In today's interconnected business environment, every device from a laptop to a server represents a potential entry point for sophisticated cyber threats. As organizations in San Antonio and beyond adopt remote work and expand their cloud infrastructure, the traditional network perimeter has dissolved, making robust endpoint protection more critical than ever. For regulated industries like healthcare and finance, securing these endpoints is not just a matter of security, but of compliance.
Choosing the right solution can be a significant challenge, with a crowded market of vendors all promising comprehensive defense. This guide is designed to cut through the noise. We will analyze the 12 best endpoint security software platforms, breaking down their core features, ideal use cases, and practical limitations. This resource is built for small and midsize businesses, growing teams, and multi-location companies that need clear, actionable insights to make an informed decision.
This article provides a detailed comparison of each platform, complete with screenshots and direct links, to help you find the perfect fit. We will explore everything from next-generation antivirus (NGAV) and Endpoint Detection and Response (EDR) to fully managed services. For businesses managing a significant number of mobile devices, understanding the full scope of endpoint protection is key. Exploring what Enterprise Mobility Management (EMM) entails is essential for securing and optimizing your mobile workforce. Our goal is to equip you with the knowledge to safeguard your organization’s most valuable assets against modern threats.
1. Cybersecurity Services
Defend IT Services presents a compelling offering that goes beyond traditional standalone software. Instead of providing just one tool, it delivers a comprehensive, managed cybersecurity service bundle that integrates endpoint security as a core component of a holistic defense strategy. This approach makes it a standout choice for businesses seeking an all-in-one, expertly managed solution rather than a self-managed product.
This bundled service is a strong contender for the best endpoint security software because it addresses the entire threat lifecycle. The service combines endpoint protection with a 24/7 Managed Security Operations Center (SOC), proactive patch management, and Mobile Device Management (MDM). This integrated structure ensures that threats are not only blocked at the endpoint but are also correlated with network and cloud activity for faster, more accurate incident response.
Key Features and Use Cases
The strength of Defend IT Services lies in its multi-layered, managed approach. Rather than simply selling software, they provide a full security partnership.
- Managed SOC Operations: The service includes continuous 24/7 monitoring of endpoints, cloud infrastructure, and networks. This is ideal for organizations without a dedicated internal security team, as it provides enterprise-grade threat hunting and response capabilities.
- Proactive Vulnerability Management: A dedicated team actively manages patches and addresses vulnerabilities before they can be exploited. This is particularly valuable for businesses in regulated industries like healthcare or finance that must maintain strict compliance.
- Integrated Mobile Device Management (MDM): With remote and hybrid work models becoming standard, securing employee-owned and corporate mobile devices is critical. The integrated MDM ensures consistent security policies are enforced across all access points, protecting sensitive data wherever it goes.
- Veteran-Owned Expertise: As a veteran-owned business, Defend IT Services emphasizes a disciplined, strategic approach to cybersecurity, building long-term partnerships focused on personalized support.
Analysis
| Feature | Strengths | Ideal Use Case |
|---|---|---|
| Holistic Protection | Combines endpoint, network, and cloud security under one managed service for unified visibility. | SMBs needing comprehensive security without hiring a full in-house team. |
| Proactive Defense | Focuses on preventing attacks through continuous patch and vulnerability management. | Organizations handling sensitive data that require minimized risk exposure. |
| Personalized Support | Offers tailored solutions and local support, moving beyond the typical vendor-client relationship. | Businesses seeking a strategic partner to align security with growth and compliance objectives. |
This service is best for businesses that recognize cybersecurity is more than just software; it's a continuous operational process. If your organization wants to offload the daily burden of threat monitoring, patch management, and incident response, this bundled solution is a powerful choice. You can discover more about the benefits of a managed approach by reading about why San Antonio businesses need managed cybersecurity services.
- Website: defenditservices.com/cybersecurity-services
- Best For: SMBs and regulated organizations seeking a fully managed, comprehensive security partnership.
- Pricing: Custom quote-based, as it is a tailored service bundle.
2. CrowdStrike Falcon
CrowdStrike Falcon earns its high ranking by delivering one of the most powerful and accessible endpoint security software solutions on the market. Its cloud-native platform was built from the ground up for modern threat detection, offering a single, lightweight agent that deploys in minutes without requiring a system reboot. This makes initial setup and ongoing management remarkably efficient, even for teams with limited IT resources.
The platform's standout feature is its transparency. Unlike many competitors that hide pricing behind sales calls, CrowdStrike offers clear, per-endpoint per-year pricing directly on its website, with options to start a free trial or buy directly. This simplifies the procurement process for businesses of all sizes, from small teams to large enterprises. Its consistent high performance in independent tests like the MITRE ATT&CK evaluations provides third-party validation of its effectiveness.
Platform Analysis
CrowdStrike’s unified console provides visibility across all endpoints, consolidating next-generation antivirus (NGAV), endpoint detection and response (EDR), and even managed threat hunting (Falcon Complete) into one interface. This integrated approach is ideal for regulated industries like healthcare and finance that require robust, auditable security controls. However, to access the most advanced features like identity protection or extended data retention, you must opt for higher-priced bundles or purchase add-ons, which can increase the total cost of ownership.
- Best For: SMBs and enterprises needing a scalable, high-performance EDR/XDR solution with transparent pricing and rapid deployment.
- Pros: Public per-endpoint pricing, consistently strong independent test results, single lightweight agent.
- Cons: Advanced features and longer data retention are tied to more expensive tiers or add-ons.
Website: https://www.crowdstrike.com/en-us/products/
3. Microsoft Defender for Endpoint/Business
Microsoft has transformed its native security tools into a formidable endpoint security software contender with Defender for Endpoint and its SMB-focused counterpart, Defender for Business. Its greatest strength lies in its seamless integration with the Microsoft ecosystem, offering unified management for Windows, macOS, Linux, and mobile devices directly within the Microsoft 365 Defender portal. This native connection provides unparalleled visibility and control for organizations already invested in Microsoft’s cloud services.
The platform’s value proposition is especially compelling for small to midsize businesses. Defender for Business, often included in Microsoft 365 Business Premium, delivers enterprise-grade features like automated investigation and response at an extremely competitive price point. To fully appreciate the scope of Microsoft's endpoint protection, it's beneficial to also understand the native security features and capabilities inherent in the Windows operating system itself, such as by examining understanding the differences between Windows 11 Home and Pro. This built-in advantage simplifies deployment and reduces the learning curve for IT teams.
Platform Analysis
Microsoft Defender’s unified security console simplifies policy management, threat hunting, and vulnerability assessments across the entire device landscape. Its automated attack disruption capabilities can contain threats in progress without requiring manual intervention, a significant advantage for lean security teams. While the platform is powerful, accessing the most advanced enterprise features, like deeper forensic data, requires higher-tier licenses such as E5. Additionally, organizations with a minimal Microsoft footprint may find the initial configuration and policy tuning for non-Windows endpoints requires more effort compared to platform-agnostic solutions.
- Best For: SMBs and enterprises heavily invested in the Microsoft 365 ecosystem seeking a cost-effective, natively integrated security solution.
- Pros: Very cost-effective for Microsoft 365 tenants, mature automation reduces manual triage, deep integration with Windows.
- Cons: Some enterprise features limited to P2/E5 licenses, non-Microsoft environments may need extra tuning.
Website: https://www.microsoft.com/en-us/security/business/endpoint-security/microsoft-defender-business/
4. SentinelOne Singularity
SentinelOne Singularity secures its spot by delivering an AI-powered, autonomous platform that excels in prevention, detection, and response. Its core strength lies in its ability to operate effectively both online and offline, using patented Storyline technology to contextualize threats and reverse malicious actions with a one-click remediation and rollback feature. This is a game-changer for recovering from ransomware attacks, restoring systems to their pre-infected state almost instantly.
Like some top competitors, SentinelOne embraces pricing transparency by publishing its per-endpoint annual costs directly on its website. This approach simplifies procurement for SMBs and mid-market companies that need predictable budgeting without lengthy sales negotiations. The platform also offers strong feature parity across Windows, macOS, and Linux, ensuring consistent protection in diverse IT environments, which is a key consideration for many organizations looking for the best endpoint security software.
Platform Analysis
The Singularity XDR platform unifies endpoint protection (EPP), EDR, and cloud security into a single console with one agent. Its tiered packages (Singularity Core, Control, and Complete) allow businesses to select the right level of functionality, from foundational NGAV to full-featured XDR with extended data retention. However, while the published pricing is a major plus, accessing the most advanced capabilities or adding managed detection and response (MDR) services comes at a significant premium, and larger enterprise deployments often necessitate engaging with a third-party partner.
- Best For: SMBs and mid-market companies needing powerful autonomous protection with transparent pricing and strong multi-OS support.
- Pros: Published per-endpoint pricing, powerful rollback and remediation capabilities, effective offline protection.
- Cons: Higher-end tiers and MDR services can be expensive, and partner engagement is often required for larger deployments.
Website: https://www.sentinelone.com/platform-packages/
5. Palo Alto Networks Cortex XDR
Palo Alto Networks Cortex XDR stands out by extending endpoint security into a truly unified platform that integrates network, cloud, and third-party data. It moves beyond traditional EDR by applying AI and machine learning analytics across these combined datasets, enabling security teams to detect sophisticated, multi-stage attacks that isolated tools might miss. Its approach is ideal for mature security operations that need to consolidate telemetry and streamline investigations.
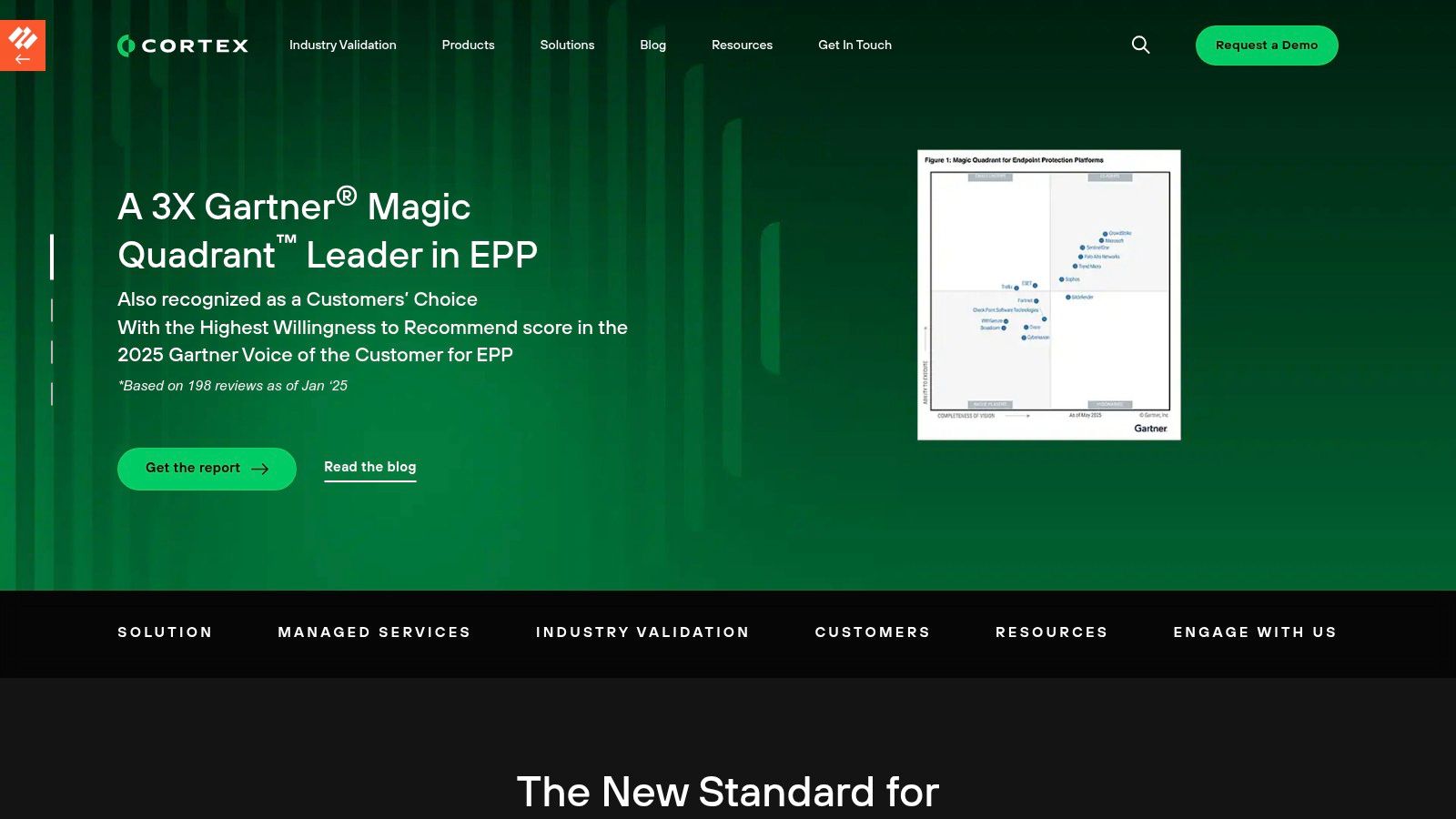
The platform is designed for enterprise environments where comprehensive visibility is non-negotiable. Instead of public pricing, Palo Alto focuses on a sales-led engagement, offering extensive resources like hands-on workshops and test-drive programs to demonstrate its value. This high-touch model allows for tailored deployments, a necessity for complex organizations in regulated sectors like finance and healthcare. The integration with Unit 42 threat intelligence and managed detection and response (MDR) services provides a clear path for organizations to augment their internal security teams.
Platform Analysis
Cortex XDR’s strength lies in its ability to stitch together disparate security events into a single, coherent incident view, significantly reducing alert fatigue and investigation times. The single-agent architecture covers prevention, detection, and response across workstations, servers, and cloud workloads. While this depth is a major advantage for large enterprises, its administrative complexity and sales-gated procurement process may present a hurdle for smaller teams or those accustomed to self-service models. The platform truly shines in environments already invested in the Palo Alto Networks ecosystem.
- Best For: Large enterprises and organizations with mature security operations seeking to unify endpoint, network, and cloud data for advanced threat detection.
- Pros: Enterprise-grade depth with strong analyst recognition, rich demo and test-drive programs, broad XDR correlations beyond endpoints.
- Cons: Pricing not publicly listed; sales-led procurement, admin complexity may be higher for small teams.
Website: https://www.paloaltonetworks.com/cortex/cortex-xdr
6. Sophos Endpoint (formerly Intercept X)
Sophos Endpoint secures its spot by combining powerful, AI-driven threat protection with an exceptionally user-friendly management experience. Its strength lies in making enterprise-grade security accessible through the Sophos Central cloud console, which unifies management across endpoints, servers, firewalls, and mobile devices. This integrated approach simplifies security operations, allowing smaller IT teams to manage a complex threat landscape without needing multiple disjointed tools.
The platform is renowned for its anti-ransomware technology, CryptoGuard, which can roll back malicious file encryption without data loss. Sophos also provides a clear upgrade path from prevention to response. Businesses can start with foundational endpoint protection and easily add on Endpoint Detection and Response (EDR) or even a 24/7 Managed Detection and Response (MDR) service, all within the same ecosystem. While you need to contact a sales rep or partner for pricing, the website offers a free trial to test the software firsthand.
Platform Analysis
Sophos Endpoint is a top contender for the best endpoint security software due to its layered defense model, which includes deep learning AI for detecting unknown malware and anti-exploit techniques to stop fileless attacks. This makes it a strong choice for regulated industries like healthcare and finance that face sophisticated threats. The platform's single-console management is a significant advantage for organizations needing visibility and control without a steep learning curve. The main drawback is the lack of public pricing and the fact that its most powerful capabilities, like EDR and MDR, are sold as separate add-ons or higher-tier licenses.
- Best For: SMBs and mid-market organizations seeking a unified security platform with a clear path to adding managed threat hunting (MDR).
- Pros: High detection efficacy and usability, excellent anti-ransomware features, easy on-ramp to MDR without platform switching.
- Cons: No public list pricing; requires a quote or partner contact, some features require higher SKUs or add-ons.
Website: https://www.sophos.com/en-us/products/endpoint-antivirus
7. Bitdefender GravityZone Business Security
Bitdefender GravityZone earns its spot by offering a powerful, layered security platform that is particularly accessible to small and midsize businesses. Known for its industry-leading prevention capabilities, it combines machine learning-based antivirus with endpoint detection and response (EDR) in a single, manageable solution. The platform’s strength lies in its broad OS compatibility and its straightforward cloud-based console, which simplifies deployment and policy management across diverse environments.
What sets Bitdefender apart is its go-to-market strategy for business clients. While direct purchases are possible, the company often routes prospective customers through its extensive partner network, including major US resellers like CDW, SHI, and specialized managed service providers. This approach frequently leads to competitive volume-based pricing and discounted SKUs that aren't available directly, making it a cost-effective choice. Many businesses choose to procure and manage Bitdefender through an IT partner, which simplifies implementation and provides expert support.
Platform Analysis
The GravityZone console provides a centralized view of all protected endpoints, with add-on modules for patch management and full-disk encryption available to strengthen security posture. This modularity allows organizations to tailor their protection without paying for unneeded features. However, the reliance on bundles and add-ons means that critical capabilities are not always included in the base package, requiring careful evaluation of license tiers. The low-footprint agent ensures minimal impact on system performance, a key consideration for resource-constrained environments.
- Best For: SMBs and mid-market companies seeking a top-rated prevention engine with flexible, reseller-driven pricing options.
- Pros: Frequently discounted volume SKUs available, straightforward cloud deployment and free trials.
- Cons: Official site often routes buyers to partners for pricing, feature availability varies by bundle and add-ons.
Website: https://www.bitdefender.com/en-us/business/smb-products/business-security
8. Trend Micro Apex One as a Service
Trend Micro Apex One as a Service offers a mature and reliable endpoint security software solution delivered via the cloud. It combines next-generation antivirus (NGAV) with advanced behavioral analysis and machine learning, all managed through a single, lightweight agent. This SaaS approach simplifies deployment and management for IT teams, ensuring consistent protection across diverse environments without the need for on-premises hardware.
One of its key differentiators is its availability through major U.S. resellers like CDW, which provides competitive, transparent SKU-based pricing. This model allows businesses to purchase licenses directly through established procurement channels, often at volume-based discounts. The platform’s stability and extensive support network make it a dependable choice for organizations that value proven performance and straightforward purchasing processes.
Platform Analysis
Apex One’s cloud-hosted console provides centralized control over endpoint policies, threat detection, and response actions. The core offering is strong, but organizations seeking advanced capabilities like extended detection and response (XDR) will need to purchase specific SKUs or add-ons. This tiered approach gives businesses flexibility, allowing them to start with essential protection and scale up to more comprehensive threat analytics as their security needs evolve. While pricing varies by reseller and license volume, the widespread availability ensures competitive quotes are easy to obtain.
- Best For: Businesses of all sizes that prefer purchasing through established IT resellers and require a stable, cloud-managed endpoint solution.
- Pros: Available from multiple authorized U.S. sellers with competitive pricing, stable and mature SaaS operations with strong support.
- Cons: Pricing varies by SKU and reseller, advanced XDR analytics often require add-on licenses.
9. VMware Carbon Black Cloud
VMware Carbon Black Cloud establishes its place as a leader in endpoint security software by focusing on deep behavioral analytics and continuous event recording. Its cloud-native platform uses a single lightweight sensor to capture unfiltered endpoint data, giving security teams a rich source for threat hunting and incident response. This granular visibility is crucial for identifying sophisticated attacks that might otherwise bypass traditional signature-based defenses.
Unlike vendors with direct-to-consumer sales models, Carbon Black is primarily sold through a robust network of value-added resellers (VARs) and partners like CDW. This channel-focused approach ensures that businesses receive expert guidance on deployment, configuration, and integration. It makes the solution particularly accessible for organizations that prefer to purchase technology as part of a broader IT strategy from a trusted supplier.
Platform Analysis
The Carbon Black Cloud console offers a unified view of endpoints, workloads, and containers, integrating next-gen antivirus (NGAV), endpoint detection and response (EDR), and managed detection. Its powerful "Live Response" feature provides security analysts with direct remote access to compromised endpoints for real-time investigation and remediation. While this level of forensic capability is a significant advantage, the platform’s go-to-market strategy means pricing is not transparent; obtaining a quote requires engaging a partner. Furthermore, advanced features and extended data retention are often tied to separate bundles or add-ons, which can complicate the procurement process and increase overall costs.
- Best For: Organizations that purchase through IT partners and require deep forensic visibility for incident response and threat hunting.
- Pros: Deep behavioral telemetry and forensic capabilities, widely supported by major US VARs, single sensor for endpoint and workload.
- Cons: Limited public list pricing requires partner quotes, additional bundles and retention options can increase cost.
10. ESET PROTECT Platform
ESET PROTECT secures its spot by offering enterprise-grade endpoint protection that remains remarkably lightweight and accessible for small to midsize businesses. It delivers a comprehensive security suite managed from a single cloud-based or on-premises console, covering everything from next-generation antivirus (NGAV) to advanced threat defense and full disk encryption. This centralized approach simplifies administration, making it an excellent choice for teams that need powerful security without a steep learning curve or significant system performance impact.
The platform's flexibility is a major advantage, allowing businesses to purchase licenses directly through the ESET website or from a wide network of U.S. resellers like SHI and Newegg. This gives buyers multiple procurement options and the ability to find competitive pricing. ESET's protection tiers are clearly defined, enabling companies to select the exact feature set they need, whether it's basic endpoint protection, cloud application security, or a fully managed detection and response (MDR) service.
Platform Analysis
The ESET PROTECT console provides unified management for a wide range of security layers, including mobile device management (MDM), patch management, and server security. This integration is particularly valuable for businesses in regulated sectors like healthcare or finance that need to demonstrate comprehensive control over all network endpoints. While the core product is robust, features like vulnerability scanning and advanced threat hunting are available in higher-priced bundles or as add-ons, which can impact the final cost for organizations needing the most advanced capabilities.
- Best For: SMBs and mid-market companies seeking a lightweight, effective, and scalable endpoint solution with flexible purchasing options.
- Pros: Very lightweight on system resources, SMB-friendly bundles with multi-year discounts, broad reseller availability.
- Cons: Online selector starts at 5 devices; smaller buyers rely on partners, pricing presentation varies across reseller sites and tiers.
Website: https://www.eset.com/us/business/enterprise/
11. AWS Marketplace – Endpoint Security/EDR category
For organizations deeply integrated into the Amazon Web Services ecosystem, the AWS Marketplace offers a streamlined, centralized approach to procuring the best endpoint security software. It isn't a single product but a curated catalog of top-tier EDR, XDR, and MDR solutions from leading vendors like CrowdStrike, SentinelOne, and Carbon Black. This model allows businesses to consolidate billing through their existing AWS account, simplifying vendor management and budget approvals.
The platform’s key advantage is its integration with AWS services and billing. Companies can leverage one-click trials, deploy agents using pre-configured AMIs, and negotiate private offers directly with vendors. This procurement pathway is particularly popular among US-based companies that have standardized their IT infrastructure on AWS, as it eliminates the need to manage separate contracts and payment schedules. The marketplace transforms a complex purchasing process into a more manageable, cloud-native experience.
Platform Analysis
AWS Marketplace simplifies the discovery and deployment of endpoint security solutions by presenting them in a familiar, trusted environment. Users can compare offerings, read reviews, and often deploy trial versions with minimal friction. This is especially useful for teams that need to quickly test and validate a solution's compatibility with their AWS workloads. However, pricing transparency can be inconsistent; while some vendors offer clear per-endpoint costs, many listings still require direct contact with the seller for a custom quote, which can slow down the evaluation process.
- Best For: Companies already using AWS who want to simplify procurement and consolidate security billing with their cloud spend.
- Pros: Streamlined vendor management and budgeting, fast trial and deployment options, access to private offers.
- Cons: Not all vendors provide public per-endpoint pricing, requiring contact with the seller for a quote.
Website: https://aws.amazon.com/marketplace/solutions/security/endpoint-security
12. CDW (US enterprise/SMB reseller marketplace)
CDW earns its spot on this list not as a software developer, but as a strategic procurement platform for some of the best endpoint security software available. It functions as a massive IT reseller, giving businesses a centralized marketplace to compare, purchase, and manage licenses from leading vendors like Trend Micro, Bitdefender, Symantec, and ESET. This approach is invaluable for teams that want to evaluate multiple solutions side-by-side without engaging numerous sales representatives.
The platform’s primary advantage is its pricing transparency and procurement efficiency. CDW displays live, SKU-level pricing for new licenses and renewals, including options for government, academic, and non-profit organizations. It simplifies budget planning and supports volume-based discounts, making it a powerful tool for organizations of any size. For businesses that see cybersecurity as a cornerstone of their growth strategy, using a platform like CDW to manage vendor relationships and renewals is a significant operational advantage. You can learn more about the importance of cybersecurity for growing businesses and how centralized procurement fits in.
Platform Analysis
CDW provides more than just a catalog; it offers a comprehensive procurement ecosystem. Features like contract pricing, net terms, and integration with internal procurement systems streamline the entire purchasing lifecycle. US-based support, implementation services, and renewal management are also available, providing end-to-end assistance. The main challenge is navigating the sheer volume of options. Correctly mapping the features of different vendor bundles to your organization’s specific needs requires careful research and due diligence on the platform.
- Best For: IT departments and procurement teams wanting a single source to compare, purchase, and manage licenses from multiple endpoint security vendors.
- Pros: Transparent SKU-level pricing across many vendors, facilitates multi-vendor comparisons and volume discounts, offers procurement system integration.
- Cons: Some SKUs are limited to specific segments (e.g., academic/public sector), feature mapping across vendor bundles can require diligence.
Website: https://www.cdw.com/
Top 12 Endpoint Security Software Comparison
| Solution | Core Features/Characteristics | User Experience / Quality ★★★★☆ | Value Proposition 💰 | Target Audience 👥 | Unique Selling Points ✨ | Price Points 💰 |
|---|---|---|---|---|---|---|
| Defend IT Services Cybersecurity | Managed SOC (cloud, endpoints, network), MDM, Patch Management | ★★★★☆ Proactive, local support & tailored service | 🏆 Veteran-owned, compliance-focused | SMBs to large businesses | Hands-on support, customizable, rapid incident response | Moderate to premium, customizable |
| CrowdStrike Falcon | NGAV, EDR/XDR single agent, AI behavioral detection | ★★★★★ Strong prevention, fast deployment | Clear per-endpoint pricing | SMBs to enterprises | Public transparent pricing, buy-now bundles | Transparent per-endpoint pricing |
| Microsoft Defender for Endpoint | NGAV + EDR, automated remediation, cross-platform Microsoft 365 | ★★★★☆ Cost-effective, seamless M365 integration | Great for Microsoft 365 tenants | SMBs with Microsoft 365 | Native integration, automation | Low cost for M365 customers |
| SentinelOne Singularity | AI-driven EPP/EDR with rollback, cloud/workload protection | ★★★★☆ Autonomous prevention, offline protection | Transparent annual per-endpoint pricing | SMBs to mid-market | Rollback capability, strong macOS/Linux parity | Published pricing, tiers |
| Palo Alto Cortex XDR | Unified agent with AI analytics, XDR, Unit 42 MDR services | ★★★★★ Enterprise-grade, analyst recognized | Rich demos & workshops | Enterprise customers | Broad XDR with MDR, AI-driven analytics | Sales-led pricing, premium |
| Sophos Endpoint | NGAV, ransomware protection, cloud-managed with MDR add-ons | ★★★★☆ High detection, easy MDR on-ramp | Guided demos and free trials | SMBs and enterprises | CryptoGuard ransomware defense, cloud console | Quote-based pricing |
| Bitdefender GravityZone | NGAV, EDR, patch management, disk encryption | ★★★★☆ Frequent discounts, cloud deployment | Volume licensing via resellers | SMBs and mid-market | Competitive pricing via US resellers | Competitive, reseller pricing |
| Trend Micro Apex One | NGAV with behavior analysis, optional XDR | ★★★★☆ Mature SaaS with multiple authorized sellers | Scalable licensing via US resellers | SMBs and enterprises | Cloud-hosted, XGen machine learning | Variable by SKU and volume |
| VMware Carbon Black Cloud | NGAV, EDR/XDR, workload protection, forensic analytics | ★★★★☆ Deep telemetry, forensic capabilities | Supported by major US VARs | SMB to enterprise | Continuous event capture, Live Response | Partner quote pricing |
| ESET PROTECT Platform | NGAV, disk encryption, mobile/cloud security, MDR | ★★★★☆ Lightweight, SMB-friendly bundles | Flexible device licensing | SMBs | Lightweight agent, multi-year discounts | Tiered from 5+ devices |
| AWS Marketplace EDR | Catalog of EDR/MDR solutions, private offers, AWS billing | ★★★★☆ Simplifies vendor mgmt, fast deployment | Consolidated AWS billing | US companies on AWS | One-click trials, private offers | Varies by vendor/bundle |
| CDW Reseller Marketplace | Wide endpoint security catalog, contract pricing, US-based support | ★★★★☆ Transparent SKU pricing, volume discounts | Multi-vendor marketplace | US SMBs and enterprises | Extensive contract and procurement options | Transparent with volume deals |
Making the Final Decision: Secure Your Endpoints, Secure Your Future
Navigating the landscape of endpoint security can feel overwhelming. We've explored a wide array of powerful solutions, from the AI-driven threat hunting of CrowdStrike Falcon and SentinelOne Singularity to the comprehensive ecosystem integration of Microsoft Defender for Endpoint. Each tool offers a unique blend of features, strengths, and ideal use cases designed to address the sophisticated threats facing modern businesses.
The core takeaway is clear: traditional antivirus software is no longer sufficient. Today's threats are dynamic, multi-faceted, and capable of bypassing simple signature-based defenses. The best endpoint security software for your organization will be a modern Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) platform. These solutions provide the visibility, behavioral analysis, and rapid response capabilities necessary to stop advanced attacks like ransomware and fileless malware in their tracks.
From Selection to Successful Implementation
Choosing a tool is only the first step. The true measure of your security posture lies in how effectively that tool is deployed, configured, and managed. Your final decision should not be based on a feature checklist alone, but on a holistic assessment of your organization's unique context.
Before you sign a contract, consider these critical factors:
- Your Internal Expertise: Do you have a dedicated IT security team with the skills to manage a complex platform like Palo Alto Networks Cortex XDR? Or would a more user-friendly, automated solution like Sophos Endpoint be a better fit? Be honest about your team's bandwidth and capabilities. An unmanaged EDR is a security liability, not an asset.
- Business and Compliance Needs: For organizations in San Antonio handling sensitive data under regulations like HIPAA or PCI DSS, the choice of software is paramount. Your solution must not only provide top-tier protection but also offer the logging, reporting, and data residency features required to maintain compliance. Platforms like Microsoft Defender and VMware Carbon Black are often favored in these regulated environments.
- Scalability and Future Growth: Your endpoint security solution should grow with your business. If you are planning a cloud migration or expanding to multiple locations, you need a cloud-native platform that can scale effortlessly without requiring significant on-premises infrastructure. This is where solutions like Trend Micro Apex One and the offerings on the AWS Marketplace truly shine.
- Total Cost of Ownership (TCO): Look beyond the per-seat license fee. Factor in the costs of implementation, training, and ongoing management. A cheaper tool that requires significant human hours to operate may ultimately be more expensive than a pricier, more automated platform or a fully managed service.
The Human Element: Technology's Critical Partner
Ultimately, even the most advanced AI-powered security platform is only as effective as the people behind it. Alerts must be investigated, threats must be triaged, and incidents require a coordinated response. This is where many small and midsize businesses face their biggest challenge. Lacking a 24/7 Security Operations Center (SOC), they struggle to keep up with the constant stream of alerts, leading to security gaps and a high risk of alert fatigue.
This is why partnering with a Managed Security Service Provider (MSSP) is often the most strategic and cost-effective path forward. An MSSP provides the best of both worlds: access to enterprise-grade technology and the dedicated human expertise needed to manage it around the clock. Instead of just buying software, you are investing in a comprehensive security outcome, ensuring that threats are not just detected but are fully remediated by seasoned professionals. This frees your internal team to focus on core business objectives, confident that your digital assets are secure.
Ready to move from selecting a tool to implementing a complete security strategy? The experts at Defend IT Services leverage the industry's best endpoint security software and combine it with 24/7 monitoring and response to protect businesses across San Antonio. Contact us for a consultation and let us build a security posture that protects your present and secures your future. Defend IT Services
Article created using Outrank

