rules if you don't know what game you're in. This first step is all about figuring out which specific regulations and standards actually apply to your business. Getting this right is critical—it defines the entire scope of your efforts from here on out.
Start by asking a few simple questions:
- What industry are we in? A healthcare provider has to worry about HIPAA, while a financial firm has its own unique rulebook.
- Do we take credit card payments? If the answer is yes, then PCI DSS isn't optional; it's a requirement.
- What kind of customer data do we handle? Storing personal information can easily pull you into the world of data privacy laws.
- Do we work with the government? Federal or state contracts almost always come with their own strict cybersecurity strings attached.
This initial discovery phase is your compass. It keeps you from wasting time on irrelevant standards and points you directly toward what matters for your business's legal and operational health.
Phase 2: Assign Clear Ownership
In a smaller company, you probably don't have a Chief Compliance Officer on staff, and that's okay. What truly matters is that one person is officially responsible for steering the ship. This individual becomes the go-to person for everything compliance-related.
This doesn't need to be a full-time role. It could be the owner, an office manager, or your IT lead. The key is making it official. When someone is clearly accountable, tasks don't get lost in the shuffle, and the whole initiative keeps moving forward.
Without clear ownership, a compliance program becomes a collection of good intentions with no one to drive them forward. Assigning a champion, even part-time, is the single most effective way to ensure progress.
Phase 3: Conduct a Baseline Assessment
Now that you know the rules and someone's in charge, it's time to see where you stand right now. A baseline assessment doesn't need to be a massive, complex audit. Think of it more as a practical self-check to find the biggest gaps between what you're doing and what you should be doing.
Create a simple checklist based on the frameworks you identified in Phase 1. For each requirement, ask two questions: "Are we doing this?" and "If so, how are we proving it?" This process will quickly highlight your areas of highest risk, giving you a clear, prioritized to-do list.
For many SMBs, this is a great time to lean on a partner. An expert in managed IT and cybersecurity services can make this assessment far more thorough and efficient, spotting things you might have missed.
Phase 4: Implement Essential Controls
It's time to roll up your sleeves and get to work. Using your assessment as a guide, start putting the most critical controls in place. This is where you turn your policies from ideas on paper into real-world actions. The goal here is to nail the fundamentals first.
Focus on foundational security measures that give you the most bang for your buck:
- Access Control: Make sure employees can only access the data and systems they absolutely need to do their jobs. Nothing more.
- Data Encryption: Protect your sensitive data with encryption, both when it's sitting on a server (at rest) and when it's being sent over the internet (in transit).
- Employee Training: Start a simple security awareness program. Teaching your team how to spot a phishing email and practice good data hygiene is one of the most powerful defenses you can build.
By tackling these core elements first, you immediately strengthen your security posture in a way that satisfies common requirements across many different compliance frameworks. It's an iterative approach that delivers real results without breaking the bank.
Avoiding Common Compliance Management Pitfalls
Knowing where the landmines are is the first step to not stepping on one. When it comes to compliance, we see so many small and midsize businesses stumble over the same hurdles again and again. But the good news is that these mistakes are entirely avoidable if you know what to look for.
Let's walk through some of the most common traps—from treating compliance like a one-off task to failing to get leadership on board. By understanding these pitfalls, you can build a program that actually works and stands the test of time.
The “One-And-Done” Project Trap
This is probably the single most dangerous misconception out there. A company will hustle to pass an audit, get a certification, and then… breathe a sigh of relief and stick the binder on a shelf. Job done, right?
Wrong. Compliance isn't a destination; it's an ongoing process. Regulations evolve, new cyber threats pop up constantly, and your own business changes over time. A compliance program that isn't actively managed becomes irrelevant almost immediately, leaving you just as exposed as you were before you started.
Proactive Strategy: Think of compliance like tending a garden, not building a house. It needs constant attention. Schedule simple, recurring compliance check-ins—quarterly is a great rhythm to get into. These meetings don't need to be marathons; just a focused check to see what's changed and if your controls need a tune-up.
The Check-The-Box Mentality
We've all seen this one. It’s the mindset of doing the bare minimum to pass the test without actually learning the material. It's the difference between installing a firewall because a rulebook says so, and actually configuring that firewall to block the real-world threats targeting your business.
A check-the-box approach gives you a false sense of security. You might be "compliant" on paper, but you're not secure. The controls are just for show, and they don't truly address your company's unique risks. This completely misses the point of what is compliance management in the first place: genuinely protecting your data, your customers, and your reputation.
Lack of Leadership Buy-In
If the people at the top aren't truly on board, any compliance initiative is doomed to be a slow, painful grind. When leadership views compliance as just another expense or a bureaucratic headache, the program will never get the resources, budget, or authority it needs to be effective.
Your team can spot this a mile away. If the bosses don't take it seriously, why should they? Compliance quickly becomes seen as an obstacle to getting "real work" done instead of what it is: an essential part of doing business responsibly.
To get ahead of this, leaders have to be the program's biggest champions. Here's what that looks like:
- Communicate the "Why": Leaders need to connect the dots for everyone, explaining how compliance protects jobs, builds customer trust, and ultimately helps the company grow.
- Allocate Real Resources: This means dedicating people's time—not just their leftover time—and setting aside a realistic budget for the right tools and training.
- Lead from the Front: When executives follow the security policies themselves, it sends a crystal-clear message that this stuff matters and everyone is accountable.
By steering clear of these common pitfalls, you can transform your compliance program from a reactive, stressful burden into a proactive, strategic advantage that makes your entire organization stronger.
When to Partner with a Managed Provider
For most small and midsize businesses, trying to manage compliance and cybersecurity internally is like deciding to represent yourself in court. You could do it, but it's wildly inefficient and the risks are enormous.
The simple truth is that mastering frameworks like HIPAA or PCI DSS requires a very specific, deep expertise that most SMBs just don't have on the payroll. This is the exact moment where bringing in a managed services provider (MSP) can completely change the game.

Think of an MSP as the specialized architect for your digital infrastructure. An architect’s job is to make sure a new building meets every single complex code and structural standard; an MSP does the same for your IT environment, ensuring it stands up to all relevant regulatory demands. They don't just hand you a box of software—they build and run your entire compliance program.
Turning Strategy into Action
A great provider takes compliance off the whiteboard and makes it a living, breathing part of your daily operations. They bring the experience, the team, and the toolset to do the heavy lifting for you. This almost always includes:
- Expert Risk Assessments: Pinpointing your unique vulnerabilities and figuring out exactly what regulations apply to you.
- Implementing Technical Controls: Setting up and managing the firewalls, encryption, and access controls your specific framework demands.
- Continuous Monitoring: Using sophisticated tools to keep a 24/7 watch on your systems for any threats or compliance slip-ups.
- Audit Preparedness: Gathering and organizing all the necessary documentation and proof to make audit day a smooth, predictable process.
Partnering with an MSP isn't just another business expense. It's a strategic investment in your security, your peace of mind, and your freedom to actually focus on growing your company. You get enterprise-level expertise without the shocking enterprise-level price tag.
Navigating an Increasingly Demanding Landscape
The pressure to stay compliant isn't going away—it’s getting more intense. Audits are becoming more frequent and thorough, with recent data showing that 58% of organizations now face four or more audits every single year.
Many of the most common compliance failures are tied directly to cybersecurity breaches (28%) and issues with third-party vendors, which just underscores how critical expert oversight has become.
For any business serious about protecting its data and reputation, having an experienced partner is no longer a luxury. A provider that specializes in managed IT and cybersecurity services can design a roadmap that perfectly aligns your technology with your compliance goals.
Ultimately, this kind of partnership lets you hand off the immense burden of compliance management so you can get back to what you do best: running your business.
Frequently Asked Questions About Compliance
Even with a solid grasp of the basics, real-world questions always pop up when it's time to put theory into practice. Let's tackle some of the most common concerns business owners have when they start building their compliance program.
What Is the Real Cost of Compliance for a Small Business?
There’s no single price tag for compliance. The cost is more of a spectrum, and where you fall on it depends entirely on your industry and the kind of data you handle. For most small businesses, the initial investment covers things like a professional risk assessment, putting necessary security tools in place (like firewalls or data encryption), and training your team.
It’s easy to focus on that upfront number, but the real math involves comparing it to the astronomical cost of getting it wrong.
A single data breach can trigger devastating fines, legal battles, and a loss of customer trust that can permanently shutter a small company. In that light, proactive compliance isn't an expense—it's an investment in staying in business.
The true cost isn't what you spend on compliance; it's what you stand to lose without it. Viewing it as a business-critical function rather than an expense is the key to a healthy long-term strategy.
How Is Compliance Different from Cybersecurity?
This is a great question because the two are deeply intertwined, but they aren't the same thing. It helps to think of it like this:
- Cybersecurity is the hands-on practice of protecting your technology. It's the "how"—the firewalls, the multi-factor authentication, the endpoint protection, and all the technical defenses you deploy against threats.
- Compliance is about adhering to a specific set of rules laid out by a third party, like the government (HIPAA) or the payment card industry (PCI DSS). It's the "what" and the "why" that directs which cybersecurity measures you must have in place.
You can technically be compliant without being truly secure, especially if you’re just going through a checklist. But you can't be truly secure in today's world without implementing the robust cybersecurity controls that nearly every compliance framework demands.
Can Software Automate Our Compliance Program?
Yes and no. Software is a fantastic tool for streamlining a compliance program, but it can’t run the whole show on its own. Compliance management platforms are brilliant for automating tedious tasks like continuous monitoring, organizing policy documents, and generating evidence for an audit. They can save you a huge amount of time and cut down on human error.
But at its core, compliance requires human judgment. You can't automate strategic decisions, nuanced risk assessments, or the critical work of building a security-conscious culture. Technology is a powerful ally, not a replacement for a well-managed program with people at the helm.
How Often Should We Review Our Compliance Strategy?
Think of your compliance strategy as a living part of your business, not a "set it and forget it" document. A full review should happen at least once a year. But the best practice is to have more frequent check-ins, maybe quarterly, to stay on top of things.
Beyond the regular schedule, certain events should trigger an immediate review:
- A major change in regulations that affects your business.
- You bring a new major technology system online.
- You experience a security incident (or even a close call).
- Your business model changes significantly (e.g., expanding into a new market).
Keeping your strategy current ensures it actually protects you, rather than just gathering dust on a shelf.
Navigating the world of compliance is a major undertaking, but you don't have to figure it all out alone. Defend IT Services offers the expert guidance and managed solutions you need to build a compliance program that not only protects your business but also helps it grow. Contact us today to build your compliance roadmap.

