It’s a common, and frankly dangerous, myth that small businesses fly under the radar of cybercriminals. Many owners think, "Why would they target me? I'm just a small fish." But that's precisely why they're so appealing.
Attackers see small businesses as the perfect target: you hold valuable data but likely lack the fortress-like security of a massive corporation. Getting a handle on this reality is the first crucial step to protecting your business.
Why Small Businesses Are a Goldmine for Hackers

Let's debunk the idea that hackers only go after giant corporations. The truth is, they love the path of least resistance. Think of your business like a house on a street full of high-security mansions. If your front door is unlocked, that's where a burglar is going to go first. It's just easier.
Small businesses are often seen as soft targets for a few key reasons. You might be a gateway to a larger company's supply chain, you definitely have customer data worth stealing, and your IT security budget probably isn't massive. This combination makes you an incredibly attractive target for criminals looking for a quick and easy payday.
The Aftermath of an Attack is More Than Just Financial
When a breach happens, the damage goes far beyond the initial hit to your bank account. The fallout can create a domino effect that puts the entire future of your business on the line.
Here’s what you’re really up against:
- Crippling Financial Costs: The expenses pile up fast. You're not just dealing with the theft itself, but also forensic investigations, regulatory fines, and potentially even ransomware payments.
- Reputation Damage: Trust is everything. Once you lose it, it's incredibly hard to win back. Customers will rightfully worry about their data and may simply go to a competitor they feel is safer.
- Operational Downtime: Imagine your entire operation grinding to a halt. A successful attack can shut you down for days or even weeks, leading to a complete standstill in revenue and productivity.
In 2025, a staggering 43% of all cyberattacks are expected to hit small businesses. The average cost of a single breach is pegged at $120,000—a figure that would be a knockout blow for most small companies. Worse yet, the rise of "Ransomware-as-a-Service" has made it simple for even amateur hackers to launch sophisticated attacks.
Believing you're "too small to be a target" is an outdated and dangerous mindset. Modern cybercriminals use automated tools to constantly scan the internet for any weakness, making any business with an online presence a potential victim.
To really grasp the modern threat, including things like the reality of ransomware outbreaks, it becomes crystal clear that having a strong defense isn't a luxury—it's a fundamental requirement for staying in business.
Understanding Your Core Cybersecurity Defenses
Building a solid digital defense isn't about finding one magical solution. It’s about creating layers of protection, a lot like building a medieval fortress designed to withstand a siege. Each layer has a specific job, and they only create a truly secure environment when they work together.
This infographic shows how that fortress approach works, with different layers of cybersecurity services protecting your most valuable assets.
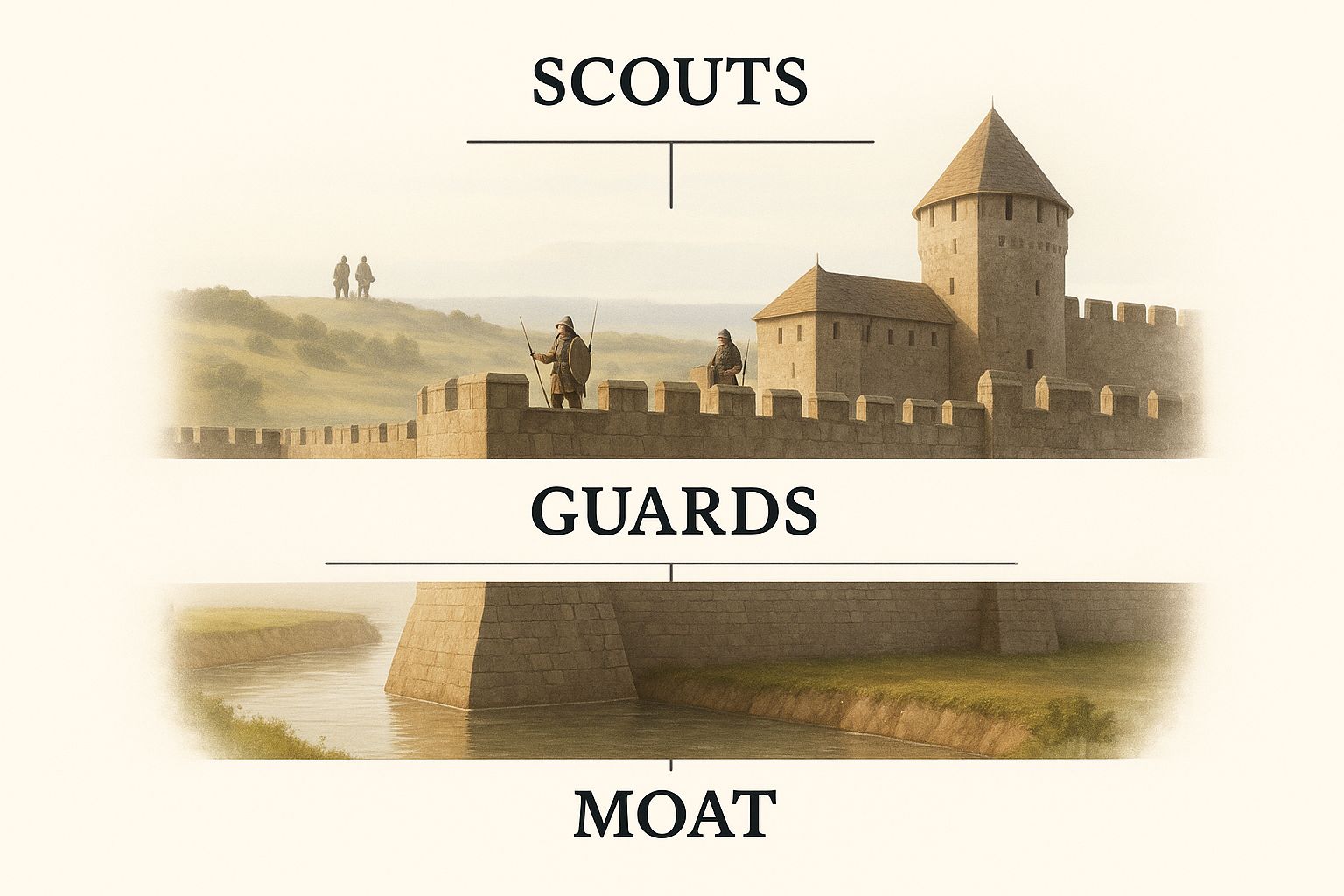
As you can see, a complete defense starts from the outside and works its way in. Every single component plays a vital role in the overall strategy.
The Moat: Your Network Security
Your first line of defense is the network perimeter—think of it as the digital "moat" around your castle. Its entire purpose is to control what comes in and what goes out, stopping obvious threats before they can even get close to your walls.
Key services here include:
- Managed Firewalls: These are your primary gatekeepers. They inspect all the data trying to get in and out, blocking anything malicious based on a pre-set list of security rules.
- Virtual Private Networks (VPNs): A VPN creates a secure, encrypted tunnel for remote employees to access company files and systems. This is crucial for preventing hackers from spying on them when they use public Wi-Fi.
Without a strong moat, your business is wide open to the internet, making it incredibly easy for attackers to start looking for a way in.
The Walls: Your Endpoint Protection
If a bad actor somehow gets across the moat, their next challenge is the fortress walls. In cybersecurity, these "walls" are your endpoint devices—all the laptops, desktops, servers, and smartphones your team uses every day.
This is where Endpoint Detection and Response (EDR) becomes essential. It’s like having guards on the walls who aren’t just looking for known enemies (like old-school antivirus). Instead, they are actively hunting for any suspicious behavior. If a threat is spotted on one device, it can be instantly quarantined from the rest of the network to stop an attack from spreading.
The Guards: Your Threat Monitoring Team
Even the strongest walls can be breached. That's why you need vigilant guards constantly patrolling for trouble. This is the job of 24/7 Threat Monitoring and Response, often handled by a dedicated Security Operations Center (SOC).
These experts are your human sentinels, using sophisticated tools to watch for any sign of an intrusion, day or night. When an alarm goes off, they don't just send you an email alert. They immediately jump in to investigate, contain the threat, and start fixing the problem. This proactive monitoring is the key to stopping attacks before real damage is done.
A recent Mastercard survey revealed that 46% of small businesses have been hit by a cyberattack. Of those, nearly 20% ended up filing for bankruptcy or closing their doors permanently, showing just how devastating a breach can be. You can read the full cybersecurity study from Mastercard for more insights.
The Scouts: Your Vulnerability Management
Finally, a smart defender doesn’t just sit around waiting to be attacked. They send scouts out beyond the walls to find potential weaknesses before the enemy can use them. This is what Vulnerability Management is all about.
This service involves regularly scanning your entire system—your software, network, and devices—for known security holes or configuration errors. By finding and patching these vulnerabilities ahead of time, you're basically sealing up the cracks in your fortress walls before an attacker even knows they're there. Exploring a full range of cybersecurity services is the best way to build this kind of layered defense.
To help you visualize how these pieces fit together, here's a quick summary of the essential services and what they protect you from.
Essential Cybersecurity Services for Small Businesses
| Service Category (Fortress Analogy) | Key Services Included | Primary Threats Addressed |
|---|---|---|
| Network Security (The Moat) | Managed Firewalls, VPNs, Intrusion Detection Systems | Unauthorized access, malware, denial-of-service (DoS) attacks, network intrusions |
| Endpoint Protection (The Walls) | Endpoint Detection & Response (EDR), Next-Gen Antivirus | Ransomware, spyware, viruses on devices, fileless malware |
| Threat Monitoring (The Guards) | 24/7 Security Operations Center (SOC), Log Monitoring | Active breaches, insider threats, advanced persistent threats (APTs), zero-day attacks |
| Vulnerability Management (The Scouts) | Regular Scanning, Patch Management, Penetration Testing | Unpatched software, system misconfigurations, known exploits |
Each of these layers is crucial. Relying on just one or two leaves dangerous gaps that attackers are experts at finding. A comprehensive, multi-layered approach is the only way to truly secure your business.
Managed Services Versus an In-House Team
As a business owner, you'll eventually hit a fork in the road when it comes to securing your company. Do you build your own in-house cybersecurity team from the ground up, or do you partner with a Managed Security Service Provider (MSSP)? This isn't a small decision—it directly shapes your budget, your capabilities, and how well you can actually defend your business.
Let’s try an analogy. Hiring an in-house team is a lot like hiring a full-time personal chef. You get a dedicated expert who learns your tastes and is always on hand. The catch? You're on the hook for their salary, benefits, all the kitchen equipment, and ongoing culinary classes. It’s a fantastic, white-glove service if you have the resources to back it up.
Partnering with an MSSP, on the other hand, is more like signing up for a high-end gourmet meal delivery service. You instantly get access to a whole team of specialized chefs—experts in different cuisines—all using top-tier equipment. It’s predictable, cost-effective, and you get a level of variety and expertise that would be impossible to get from just one person.
The Cost and Expertise Gap
For most small businesses, the math just doesn't work for an in-house team. Putting together even a small, competent security crew is a serious financial commitment. You're not just hiring one person; you need multiple specialists to cover all your bases, and you have to pay them competitive salaries. Then come the expensive tools and the constant training needed to keep their skills from going stale.
An MSSP flips this model on its head, offering a predictable subscription. For a flat monthly fee, you get an entire team of seasoned security pros and their arsenal of enterprise-grade technology. It turns a massive capital investment into a manageable operational expense.
The real magic of an MSSP is getting access to a deeper, broader pool of expertise than a small business could ever hope to hire on its own. You get specialists in threat hunting, network security, and compliance all working for you.
This collective brainpower is a game-changer in a field where new threats pop up daily. One person, or even a small internal team, simply can't keep up with every new attack vector and vulnerability.
Around-the-Clock Protection and Scalability
Hackers don't work 9-to-5, and your defenses shouldn't either. One of the biggest wins of partnering with an MSSP is getting 24/7/365 monitoring. Their Security Operations Center (SOC) never sleeps. It's constantly watching your network, ready to jump on a threat the second it appears—whether that's 3 AM on a Sunday or in the middle of a holiday.
Trying to achieve that level of constant vigilance with a small in-house team is a recipe for burnout and dangerous coverage gaps.
Plus, an MSSP can grow with you. As your business expands or your needs shift, they can easily scale their services up or down. That’s a kind of flexibility that’s incredibly difficult to match with internal hires. For local businesses, seeing why you need managed IT and cybersecurity services in San Antonio can really drive home the benefits.
While an in-house team gives you dedicated, hands-on control, an MSSP delivers a far more practical and powerful security solution for the vast majority of small businesses, giving them top-tier protection without the crippling price tag.
How to Choose the Right Cybersecurity Partner
Picking a provider for your small business's cybersecurity is a huge decision. You're not just hiring another vendor; you're entrusting a partner with the keys to your kingdom. The best ones operate like an extension of your own team, truly getting to know your business, your challenges, and where you want to go.
A great firm won't just throw a software package at you and call it a day. They'll start by asking questions and listening. This discovery phase is a massive green flag—it shows they’re committed to crafting a security strategy that actually fits your business, not just selling you a pre-packaged deal.
Evaluate Their Industry Expertise
Every industry has its own unique set of threats and compliance headaches. A provider that’s protected a local doctor's office will be fluent in HIPAA, while one that works with manufacturing plants will know the ins and outs of securing factory floor systems. That kind of specialized knowledge is pure gold.
When you're interviewing potential partners, don't be afraid to dig deep. Ask for case studies or references from businesses in your field. Be direct:
- Have you worked with other companies in the [your industry] space?
- What are the biggest threats you see hitting businesses like mine right now?
- How do you help your clients stay compliant with regulations like PCI DSS or CMMC?
An experienced and confident partner will have solid, specific answers ready to go. If they get vague or can't point to relevant experience, that's a major red flag.
Scrutinize Their Incident Response Plan
Let's be real: even with the strongest defenses, a security incident can still happen. The real test of a provider isn't when everything is quiet; it's what they do when the alarm bells start ringing. Their Incident Response (IR) Plan is the playbook that dictates how they'll contain the damage and get you back on your feet.
This plan needs to be crystal clear, detailed, and something they can walk you through without hesitation.
A provider's true value is often revealed not when things are calm, but in the critical moments during an active security breach. A well-defined and practiced incident response plan is non-negotiable.
You should know exactly who you're supposed to call at 2 a.m., what their first moves will be, and what they'll need from your team. If they can’t clearly explain their process for handling a ransomware attack, they aren't prepared to protect you when it counts.
Demand Transparent Pricing and Reporting
Hidden fees and confusing contracts are deal-breakers. A provider you can trust will be upfront with their pricing, explaining exactly what you're paying for. You should get a clear Service Level Agreement (SLA) that spells out their commitments on things like response times and support availability.
On top of that, they should give you regular reports that you can actually understand. These reports are your proof that they're doing the job, and they should show you:
- Threats Blocked: A simple summary of the attacks they've stopped.
- System Health: Updates on patch statuses and recent vulnerability scans.
- User Activity: A look at potential internal risks or policy violations.
- Recommendations: Practical advice on how you can improve your security.
Sometimes, a local partner who is genuinely invested in the community's success can make all the difference. Knowing why San Antonio businesses build trust with local cybersecurity experts shows just how valuable that relationship can be. In the end, this is about finding a firm that isn't just technically skilled, but is also transparent, communicative, and truly wants to see your business thrive.
Building Your Human Firewall with Employee Training

You can have the most advanced security software on the planet, but it can all be undone by a single, accidental click. This is why your employees are your true first line of defense. Think of them as a human firewall—a living barrier that can either spot and stop threats or inadvertently open the door and let them in.
An untrained employee is like an open gate in your company’s fortress. They might not think twice about opening a malicious email, get tricked into using a weak password, or mishandle sensitive customer data. These simple mistakes create a direct path for attackers, and it’s a vulnerability cybercriminals are all too eager to exploit.
The numbers here are staggering. Cybercrime is on track to cost the global economy $10.5 trillion by 2025, and that figure is expected to jump to $15.63 trillion by 2029. Just this year, an incredible 94% of small businesses were hit by a cyberattack, with phishing scams being the culprit in roughly 73% of those breaches. Since human error is the root cause of most incidents, you simply can't afford to overlook training.
What Good Security Training Looks Like
At its core, building your human firewall is about understanding Security Awareness Training and empowering your team with the right knowledge. A solid program isn’t a one-and-done lecture; it’s an ongoing process that makes learning practical and engaging.
Effective training really boils down to three key areas:
Spotting Phishing Scams: Teach your team to recognize the tell-tale signs of a scam email—things like urgent demands, weird sender addresses, or generic greetings. Running regular phishing simulations is a fantastic way to let them practice spotting fakes in a safe, controlled environment.
Practicing Smart Password Habits: Show everyone why creating complex, unique passwords for different systems is so important. Better yet, introduce them to password managers. These tools do the heavy lifting of generating and storing strong credentials, so your team doesn't have to.
Handling Data Safely: Make sure your entire staff knows the rules for managing sensitive information, from customer credit card numbers to internal financial documents. This includes clear guidelines on how to share files securely and who has permission to access specific data.
A strong security culture isn't just an IT policy; it's a shared mindset. It’s when every person, from the newest hire to the CEO, feels a sense of ownership in protecting the business. Security becomes everyone's job.
When training is continuous and interactive, you build a vigilant team that actively strengthens your defenses. This approach flips the script, turning your biggest potential weakness into one of your strongest security assets.
Your Proactive Cybersecurity Action Plan
Alright, you've made it this far. You understand the threats and the services that can protect you. Now it's time to put that knowledge into practice and build a real defense for your business.
Think like a thief for a moment. Where are your crown jewels? A simple risk assessment isn't some complex technical audit; it's just you, sitting down and figuring out what data is most valuable and where your defenses are weakest. This helps you focus your efforts where they matter most.
Next, you have to talk about money. Set a realistic budget for cybersecurity services. I know it can feel like just another cost, but try to see it as an investment in your company's survival. A single breach can be far more expensive than a year's worth of protection.
Too many business owners treat cybersecurity like a smoke detector—they install it and forget it. But it's more like a security guard who needs to constantly patrol, adapt, and stay alert. Real security is an ongoing process, not a one-and-done setup.
With a budget in mind, start looking for partners who get what you do and the specific risks your industry faces. And don't forget your team! Schedule your first employee training session. Even a quick 30-minute chat about spotting phishing emails can make a huge difference.
Taking these first concrete steps is how you build a solid security foundation. Acting today is the best way to make sure your business is still standing tomorrow.
A Few Common Questions About Small Business Cybersecurity
When you start digging into cybersecurity services, a lot of practical questions naturally come up. Getting straight answers is the first step to making a smart decision to protect your business. Let's tackle some of the most common things we hear from business owners.
How Much Should We Really Be Budgeting for This?
There’s no one-size-fits-all answer here. The right number depends on your company's size, your industry, and exactly what services you need. That said, a good rule of thumb is to dedicate between 3% and 6% of your total IT budget to security.
A better way to think about it, though, is to start with a risk assessment. A solid provider will help you identify where you're most exposed. This lets you put your budget where it will do the most good, instead of just buying a bunch of tools you might not even need.
Can We Actually Afford All These Security Measures?
Let's flip that question: can you afford not to? The average cost of a data breach for a small business can soar past $100,000. That number completely dwarfs the annual cost of good, preventative cybersecurity.
It's a lot like your business insurance. You pay a predictable, manageable amount to protect yourself from a potential disaster that could sink the company. Many Managed Security Service Providers (MSSPs) even offer monthly subscription plans built specifically for small business budgets, making top-tier protection surprisingly accessible.
The real cost isn't in proactive protection; it's in the reactive cleanup. Investing in security upfront is a strategic decision to avoid the devastating financial and reputational damage of a breach.
How Long Does It Take to Get Everything Set Up?
The timeline really depends on what your IT environment looks like now and which services you’re putting in place. For most small businesses, however, getting started is faster than you might think.
We usually prioritize the foundational services first. These include things like:
- Endpoint Protection: This is your next-level antivirus and threat detection for every laptop, computer, and server.
- Managed Firewalls: Think of this as the security guard for your entire network, monitoring all the traffic coming in and out.
- Email Filtering: This is a huge one, as it blocks phishing attacks, which are far and away the most common entry point for hackers.
Getting these core protections up and running often takes just a week or two. Any good provider will create a phased rollout plan with you, focusing on your most critical assets first so you get meaningful protection right away.
Ready to stop guessing and start securing? The team at Defend IT Services provides expert guidance and powerful cybersecurity services designed for businesses just like yours. Protect your business today by visiting our website.

