A Security Operations Center (SOC) is the command center for a company's cybersecurity. It's a dedicated unit where a team of experts uses a suite of technologies and well-defined processes to constantly watch over, detect, and respond to cyber threats, 24/7.
Think of it as the digital equivalent of an air traffic control tower for your entire IT environment.
The Central Nervous System of Your Cybersecurity

Imagine your business is a fortress. A SOC isn't just a set of walls; it's the elite team of guards inside, actively monitoring every gate, patrolling the perimeter, and analyzing surveillance feeds around the clock. Their single-minded mission is to spot and neutralize any threat before it can breach the defenses.
Without a centralized hub like a SOC, security becomes a patchwork quilt of different tools and teams. One group handles the firewall, another manages antivirus on laptops, and someone else looks after cloud security. This siloed approach creates dangerous blind spots that attackers are quick to exploit.
A SOC pulls all those disparate data streams into one unified command center. This gives the security team a complete picture, allowing them to connect the dots and build a coordinated, proactive defense.
The Three Pillars of an Effective SOC
At its heart, any successful SOC—whether it's in-house or outsourced—is built on three essential pillars working together. If one is weak, the entire structure is at risk.
A quick look at the essential components that form the foundation of any security operations center.
| Pillar | Role in Cybersecurity Defense |
|---|---|
| People | The skilled security analysts, engineers, and managers with the expertise to investigate alerts, hunt for hidden threats, and manage incidents. |
| Processes | The clearly defined playbooks and workflows that guide the team’s actions, ensuring a consistent and efficient response to any security event. |
| Technology | The advanced toolset that gives the team its power, including systems that collect log data, identify anomalies, and automate responses. |
These three elements must be in constant sync to handle the sheer volume of modern cyber threats effectively.
The scale of data a modern SOC deals with is almost unbelievable. The average customer generates around 33 billion security-relevant events every single year. That’s a flood of information far too vast for any human to sift through without the right technology and processes guiding them.
Why a SOC is a Business Imperative
A SOC isn't just another line item in the IT budget; it’s a core business function that directly protects your revenue, reputation, and the trust you've built with your customers. The importance of cybersecurity for growing businesses is huge, as a single successful attack can lead to crippling financial losses and operational chaos.
By centralizing threat management, a SOC shifts your organization from a reactive, "break-fix" mentality to a proactive state of constant vigilance. This approach dramatically reduces the odds of a successful attack and shrinks the potential damage if one does get through. For a deeper look into the core concepts, you can explore this excellent guide on What Is a Security Operations Center?.
Meet the Team Inside a Modern SOC
While technology is the engine of a modern SOC, it's the people who are firmly in the driver's seat. A SOC isn't just a room full of glowing monitors; it's a hub of skilled professionals working together to defend the organization's most critical assets. Think of it as a cybersecurity special forces unit, where every member has a distinct and vital role.
These roles are typically organized into tiers, which creates a smart, structured workflow for handling security events. This system ensures alerts are triaged efficiently, with each level of analyst bringing more advanced expertise to the table. It keeps your senior experts from getting bogged down in low-level noise and makes sure the most complex threats get the focus they deserve.
Tier 1 Analyst: The Frontline Defenders
Tier 1 analysts are the sentinels of the SOC. They are the first line of defense, constantly monitoring the stream of alerts coming from security tools like the SIEM. Their job is to perform the initial triage, kind of like an emergency room nurse sorting out who needs immediate attention.
They spend their day sifting through alerts, quickly separating the false alarms from genuine, credible threats. A Tier 1 analyst might investigate a spike in failed login attempts from a weird location or an unusual file download on a critical server. If an alert looks like a real problem, they gather the initial data and pass it up the chain for a deeper look.
Tier 2 Analyst: The Incident Responders
When an alert gets escalated, it lands with a Tier 2 analyst. These folks are the investigators. They have a much deeper understanding of threats and forensic techniques, allowing them to really dig into the "who, what, when, and how" of a security incident.
A Tier 2 analyst will take the initial report from Tier 1 and start connecting the dots. They'll analyze network traffic, comb through endpoint logs, and pull data from multiple sources to understand the full scope of the attack. Their goal is to contain the threat and lay out a clear plan for fixing the problem. This team often includes specialists like an Incident Response Engineer, who is an expert at managing the fallout from a breach.
A SOC is a perfect example of the human-machine partnership. Technology provides the data and scale, but it takes human intuition, curiosity, and experience to connect disparate clues and uncover the story behind an attack.
Tier 3 Analyst: The Proactive Threat Hunters
Tier 3 analysts are the most senior technical minds in the SOC. While Tiers 1 and 2 are mostly reactive—responding to alerts as they happen—Tier 3 is all about being proactive. They are the elite threat hunters, actively searching for sophisticated attackers who might have slipped past the automated defenses.
These experts use their deep knowledge of attacker tactics to hunt for subtle signs of compromise that machines might miss. They might search for unusual patterns in system behavior, create new detection rules based on the latest threat research, and take the lead on major, complex incidents. Their work is essential for finding and stopping advanced persistent threats (APTs) before they cause serious damage.
The Strategic Leadership Roles
Keeping all these technical tiers working in harmony requires a couple of key leadership and support roles to provide direction and big-picture context.
- SOC Manager: This person runs the whole show. They manage the team, fine-tune the processes, report on performance to company leadership, and make sure the SOC has the budget and tools it needs to win.
- Threat Intelligence Analyst: Think of this specialist as the SOC's reconnaissance expert. They study the global threat landscape, analyzing attacker groups, their motives, and their methods. They then feed this crucial intelligence back to the team, giving them the context to know what to look for and how to fight back effectively.
How a SOC Actively Protects Your Business
A Security Operations Center isn't just a defensive wall waiting to be hit. Think of it more like an immune system for your business—a dynamic, living defense that’s constantly working through a cycle of monitoring, detection, and response. To really get what a SOC is, you have to see how it takes a faint, suspicious signal and follows it all the way through to a fully resolved security incident.
It all starts with constant vigilance. A SOC pulls in a massive stream of data every second from every corner of your organization. We’re talking network traffic, server logs, cloud activity, and data from every single endpoint. Specialized tools then dig through this ocean of information, hunting for anything that looks out of place or deviates from normal, safe behavior.
This proactive monitoring is the bedrock of everything a SOC does. It’s what lets the team spot the earliest whispers of trouble, often long before an automated alarm even thinks about going off.
From Alert Overload to Actionable Intelligence
When a potential threat pops up, the next critical job is triage. An average business network can spit out thousands of security alerts every day, and the truth is, most of them are false alarms. Without a skilled team, this "alert fatigue" is a real problem, making it easy to miss the one alert that actually matters. The SOC team acts as that expert filter.
This is where having a tiered analyst structure really shines. A Tier 1 analyst is the first line of defense. They'll investigate an alert, quickly figure out if it’s a genuine threat or just noise, and if it looks real, they gather the essential data and pass it up the chain.
The process below shows how this works, moving an alert through different levels of expertise to get it resolved efficiently.
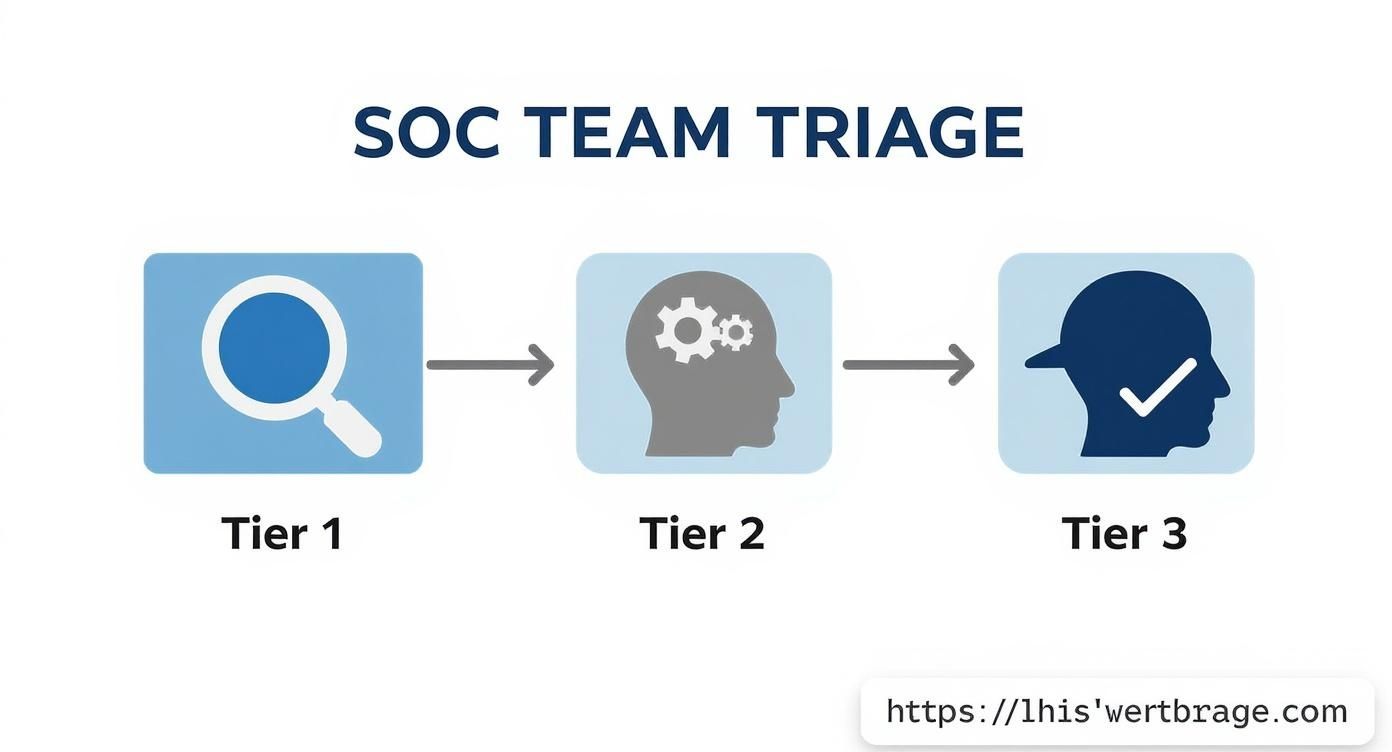
This methodical flow makes sure that your most experienced analysts are spending their time on the most complex and dangerous threats, not getting bogged down by minor issues.
Launching a Coordinated Incident Response
Once a threat is confirmed and sized up, the SOC flips into incident response mode. This isn’t a chaotic scramble; it’s a well-rehearsed plan, guided by playbooks designed for specific types of attacks. The main goal here is simple: contain the threat and minimize the damage as fast as humanly possible.
A typical incident response follows a few key stages:
- Containment: The absolute first priority is to stop the bleed. This could mean yanking a compromised laptop off the network, blocking a malicious IP address at the firewall, or shutting down a user account that’s been hijacked.
- Eradication: Once the threat is boxed in, the team works to surgically remove it from the environment. This means killing off malware, patching the vulnerability the attacker used to get in, and making sure no backdoors were left behind.
- Recovery: With the threat gone, the focus shifts to getting everything back to normal. This might involve restoring data from clean backups or even rebuilding entire systems, all while making double-sure they are secure before going back online.
This structured response is what separates a minor hiccup from a major disaster. It ensures that every step is taken not just to fix the immediate problem, but to slam the door shut so the same attacker can't just walk back in. For companies in our area, a solid response capability is a primary reason why every San Antonio business needs managed IT and cybersecurity services to keep their operations safe.
Learning and Improving from Every Attack
The SOC’s job isn’t over once the incident is closed. The final, and arguably most important, phase is the post-incident analysis. This is where the team performs a full post-mortem, dissecting the attack to figure out exactly what happened, how it happened, and why.
A core principle of a mature security operations center is that every incident, big or small, is an opportunity to get stronger. The goal isn't just to respond—it's to adapt.
During this review, analysts dig deep. How did the attacker get in? What could we have done to catch it sooner? Are there new security rules or policies we can implement to stop this from happening again?
The answers to these questions are pure gold. They feed directly back into the SOC's defenses, leading to updated firewall rules, new detection logic in their monitoring tools, or even fresh security awareness training for staff. It’s this constant feedback loop that ensures an organization's defenses are always evolving, getting smarter and stronger with every attempted attack.
The Technology Stack That Powers a SOC

Behind every effective SOC is a powerful arsenal of technology. These aren’t just tools; they're the eyes, ears, and hands of the security team, letting them cut through the noise and respond to threats at machine speed. Without the right tech, a SOC team would be flying blind, completely overwhelmed by the sheer volume of modern cyberattacks.
Think of these technologies as layers of a sophisticated defense system. Each has a specific job, but they all have to work together seamlessly. Understanding these core components is the key to seeing how a security operations center really functions.
The demand for these advanced tools is skyrocketing for a reason. The global Security Operations Center market, currently valued at about USD 44.2 billion, is expected to hit USD 152.59 billion by 2037. This incredible growth is all about the need for smarter, faster security powered by AI and machine learning. You can discover more insights about the SOC market growth on researchnester.com.
SIEM: The Central Brain of the SOC
The Security Information and Event Management (SIEM) system is the foundation of any modern SOC. It’s the central nervous system, pulling in log data from everything—firewalls, servers, workstations, cloud apps, you name it.
A SIEM’s main purpose is to bring all that disconnected data into one place. By crunching this data in real time, it spots anomalies and potential threats, then flags them for the team to investigate. It’s what turns a chaotic flood of raw information into a manageable stream of prioritized alerts.
SOAR: The Muscle for Automated Response
If the SIEM is the brain, then Security Orchestration, Automation, and Response (SOAR) is the muscle. SOAR platforms take the alerts from the SIEM and other tools and kick off the initial response automatically. This is absolutely essential for dealing with the constant barrage of routine alerts that would otherwise bury a security team.
SOAR platforms follow pre-built "playbooks" to execute a chain of actions without a human lifting a finger. For instance, an alert for a malicious file could trigger a SOAR playbook to:
- Instantly quarantine the affected machine to stop the spread.
- Block the malicious file’s signature on all other devices.
- Log a ticket in the system for an analyst to review the aftermath.
This automation frees up analysts to use their skills on the complex, high-stakes incidents that truly need their attention.
"A SIEM tells you something is wrong. A SOAR platform starts doing something about it. Together, they form a powerful combination of detection and response that is essential for modern security operations."
EDR: Eyes on the Endpoint
Endpoint Detection and Response (EDR) tools give the SOC deep visibility into what’s happening on individual devices like laptops, servers, and phones. Your classic antivirus just isn't enough to stop the kinds of advanced attacks that can hide out on these endpoints.
EDR solutions act like a security camera on every device, constantly monitoring for suspicious behavior like unusual commands being run or weird changes to system files. If it spots a threat, an EDR solution can immediately isolate that compromised device from the network to contain the damage. It provides the crucial forensic data analysts need to figure out exactly what happened.
Threat Intelligence Platforms: Providing Crucial Context
Finally, Threat Intelligence Platforms (TIPs) add critical outside context, helping the SOC understand the who and why behind an attack. A TIP gathers data from global sources on the latest malware, attacker tactics, and vulnerabilities being exploited right now.
This intelligence feeds directly into the SIEM and SOAR, making their detection rules and automated responses much smarter. It helps analysts answer questions like, "Is this IP address tied to a known ransomware group?" or "Does this activity match a new phishing campaign everyone is talking about?" By understanding the enemy, the SOC can build a much more proactive defense.
Choosing the Right SOC Model for Your Needs
https://www.youtube.com/embed/OHkWXFheSKM
Deciding you need a Security Operations Center is the easy part. The real question is: how do you get one? Not every business has the budget or the desire to build a cybersecurity command center from scratch. Thankfully, you don't have to.
There are a few different ways to approach this, each striking a different balance between cost, control, and access to expertise. Figuring out which path is right for you is crucial, as it will define your defensive strategy for years to come. It’s all about finding the perfect fit for your company’s unique situation.
The In-House SOC Model
The traditional route is the in-house SOC. This means you build it, staff it, and run it all yourself, on-site. The biggest advantage here is total control. Your team lives and breathes your company culture and knows your IT environment inside and out.
But that control comes with a hefty price tag. You’re looking at a massive upfront investment in technology, like a SIEM and a SOAR platform. Even tougher is the human element: you have to find, train, and pay a team of top-tier cybersecurity experts to provide 24/7 coverage. For most small and midsize businesses, the cost and staffing headaches make this a non-starter.
The Outsourced SOC Model: SOC-as-a-Service
On the complete opposite end is the fully outsourced model, what we call SOC-as-a-Service (SOCaaS) or a Managed Security Service Provider (MSSP). Here, you hire a dedicated firm to be your SOC. They bring the people, the tech, and the processes.
This approach has some serious perks:
- Instant Expertise: You immediately get access to a team of battle-hardened security pros.
- Predictable Costs: Forget massive capital expenditures. You pay a simple, predictable subscription fee.
- Enterprise-Grade Tools: MSSPs use the kind of powerful, expensive technology that’s often out of reach for a single organization.
The trade-off? You hand over some of the day-to-day operational control. You still set the strategy, but they handle the tactical execution. This is a fantastic option for businesses that want world-class security without the management overhead. The market agrees; SOC-as-a-Service is projected to grow at a CAGR of over 14% between 2025 and 2030 as more companies look for expert-led security. You can dig into the full research about security market projections to see these trends for yourself.
The Co-Managed or Hybrid SOC Model
What if you want something in the middle? That’s where a co-managed SOC comes in. This hybrid model pairs your internal IT team with the specialized skills of an external provider. It’s a true partnership.
For instance, your team might handle the initial review of an alert, using their knowledge of your business to add context. Then, they can escalate the tough stuff to the MSSP's experts for deep-dive threat hunting and incident response, especially after hours.
This model is perfect for organizations that have a good IT team but lack the specialized cybersecurity talent or the ability to stay awake all night watching for threats. It truly leverages the best of both worlds.
This collaborative approach lets your team stay in the driver's seat while offloading the most draining and complex tasks. It empowers your people by giving them an expert team to back them up when things get serious. By exploring different cybersecurity services, you can find the right partner to build a co-managed model that works for you.
Comparison of SOC Deployment Models
To make the choice clearer, let’s break down how these three models stack up against each other.
| Aspect | In-House SOC | Co-Managed SOC | Outsourced SOC (SOCaaS) |
|---|---|---|---|
| Initial Cost | Very High (Tech + Hiring) | Moderate (Subscription + Staff) | Low (Subscription-based) |
| Ongoing Cost | High (Salaries, Training, Licenses) | Predictable (Subscription Fee) | Predictable (Subscription Fee) |
| Control Level | Full Control | Shared Control | Limited Direct Control |
| Expertise | Dependent on internal hiring | Blended (Internal + External) | Access to broad expert pool |
| Coverage | 24/7 coverage is very expensive | 24/7 coverage is standard | 24/7 coverage is standard |
| Implementation | Long & Complex | Moderate | Fast |
| Best For | Large enterprises with mature security programs and significant budgets. | SMBs with existing IT staff who need to augment their capabilities. | SMBs with limited IT/security staff who need a comprehensive solution. |
Ultimately, there's no single "best" model—only the best model for your business. Whether you need a full-service partner or just a helping hand, the right SOC model can transform your security posture from a source of stress into a position of strength.
Measuring SOC Performance and Ensuring Compliance
A good Security Operations Center doesn't just give you a warm, fuzzy feeling of security; it delivers hard numbers that prove your investment is paying off. To really know if a SOC is pulling its weight, you can't just count the number of attacks it blocks. You need to dig deeper into metrics that show how fast and how sharp your defenses really are.
These metrics, or Key Performance Indicators (KPIs), cut through the technical noise and tell a clear story. They answer the questions that keep leaders up at night: How long can an attacker hide in our network before we spot them? And once we do, how fast can we get them out?
Without these measurements, you're essentially flying blind. You have no real way to justify your security budget or prove that your defenses are actually getting better.
Key Metrics That Define SOC Success
Two of the most critical numbers for any SOC are Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). They aren't just buzzwords; they're direct reflections of how your team performs under pressure.
Mean Time to Detect (MTTD): This is the average time it takes for your team to discover a security threat from the moment it first appears. The lower, the better. A short MTTD means intruders have less time to wander around your network, steal data, or do real damage.
Mean Time to Respond (MTTR): This measures how long it takes to shut down a threat after it's been detected. A low MTTR means your team can act decisively, stopping an attack cold and limiting the fallout.
Think of it like a house fire. MTTD is how quickly the smoke alarm goes off. MTTR is how fast the firefighters show up and put the blaze out. You need both to work quickly, or a small spark can turn into a total disaster.
Turning Security into a Compliance Enabler
A SOC does more than just fight off attackers; it's also a powerful ally for navigating the maze of regulatory compliance. Many industries have strict, non-negotiable rules about protecting sensitive data. Getting it wrong can lead to eye-watering fines and a tarnished reputation.
A well-oiled SOC provides the operational proof and detailed evidence that auditors and regulators need to see for standards like:
- HIPAA: For healthcare organizations managing protected health information (PHI).
- PCI DSS: For any company processing credit card payments.
- GDPR: For businesses handling the personal data of European Union citizens.
The constant monitoring, meticulous logging, and formal incident response plans that are baked into a SOC's DNA are precisely what these regulations require. The SOC produces the reports and audit trails that demonstrate you have strong controls in place, transforming your security function from a simple cost center into a business enabler that builds and maintains customer trust.
Got Questions About SOCs? We've Got Answers.
When you start digging into cybersecurity, a few common questions always pop up. Let's clear the air and tackle some of the most frequent ones we hear about security operations centers.
What’s the Difference Between a SOC and a NOC?
It's a common point of confusion, but the distinction is pretty simple. A Security Operations Center (SOC) is all about security. A Network Operations Center (NOC), on the other hand, is all about performance and availability.
Think of it like this: the NOC ensures the digital highways are paved, open, and free of traffic jams. Their job is to keep things running smoothly. The SOC is the highway patrol, actively looking for drunk drivers, carjackers, and anything else that could cause harm on those roads. One keeps the lights on; the other keeps the bad guys out.
Does a Small Business Really Need a SOC?
In a word: yes. Hackers love targeting small and midsize businesses for the simple reason that they often assume their defenses are weaker. It's a numbers game for them.
While building your own in-house SOC is usually out of reach for smaller companies, that's where modern solutions like SOC-as-a-Service come in. These services give you access to enterprise-grade, 24/7 monitoring and a team of experts for a fraction of the cost. If you handle any sensitive data—customer info, payment details, patient records—a SOC isn't a luxury; it's a fundamental part of modern business defense.
It's a dangerous myth that only huge corporations are targets. Any business that relies on technology is on the radar for cybercriminals, which makes professional security monitoring a necessity.
How Do AI and Machine Learning Fit Into a SOC?
Artificial intelligence and machine learning are game-changers for a human SOC team. They act as incredible force multipliers. Think of them as tireless assistants who can sift through billions of digital clues in seconds, spotting subtle patterns of an attack that a human analyst might overlook.
This automation is fantastic for handling the initial grunt work—flagging suspicious activity and weeding out the endless stream of false alarms. It frees up the human experts to do what they do best: deep-dive investigations, creative problem-solving, and stopping real threats in their tracks. It makes the whole operation smarter, faster, and far more effective.
At Defend IT Services, we believe every business deserves top-tier security without the enterprise price tag. Our SOC-as-a-Service delivers the round-the-clock protection you need, so you can focus on running your business. Learn more about our managed cybersecurity solutions.

